Category: AI in news
Feb 20, 2024NewsroomDark Web / Cybercrime An international law enforcement operation has led to the seizure of multiple darknet domains operated by LockBit, one of the most prolific ransomware groups, marking the latest in a long list of digital takedowns. While the full extent of the effort, codenamed Operation Cronos, is presently unknown, visiting the…
Read MoreEU Court of Human Rights Rejects Encryption Backdoors The European Court of Human Rights has ruled that breaking end-to-end encryption by adding backdoors violates human rights: Seemingly most critically, the [Russian] government told the ECHR that any intrusion on private lives resulting from decrypting messages was “necessary” to combat terrorism in a democratic society. To…
Read MoreMeta Platforms said it took a series of steps to curtail malicious activity from eight different firms based in Italy, Spain, and the United Arab Emirates (U.A.E.) operating in the surveillance-for-hire industry. The findings are part of its Adversarial Threat Report for the fourth quarter of 2023. The spyware targeted iOS, Android, and Windows devices.…
Read MoreVulnerable webmail servers seem to be a part of the general modus operandi the Russian hackers use for espionage campaigns. Previously in June 2023, another Russian state-sponsored cyber espionage group BlueDelta (aka FancyBear, APT28) was targeting vulnerable Roundcube installations across Ukraine and had also exploited CVE202323397, a critical zero-day vulnerability in Microsoft Outlook in 2022,…
Read MoreFeb 19, 2024NewsroomMalware / Mobile Security The Android banking trojan known as Anatsa has expanded its focus to include Slovakia, Slovenia, and Czechia as part of a new campaign observed in November 2023. “Some of the droppers in the campaign successfully exploited the accessibility service, despite Google Play’s enhanced detection and protection mechanisms,” ThreatFabric said…
Read MoreMicrosoft recently released a security news update that addresses chilling reports that attackers have been able to pivot from a test tenant to the C suite to obtain access to emails being sent and received. In addition, it came to light that HPE’s corporate mailboxes had been accessed using a similar exploit. Both appear to…
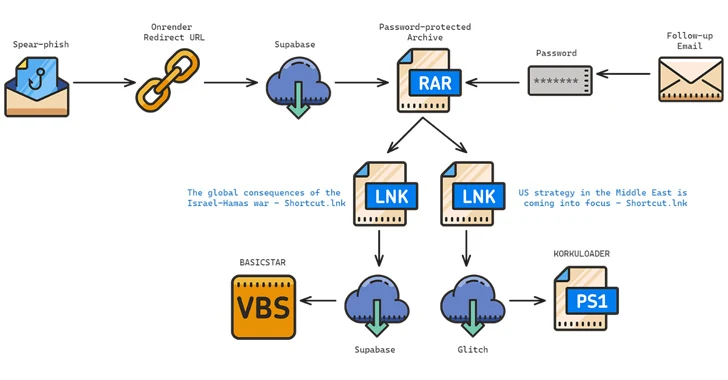
Read MoreFeb 19, 2024NewsroomMalware / Cyber Espionage The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar portal. Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a…
Read MoreFeb 18, 2024NewsroomMalware / Cybercrime A Ukrainian national has pleaded guilty in the U.S. to his role in two different malware schemes, Zeus and IcedID, between May 2009 and February 2021. Vyacheslav Igorevich Penchukov (aka Vyacheslav Igoravich Andreev, father, and tank), 37, was arrested by Swiss authorities in October 2022 and extradited to the U.S.…
Read MoreEfficient communication is a cornerstone of business success. Internally, making sure your team communicates seamlessly helps you avoid friction losses, misunderstandings, delays, and overlaps. Externally, frustration-free customer communication is directly correlated to a positive customer experience and higher satisfaction. However, business communication channels are also a major target for cybercriminals. In recent years, especially since…
Read MoreFriday Squid Blogging: Vegan Squid-Ink Pasta It uses black beans for color and seaweed for flavor. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on February 16, 2024 at 5:04 PM •…
Read More