Category: AI in news
Social Engineering – Techniken Social Engineering hat sich für Cyberkriminelle als besonders erfolgreich erwiesen, wenn es darum geht in Unternehmen einzudringen. Sobald ein Angreifer das Passwort eines vertrauenswürdigen Mitarbeiters erbeutet hat, kann er sich damit einloggen und sensible Daten auslesen. Mit einer Zugangskarte oder einem Code, der physischen Zugang gewährt, können Cyberkriminelle sogar noch größeren…
Read MoreEach cybersecurity event, whether planned or not, “offers an opportunity for all of us to find ways to build our resiliency muscle and protect our patients,” Wolfe says. “Preparation is key and each downtime event provides an opportunity to discover ways to improve our resiliency. One of the areas my team is focused on is…
Read MoreAug 23, 2024Ravie LakshmananEndpoint Security / Data Privacy Cybersecurity researchers have uncovered a new information stealer that’s designed to target Apple macOS hosts and harvest a wide range of information, underscoring how threat actors are increasingly setting their sights on the operating system. Dubbed Cthulhu Stealer, the malware has been available under a malware-as-a-service (MaaS)…
Read MoreThe attacks The SEC said that in the first attack in September 2022, a threat actor hijacked an email chain between the company, then known as American Stock Transfer & Trust Company, and one of its clients, pretending to be an employee of the client company, instructed American Stock Transfer to issue millions of new…
Read MoreSurveillance Watch This is a fantastic project mapping the global surveillance industry. Tags: privacy, surveillance Posted on August 22, 2024 at 9:15 PM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreAug 22, 2024Ravie LakshmananHardware Security / Supply Chain Attack Cybersecurity researchers have uncovered a hardware backdoor within a particular model of MIFARE Classic contactless cards that could allow authentication with an unknown key and open hotel rooms and office doors. The attacks have been demonstrated against FM11RF08S, a new variant of MIFARE Classic that was…
Read MoreAug 22, 2024Ravie LakshmananNetwork Security / Zero-Day Details have emerged about a China-nexus threat group’s exploitation of a recently disclosed, now-patched security flaw in Cisco switches as a zero-day to seize control of the appliance and evade detection. The activity, attributed to Velvet Ant, was observed early this year and involved the weaponization of CVE-2024-20399…
Read MoreCEO Sridhar Ramaswamy dives into Cortex AI and Iceberg customer momentum, the impact of Snowflake’s recent cyberattack and how AI will ‘c ontribute materially to revenue’ in 2025 . CEO Sridhar Ramaswamy was bullish about his company’s AI future during Snowflake’s Q2 earnings report on Wednesday, while also downplaying his company’s recent cyberattack and unveiling…
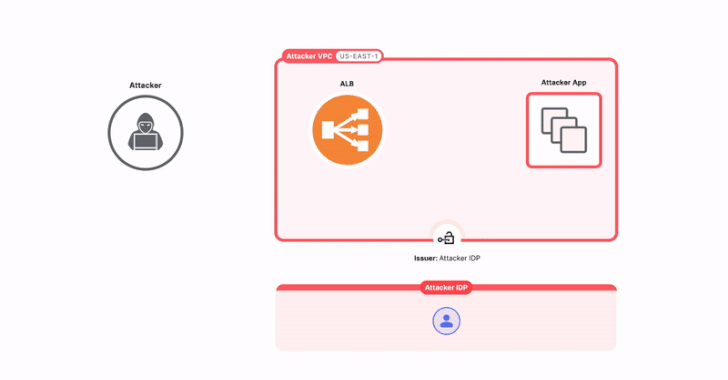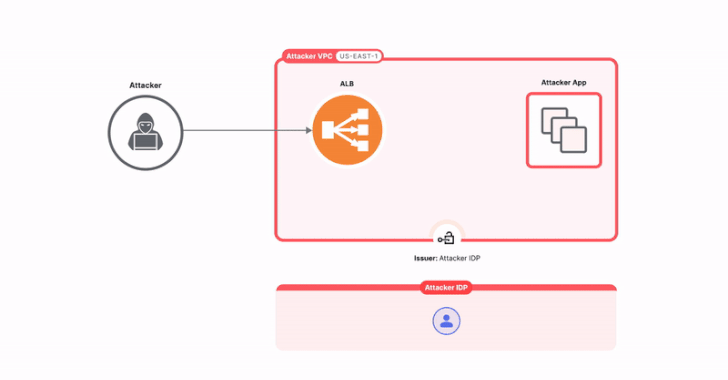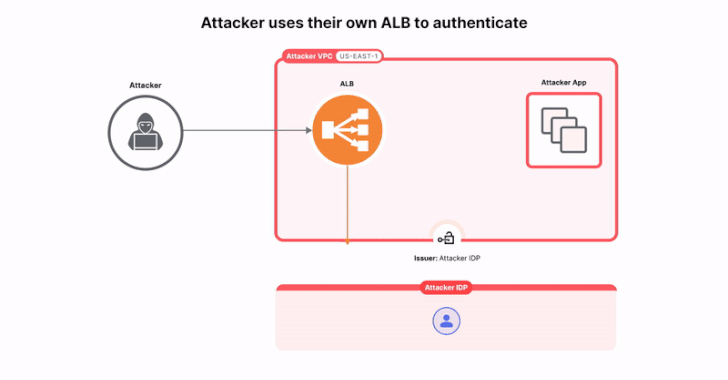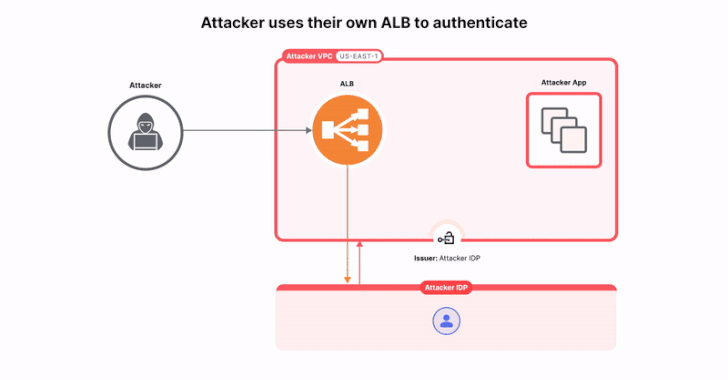
Read MoreAug 22, 2024Ravie LakshmananCloud Security / Application Security As many as 15,000 applications using Amazon Web Services’ (AWS) Application Load Balancer (ALB) for authentication are potentially susceptible to a configuration-based issue that could expose them to sidestep access controls and compromise applications. That’s according to findings from Israeli cybersecurity company Miggo, which dubbed the problem…
Read MoreA production partner of Netflix has suffered a serious security breach which has resulted in yet-to-be-released episodes of popular shows to be leaked online. As Variety reports, the security breach occurred at media localisation company Iyuno which confirmed on August 9 that it had suffered a “security issue, involving unauthorized access to confidential content.” Iyuno…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA