Category: AI in news
Feb 12, 2024NewsroomOperating System / Technology Microsoft said it’s introducing Sudo for Windows 11 as part of an early preview version to help users execute commands with administrator privileges. “Sudo for Windows is a new way for users to run elevated commands directly from an unelevated console session,” Microsoft Product Manager Jordi Adoumie said. “It…
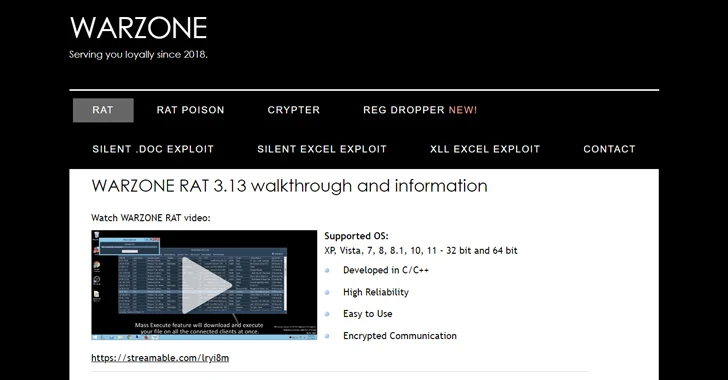
Read MoreFeb 11, 2024NewsroomMalware / Cybercrime The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was used to sell a remote access trojan (RAT) called Warzone RAT. The domains – www.warzone[.]ws and three others – were “used to sell computer malware used by cybercriminals to secretly access and steal data from…
Read MoreFeb 10, 2024NewsroommacOS Malware / Cyber Threat Apple macOS users are the target of a new Rust-based backdoor that has been operating under the radar since November 2023. The backdoor, codenamed RustDoor by Bitdefender, has been found to impersonate an update for Microsoft Visual Studio and target both Intel and Arm architectures. The exact initial…
Read MoreFriday Squid Blogging: A Penguin Named “Squid” Amusing story about a penguin named “Squid.” As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on February 9, 2024 at 5:09 PM • 0 Comments…
Read MoreCisco has fixed three serious cross-site request forgery (CSRF) vulnerabilities in its Expressway Series collaboration gateway and a denial-of-service (DoS) flaw in the ClamAV anti-malware engine. CSRF flaws allow unauthenticated attackers to perform arbitrary actions on vulnerable devices by tricking users to click on a specifically crafted link. The actions execute with the privilege of…
Read MoreNo, Toothbrushes Were Not Used in a Massive DDoS Attack The widely reported story last week that 1.5 million smart toothbrushes were hacked and used in a DDoS attack is false. Near as I can tell, a German reporter talking to someone at Fortinet got it wrong, and then everyone else ran with it without…
Read MoreUntil earlier this week, the support website for networking equipment vendor Juniper Networks was exposing potentially sensitive information tied to customer products, including the exact devices each customer bought, as well as each product’s warranty status, service contracts and serial numbers. Juniper said it has since fixed the problem, and that the inadvertent data exposure…
Read MoreFeb 09, 2024NewsroomMobile Security / Cyber Threat Threat hunters have identified a new variant of Android malware called MoqHao that automatically executes on infected devices without requiring any user interaction. “Typical MoqHao requires users to install and launch the app to get their desired purpose, but this new variant requires no execution,” McAfee Labs said…
Read MoreSSL VPNs are trusted secure connections to private organization networks. A vulnerability like CVE-2024-21762 allows attackers to access and exploit systems on these secure channels. The vulnerability affects FortiOS versions 7.4 (before 7.4.2), 7.2 (before 7.2.6), 7.0 (before 7.0.13), 6.4 (before 6.4.14), 6.2 (before 6.2.15), 6.0 (all versions). While patches have been rolled out with…
Read MoreIntroduction The modern software supply chain represents an ever-evolving threat landscape, with each package added to the manifest introducing new attack vectors. To meet industry requirements, organizations must maintain a fast-paced development process while staying up-to-date with the latest security patches. However, in practice, developers often face a large amount of security work without clear…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA