Category: AI in news
Step 3: Threat profiling This phase helps to identify and prioritize threats and understand how they can manifest. Threat profiling starts with the identification of potentially relevant threats through discussion with key stakeholders and analyzing available sources of threat intelligence (e.g., an internal threat intelligence team or external commercial feeds). Once the threat landscape is…
Read MoreTwo China-linked advanced persistent threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a cyber espionage campaign over the past three months. This includes the threat actor known as Mustang Panda, which has been recently linked to cyber attacks against Myanmar…
Read MoreSimilarities with older APT29 backdoors While Zscaler did not link the January attack to any APT group, the researchers believed at the time it was the work of a nation-state threat actor looking to exploit diplomatic relations, which is typical of APT29 targeting. Going further, Mandiant has not established clear similarities in design and code…
Read MoreAs cloud adoption rates continue to rise, security leaders are beginning to rethink the way they approach cybersecurity. What once worked for on-premises networks is no longer sufficient for complex, interconnected hybrid and multicloud environments. In addition to deploying security best practices throughout the full application lifecycle, CISOs also need to be able to obtain…
Read MoreMar 26, 2024NewsroomIndustrial Espionage / Threat Intelligence Threat hunters have identified a suspicious package in the NuGet package manager that’s likely designed to target developers working with tools made by a Chinese firm that specializes in industrial- and digital equipment manufacturing. The package in question is SqzrFramework480, which ReversingLabs said was first published on January…
Read MoreAI has the power to transform security operations, enabling organizations to defeat cyberattacks at machine speed and drive innovation and efficiency in threat detection, hunting, and incident response. It also has major implications for the ongoing global cybersecurity shortage. Roughly 4 million cybersecurity professionals are needed worldwide. AI can help overcome this gap by automating…
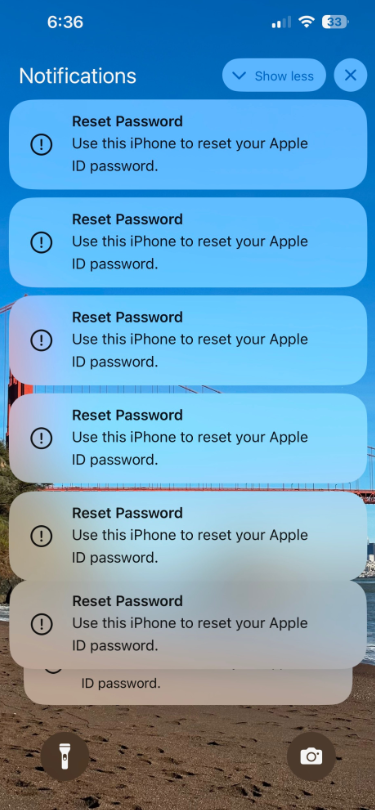
Read MoreSeveral Apple customers recently reported being targeted in elaborate phishing attacks that involve what appears to be a bug in Apple’s password reset feature. In this scenario, a target’s Apple devices are forced to display dozens of system-level prompts that prevent the devices from being used until the recipient responds “Allow” or “Don’t Allow” to…
Read MoreAs organizations expand and increasingly invest in more cloud applications and services, their cloud footprint grows and often becomes more complex. That’s why it is critically important to regularly reevaluate the security of those cloud assets to ensure that everything is secure, and the required processes and procedures are being upheld. The growth in cloud…
Read MoreThe U.S. Department of Justice (DoJ) on Monday unsealed indictments against seven Chinese nationals for their involvement in a hacking group that targeted U.S. and foreign critics, journalists, businesses, and political officials for about 14 years. The defendants include Ni Gaobin (倪高彬), Weng Ming (翁明), Cheng Feng (程锋), Peng Yaowen (彭耀文), Sun Xiaohui (孙小辉), Xiong…
Read MoreOn Secure Voting Systems Andrew Appel shepherded a public comment—signed by twenty election cybersecurity experts, including myself—on best practices for ballot marking devices and vote tabulation. It was written for the Pennsylvania legislature, but it’s general in nature. From the executive summary: We believe that no system is perfect, with each having trade-offs. Hand-marked and…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm