Category: AI in news
Cloudflare: On February 1, Cloudflare announced it had detected a threat actor on its self-hosted Atlassian server on November 23. Although the primary point of compromise in this incident came through account credentials that Cloudflare failed to rotate after an Okta compromise, the company said the threat actor attempted to gain access to a non-production…
Read MoreFeb 13, 2024NewsroomVulnerability / Email Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a medium-severity security flaw impacting Roundcube email software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The issue, tracked as CVE-2023-43770 (CVSS score: 6.1), relates to a cross-site scripting (XSS) flaw that stems…
Read MoreOver 20 hospitals in Bucharest have reportedly been impacted by a ransomware attack after cybercriminals targeted an IT service provider. As a consequence medical staff have been forced to use pen-and-paper rather than computer systems. Romania’s National Cybersecurity Directorate (DNSC) said in a statement that the attackers encrypted hospital data using the Backmydata ransomware –…
Read MoreAbout Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998. I’m a fellow and lecturer at Harvard’s Kennedy School, a board member of EFF, and the Chief of Security Architecture…
Read MoreA smart helmet for biking and skiing fans sounds like a good idea. If you’re on the slopes or trails, you want to protect your head and stay in touch with your group. Which is why Livall, a popular manufacturer of ski and bike helmets, has presumably developed a “smart” line of products with “walkie-talkie”…
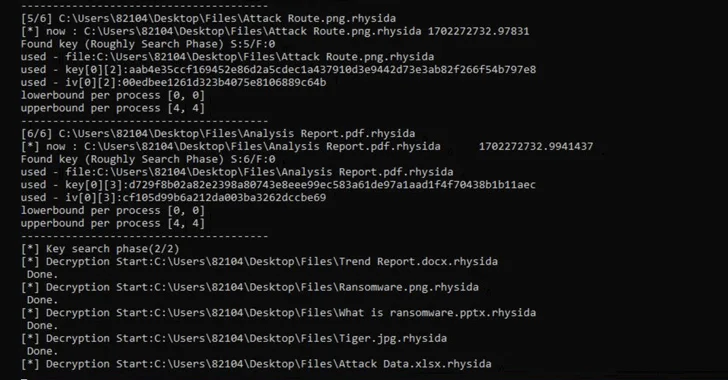
Read MoreFeb 12, 2024NewsroomVulnerability / Data Recovery Cybersecurity researchers have uncovered an “implementation vulnerability” that has made it possible to reconstruct encryption keys and decrypt data locked by Rhysida ransomware. The findings were published last week by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA). “Through a comprehensive analysis…
Read MoreThe idea of “shit left” was to incorporate security earlier in the development phase, but because of the complexity and the nuanced nature of every API, API Security as a market simply ignores the consumer of the API and has not historically provided a means to manage, monitor, and control the data in motion, according…
Read MoreFeb 12, 2024The Hacker NewsCyber Threat / Password Security When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple work for hackers, MFA provides an essential layer of protection against breaches. However, it’s important to remember that MFA isn’t foolproof. It can be bypassed,…
Read MoreThe update will attempt to patch the recovery partition, but here lies the problem: Over the years Microsoft has changed its mind on how big the recovery partition should be and exactly where it should be located. Depending on how old your deployment images are, that is when you first installed your base of Windows…
Read MoreMichael Brown, vice president of technology at Auvik, has it right in my opinion: “On one end of the spectrum, monitoring an employee’s every action provides deep visibility and potentially useful insights, but may violate an employee’s privacy. On the other hand, while a lack of monitoring protects the privacy of employee data, this choice…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA