Category: AI in news
Feb 27, 2024NewsroomCloud Security / Threat Intelligence Cybersecurity and intelligence agencies from the Five Eyes nations have released a joint advisory detailing the evolving tactics of the Russian state-sponsored threat actor known as APT29. The hacking outfit, also known as BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard (formerly Nobelium), and The Dukes, is assessed to…
Read MoreCost to join: Annual individual membership, $1,250. FirstBoard.io bills itself as a “curated collective of female tech founders, CXOs, and operating leaders working together to increase female representation on company boards” in a variety of industries, including cybersecurity, cloud, enterprise software, artificial intelligence, robotics, and internet of things. Founded in 2020 by Rita Scroggin, an…
Read MoreA group of attackers targeting Ukraine-affiliated organizations has been delivering malicious payloads hidden within the pixels of image files. Known as steganography, it is just one of many advanced techniques the group uses to evade detection as part of a malware loader known as IDAT. Tracked as UAC-0184 by several security firms, as well as…
Read MoreAlways be wary of opening unsolicited attachments – they might harbour malware. That’s a message that is being strongly underlined once again, following the discovery of a cybercrime campaign that is using the cover of travel service providers. Security researchers at Forcepoint say that they have uncovered evidence that malicious hackers are sending out poisoned…
Read MoreSurprise! The LockBit ransomware group has re-emerged, just days after a high-profile law enforcement operation seized control of its infrastructure and disrupted its operations. “Operation Cronos” saw global agencies around the world work together to seize control of LockBit’s website, where information had been published about ransomware victims and their stolen data, possibly leaving many…
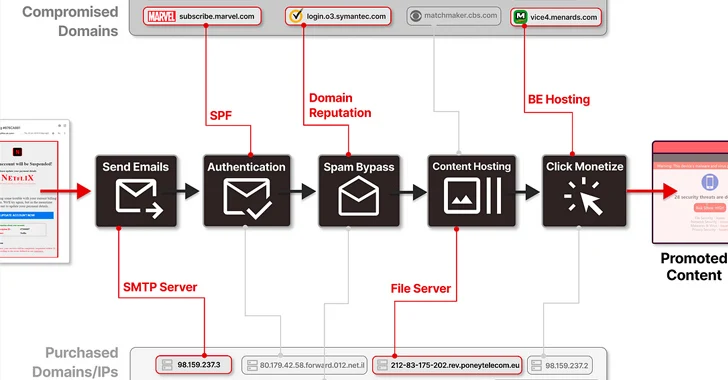
Read MoreMore than 8,000 subdomains belonging to legitimate brands and institutions have been hijacked as part of a sophisticated distribution architecture for spam proliferation and click monetization. Guardio Labs is tracking the coordinated malicious activity, which has been ongoing since at least September 2022, under the name SubdoMailing. The emails range from “counterfeit package delivery alerts…
Read MoreFeb 26, 2024The Hacker NewsSoftware Security / Cryptocurrency A set of fake npm packages discovered on the Node.js repository has been found to share ties with North Korean state-sponsored actors, new findings from Phylum show. The packages are named execution-time-async, data-time-utils, login-time-utils, mongodb-connection-utils, and mongodb-execution-utils. One of the packages in question, execution-time-async, masquerades as its…
Read MoreApple Announces Post-Quantum Encryption Algorithms for iMessage Apple announced PQ3, its post-quantum encryption standard based on the Kyber secure key-encapsulation protocol, one of the post-quantum algorithms selected by NIST in 2022. There’s a lot of detail in the Apple blog post, and more in Douglas Stabila’s security analysis. I am of two minds about this.…
Read More“I didn’t pay much attention to it, because for 5 years of swimming in money I became very lazy,” LockBitSupp said. “At 20:47 I found that the site gives a new error 404 Not Found nginx, tried to enter the server through SSH and could not, the password did not fit, as it turned out…
Read MoreLast year, the Open Worldwide Application Security Project (OWASP) published multiple versions of the “OWASP Top 10 For Large Language Models,” reaching a 1.0 document in August and a 1.1 document in October. These documents not only demonstrate the rapidly evolving nature of Large Language Models, but the evolving ways in which they can be…
Read MoreRecent Posts
- WWT To Buy Softchoice In $1.25B Blockbuster: Here’s What To Know
- The Most Scary, Interesting, and Important Stories of 2024
- Choosing the Right CNAPP: Six Considerations for Mid-Sized Enterprises
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Vulnerability Summary for the Week of December 23, 2024 | CISA