Category: AI in news
Aug 28, 2024Ravie LakshmananWordPress Security / Website Protection A critical security flaw has been disclosed in the WPML WordPress multilingual plugin that could allow authenticated users to execute arbitrary code remotely under certain circumstances. The vulnerability, tracked as CVE-2024-6386 (CVSS score: 9.9), impacts all versions of the plugin before 4.6.13, which was released on August…
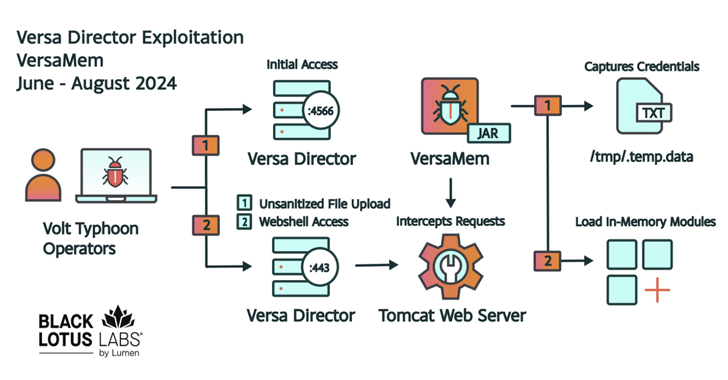
Read MoreState-sponsored Chinese hackers exploited a zero-day vulnerability in Versa Director, a software platform for managing SD-WAN infrastructure used by internet service providers (ISPs) and managed service providers (MSPs). The group, known in the security industry as Volt Typhoon, has targeted US critical infrastructure organizations in the past. “Black Lotus Labs has observed the zero-day exploitation…
Read MoreUnder E2EE, decryption keys are stored only on devices, meaning that governments can’t eavesdrop on what is being said by demanding the keys from service providers. Not surprisingly, governments hate this, leading to the suggestion in countries such as the US and UK that the technology might be outlawed at some point. Ironically, Telegram doesn’t…
Read MoreIn episode 13 of “The AI Fix””, meat avatar Cluley learns that AI doesn’t pose an existential threat to humanity and tells meat avatar Stockley how cybersex is about to get very, very weird. Our hosts also learn that men lie on their dating profiles, hear ChatGPT steal somebody’s voice, and discover an AI that…
Read MoreArtificial Intelligence (AI) has long been recognized for its role in detecting phishing attempts, but its capabilities extend far beyond that. With the rise of sophisticated cyber threats, AI has evolved to identify complex and subtle threats, predict attack patterns, and automate responses to emerging risks, significantly enhancing email security. AI is one of the…
Read MoreThe China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of a recently disclosed high-severity security flaw impacting Versa Director. The attacks targeted four U.S. victims and one non-U.S. victim in the Internet service provider (ISP), managed service provider (MSP) and information technology (IT) sectors as…
Read MoreThe cloud, artificial intelligence (AI), machine learning and other technological breakthroughs are radically changing the modern work environment. New assets and services offer increased flexibility, growth potential and access to more resources. However, they also introduce new security risks. Managing vulnerabilities across this ever-expanding threat landscape requires a risk-based approach beyond point solutions and reactive…
Read More$200 Million Cybersecurity E-Rate Funding Available for K-12 Schools and Libraries through FCC Cybersecurity Pilot Program
by nlqip
Empowering K-12 schools and libraries to strengthen their cybersecurity posture with new funding opportunities and best practices. Recent attacks reveal that K-12 schools and libraries are prime targets for cyber actors. Ransomware attacks have had dire consequences and highlighted the need for such institutions to strengthen their cybersecurity posture and reduce risk. Increased attacks against…
Read MoreCVE-2024-7971, which also received a CVSS rating of 8.8 out of 10, was fixed by Google last week in the same release that also patched CVE-2024-7965. Both the flaws were fixed in Chrome version 128.0.6613.84/.85 for Windows/macOS systems and version 128.0.6613.84 Linux users. The other eight vulnerabilities that make up the list of zero-days Google…
Read MoreThe Present and Future of TV Surveillance Ars Technica has a good article on what’s happening in the world of television surveillance. More than even I realized. Tags: privacy, surveillance, television, tracking Posted on August 27, 2024 at 7:08 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict