Category: AI in news
From a software perspective, Sovereign SASE supports the same features that are provided as part of Fortinet’s security service edge (SSE) offering, FortiSASE. The difference with Sovereign SASE is how SASE is deployed, Shah said. With Sovereign SASE, customers or partners (including managed security service providers) host the hardware based on Fortinet’s predefined hardware bundles,…
Read MoreThe integrated F5/Intel offering, which is available, will be particularly beneficial for edge applications, such as video analytics and IoT, where low latency and high performance are crucial, wrote Kunal Anand, chief technology officer with F5, in a blog about the technology. “F5 NGINX Plus works as a reverse proxy, offering traffic management and protection…
Read More‘We did a higher percentage of the business through the channel in Q2 than we have during my tenure at any time,’ Citrix channel chief Ethan Fitzsimons tells CRN in an interview. Almost two years after Citrix was taken private and merged with enterprise software vendor Tibco, the virtualization and desktop delivery company is “more…
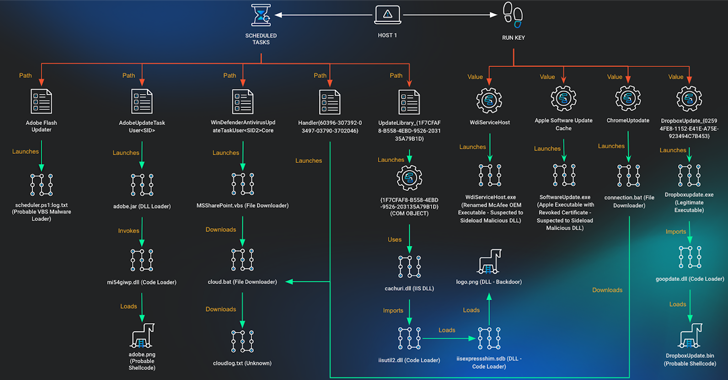
Read MoreDefenders should watch for an archive file named Network Security.zip, which includes an .exe with the Tickler malware, and for a Trojan dropper named sold.dll. Here’s another example of Peach Sandstorm tactics detailed by Microsoft: After hacking into a European defense organization, the gang moved laterally using the Windows SMB (Server Message Block) protocol. This…
Read MoreOther levels of compensation, without RCE, include demonstrating a controlled write or a memory corruption. The baseline for bugs that do not demonstrate such “higher-quality reports” range from US$7,000 to US$25,000. Last year, the total payouts in Google’s bug hunter program were US$10 million dollars, distributed among 632 people from 68 countries. Just over a…
Read MoreAug 29, 2024Ravie LakshmananCyber Espionage / Malware A non-profit supporting Vietnamese human rights has been the target of a multi-year campaign designed to deliver a variety of malware on compromised hosts. Cybersecurity company Huntress attributed the activity to a threat cluster known as APT32, a Vietnamese-aligned hacking crew that’s also known as APT-C-00, Canvas Cyclone…
Read MoreAdm. Grace Hopper’s 1982 NSA Lecture Has Been Published The “long lost lecture” by Adm. Grace Hopper has been published by the NSA. (Note that there are two parts.) It’s a wonderful talk: funny, engaging, wise, prescient. Remember that talk was given in 1982, less than a year before the ARPANET switched to TCP/IP and…
Read MoreImportantly, with its development based in Dubai and St Petersburg, Telegram isn’t an American company. For prosecutors, both inside and outside of the US, that has become an issue. Should the authorities want to grab metadata such as the IP address of a specific user on a social media, messaging or email platform, companies registered…
Read MoreWho doesn’t fancy earning US $2.5 million? That’s the reward that’s on offer from the US Department and State and Secret Service for information leading to the arrest and/or conviction of a Belarusian man who allegedly was a key figure behind the development and distribution of the notorious Angler Exploit Kit. 38-year-old Vladimir Kadariya is…
Read MoreThe goal of the partnership is to ensure Citrix Service Provider partners ‘have the level of coverage, service, technical support, so on and so forth that they need to be effective in their business and maintain flexibility in the model in which they want to consume,’ says Ethan Fitzsimons, Citrix’s channel chief. Citrix, a business…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict