Category: AI in news
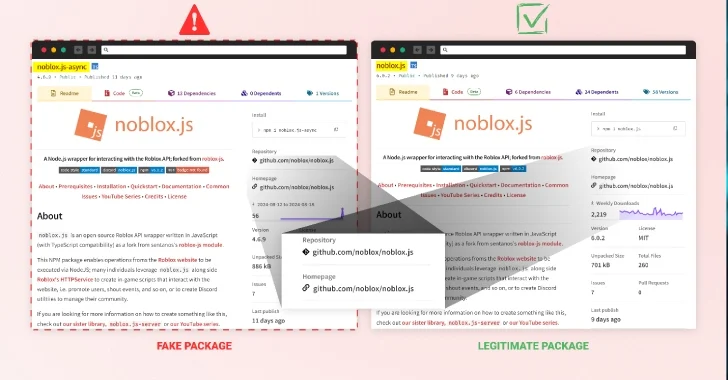
Sep 02, 2024Ravie LakshmananSoftware Security / Malware Roblox developers are the target of a persistent campaign that seeks to compromise systems through bogus npm packages, once again underscoring how threat actors continue to exploit the trust in the open-source ecosystem to deliver malware. “By mimicking the popular ‘noblox.js’ library, attackers have published dozens of packages…
Read MoreAug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the FudModule rootkit. The development is indicative of the persistent efforts made by the nation-state adversary, which had made a…
Read More“You [as a woman] have to have a very thick skin and a spine of steel to last a very long time in this industry,” she said. “Every woman I know who is a leader has the same — very tough skin and a spine of steel.” Women in cybersecurity statistics The ISC2, a nonprofit…
Read MoreFriday Squid Blogging: Economic Fallout from Falklands Halting Squid Fishing Details. Blog moderation policy. Tags: squid Posted on August 30, 2024 at 5:04 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreHowever, there can be clues in the email or on the site. Netcraft said that sometimes threat actors accidentally include large language model (LLM) outputs in the fraudulent emails. For example, a phishing email it encountered, claiming to contain a link to a file transfer of family photos, also included the phrase, “Certainly! Here are…
Read MoreCybersecurity Snapshot: Schools Suffer Heavy Downtime Losses Due To Ransomware, as Banks Grapple with AI Challenges
by nlqip
The cost of ransomware downtime in schools gets pegged at $500K-plus per day. Meanwhile, check out the AI-usage risks threatening banks’ cyber resilience. Plus, Uncle Sam is warning about a dangerous Iran-backed hacking group. And get the latest on AI-system inventories, the APT29 nation-state attacker and digital identity security! Dive into six things that are…
Read MoreIncidentally, the FBI and CISA have released a joint advisory on the Ransomhub Ransomware variant, calling it a formidable service model attracting high-profile affiliates from other prominent variants such as LockBit and ALPHV. “Since its inception in February 2024, RansomHub has encrypted and exfiltrated data from at least 210 victims representing the water and wastewater,…
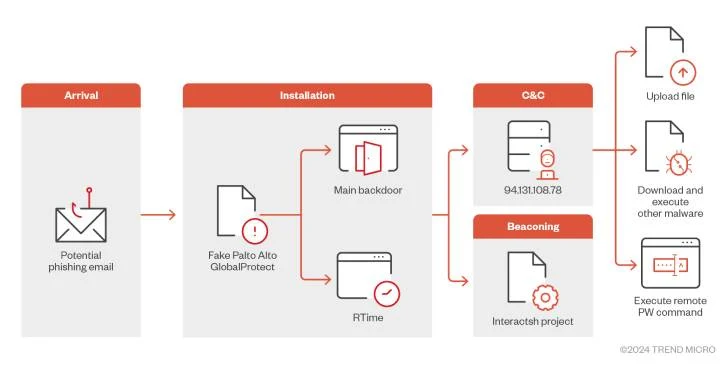
Read MoreAug 30, 2024Ravie LakshmananMalware / Network Security Cybersecurity researchers have disclosed a new campaign that potentially targets users in the Middle East through malware that disguises itself as Palo Alto Networks GlobalProtect virtual private network (VPN) tool. “The malware can execute remote PowerShell commands, download and exfiltrate files, encrypt communications, and bypass sandbox solutions, representing…
Read MoreEmotet first appeared in 2014, but like Zeus, is now a modular program most often used to deliver other forms of malware, with Trickster and Ryuk being two prominent examples. Emotet is so good at what it does that Arne Schoenbohm, head of the German Federal Office for Information Security, calls it the “king of…
Read MoreSANS Institute Unveils Critical Infrastructure Strategy Guide for 2024: A Call to Action for Securing ICS/OT Environments
by nlqip
Aug 30, 2024The Hacker NewsICS Security / OT Security A comprehensive guide authored by Dean Parsons emphasizes the growing need for specialized ICS security measures in the face of rising cyber threats. With a staggering 50% increase in ransomware attacks targeting industrial control systems (ICS) in 2023, the SANS Institute is taking decisive action by…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict