Category: AI in news
The trojan deployed on the system has a wide range of data theft capabilities. It searches for specific directories inside the Opera, Chrome, Brave, Vivaldi, Yandex and Edge browsers and extracts authentication cookies, autofill information, browsing history, bookmarks, credit card information and login credentials. The trojan also attempts to steal files associated with cryptocurrency wallets,…
Read MoreIn the early days of the pandemic, organizations relied on virtual private networks (VPNs) to link remote employees to their networks. However, legacy VPNs don’t provide the most efficient way to connect to network assets. And now that we’re fully in the age of the hybrid workforce, organizations are looking for a better and more comprehensive approach…
Read MoreIf you hear the term “microbranch,” you probably picture a small banking location with a handful of ATMs. For many years, this term was specific to the financial industry, but as remote work and internet-connected devices have grown more common, the definition has evolved to include any small remote office associated with a larger corporation.…
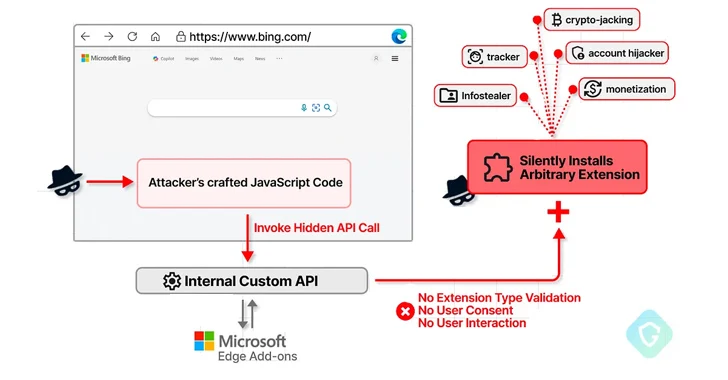
Read MoreMar 27, 2024NewsroomVulnerability / API Security A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users’ systems and carry out malicious actions. “This flaw could have allowed an attacker to exploit a private API, initially intended for marketing purposes, to covertly install additional browser extensions…
Read More“With Verify API, businesses can customize the verification and authentication experience by market needs, customer preferences, or business priorities with peace of mind—and with automatic multichannel fallback,” the company said in a press release. Verify API also allows custom routing to help customers build routing rules for tailored delivery across all channels and markets. Arms…
Read MoreMar 27, 2024NewsroomVulnerability / Data Security Cybersecurity researchers are warning that threat actors are actively exploiting a “disputed” and unpatched vulnerability in an open-source artificial intelligence (AI) platform called Anyscale Ray to hijack computing power for illicit cryptocurrency mining. “This vulnerability allows attackers to take over the companies’ computing power and leak sensitive data,” Oligo…
Read MoreSecurity Vulnerability in Saflok’s RFID-Based Keycard Locks It’s pretty devastating: Today, Ian Carroll, Lennert Wouters, and a team of other security researchers are revealing a hotel keycard hacking technique they call Unsaflok. The technique is a collection of security vulnerabilities that would allow a hacker to almost instantly open several models of Saflok-brand RFID-based keycard…
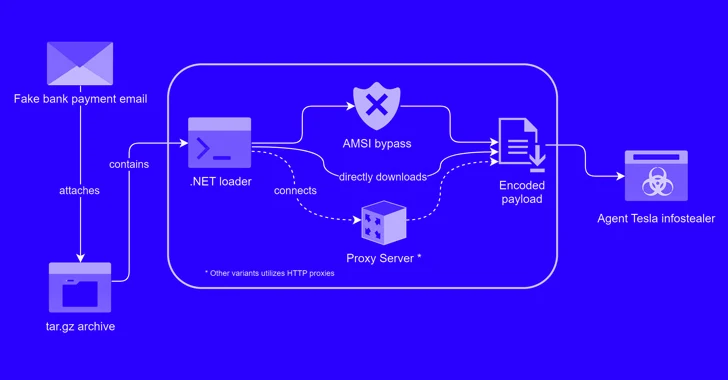
Read MoreMar 27, 2024NewsroomVulnerability / Cybercrime A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades as a bank payment notification, urging the user to…
Read MoreSecurity teams can assess vendors’ policies on data handling, incident response, data regionalization, and privacy. They can evaluate a service-level agreement for things like availability and security metrics. They can also scrutinize the vendor’s security culture and practices, including third-party audits, and confirm features like multifactor authentication and data recovery. Ideally, companies should do real-time security…
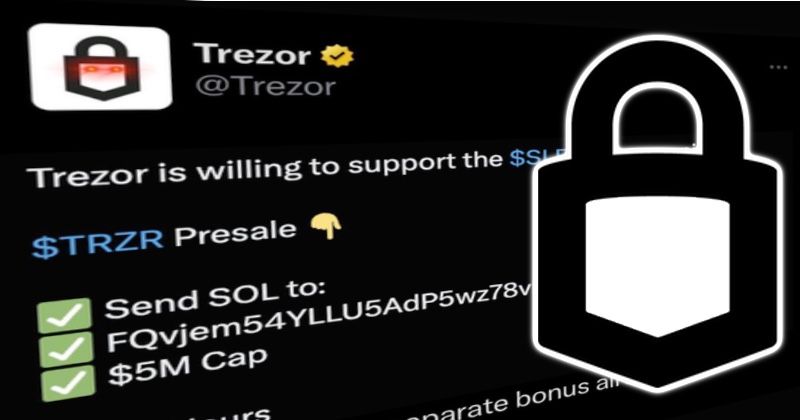
Read MoreThis isn’t the kind of thing you expect to see posted on the official Twitter account of Trezor, the well-known cryptocurrency wallet manufacturer. It’s a fairly blatant attempt to dupe unwary cryptocurrency fans into transfering digital currency into the wallet of a scammer. And whoever hacked Trezor’s Twitter account didn’t limit themselves to just posting…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm