Category: AI in news
Heaven’s above! Scammers are exploiting online funerals, and Lockbit – the “Walmart of Ransomware” – is dismantled in style by cyber cops. All this and more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault. Warning: This podcast may contain nuts, adult themes, and rude…
Read MoreA critical vulnerability patched this week in the ConnectWise ScreenConnect remote desktop software is already being exploited in the wild. Researchers warn that it’s trivial to exploit the flaw, which allows attackers to bypass authentication and gain remote code execution on systems, and proof-of-concept exploits already exist. ScreenConnect is a popular remote support tool with…
Read MoreFeb 21, 2024Newsroom Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and ChromeOS devices that could trick users into joining a malicious clone of a legitimate network or allow an attacker to join a trusted network without a password. The vulnerabilities, tracked as CVE-2023-52160 and CVE-2023-52161, have…
Read More“In terms of phishing, while I believe that the threat remains in the critical category for organizations, because many phishing campaigns seek account credentials as the primary outcome, if cybercriminals have access to valid account credentials via other means (as noted in the report), the need to run a phishing campaign will decline,” said Michael Sampson,…
Read MoreDetails of a Phone Scam First-person account of someone who fell for a scam, that started as a fake Amazon service rep and ended with a fake CIA agent, and lost $50,000 cash. And this is not a naive or stupid person. The details are fascinating. And if you think it couldn’t happen to you,…
Read MoreCybersecurity for Healthcare—Diagnosing the Threat Landscape and Prescribing Solutions for Recovery
by nlqip
On Thanksgiving Day 2023, while many Americans were celebrating, hospitals across the U.S. were doing quite the opposite. Systems were failing. Ambulances were diverted. Care was impaired. Hospitals in three states were hit by a ransomware attack, and in that moment, the real-world repercussions came to light—it wasn’t just computer networks that were brought to…
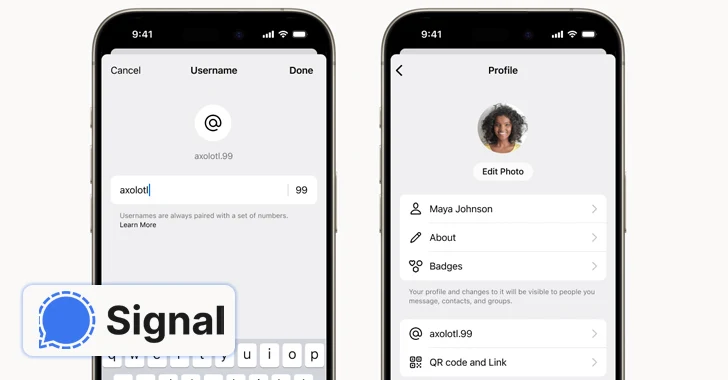
Read MoreFeb 21, 2024NewsroomSecure Communication / Anonymity End-to-end encrypted (E2EE) messaging app Signal said it’s piloting a new feature that allows users to create unique usernames (not to be confused with profile names) and keep the phone numbers away from prying eyes. “If you use Signal, your phone number will no longer be visible to everyone…
Read MoreFeb 21, 2024NewsroomActive Directory / Vulnerability VMware is urging users to uninstall the deprecated Enhanced Authentication Plugin (EAP) following the discovery of a critical security flaw. Tracked as CVE-2024-22245 (CVSS score: 9.6), the vulnerability has been described as an arbitrary authentication relay bug. “A malicious actor could trick a target domain user with EAP installed…
Read MoreFor some internal classified work, the NSA also pushes multiple layers of encryption. Their guidelines for using commercially available software in classified environments frequently encourage using multiple “layers” of independent packages. How much security does hybrid encryption provide? One of the biggest debates is how much security hybridization offers. Much depends on the details and…
Read MoreFeds Seize LockBit Ransomware Websites, Offer Decryption Tools, Troll Affiliates – Krebs on Security
by nlqip
U.S. and U.K. authorities have seized the darknet websites run by LockBit, a prolific and destructive ransomware group that has claimed more than 2,000 victims worldwide and extorted over $120 million in payments. Instead of listing data stolen from ransomware victims who didn’t pay, LockBit’s victim shaming website now offers free recovery tools, as well…
Read More