Category: AI in news
“I have given extensive consideration to the question of whether the OAIC should invest further resources in scrutinizing the actions of Clearview AI, a company that has already been investigated by the OAIC and which has found itself the subject of regulatory investigations in at least three jurisdictions around the world as well as a…
Read MoreAug 21, 2024Ravie LakshmananCyber Espionage / Malware A new remote access trojan called MoonPeak has been discovered as being used by a state-sponsored North Korean threat activity cluster as part of a new campaign. Cisco Talos attributed the malicious cyber campaign to a hacking group it tracks as UAT-5394, which it said exhibits some level…
Read MoreAug 21, 2024Ravie LakshmananSoftware Security / Vulnerability Cybersecurity researchers have disclosed a critical security flaw impacting Microsoft’s Copilot Studio that could be exploited to access sensitive information. Tracked as CVE-2024-38206 (CVSS score: 8.5), the vulnerability has been described as an information disclosure bug stemming from a server-side request forgery (SSRF) attack. “An authenticated attacker can…
Read MoreStory of an Undercover CIA Agent who Penetrated Al Qaeda Rolling Stone has a long investigative story (non-paywalled version here) about a CIA agent who spent years posing as an Islamic radical. Unrelated, but also in the “real life spies” file: a fake Sudanese diving resort run by Mossad. Tags: al Qaeda, CIA, espionage, undercover…
Read MoreHours after the CSO exclusive on the potential deal went live, several users submitted their disapproval on Reddit. One wrote, “Oh god I hope not. Action1 is my personal RMM (remote monitoring and management) at this point”, while user another said, “This would be a great acquisition for CS, but will probably suck for a…
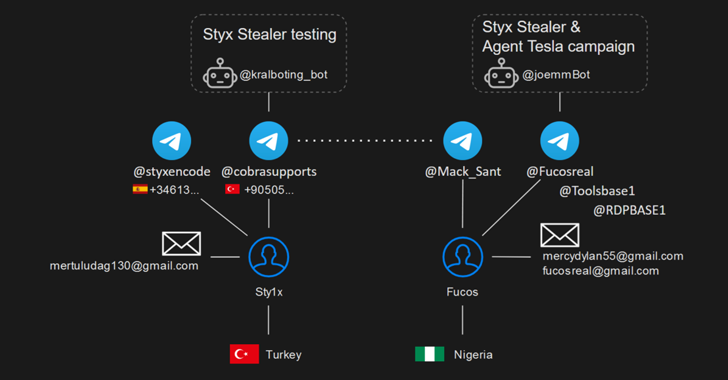
Read MoreAug 21, 2024Ravie LakshmananCyber Espionage / Threat Intelligence In what’s a case of an operational security (OPSEC) lapse, the operator behind a new information stealer called Styx Stealer leaked data from their own computer, including details related to the clients, profit information, nicknames, phone numbers, and email addresses. Styx Stealer, a derivative of the Phemedrone…
Read MoreSemiconductor firms are appealing targets due to the high value of their intellectual property (IP), sensitive manufacturing processes, and their critical role in global supply chains. The complexity and precision involved in chip manufacturing mean that any disruption — whether through data theft, ransomware, or system sabotage — can have far-reaching consequences, impacting not just…
Read More“Let’s say someone is using those providers and they happen to have a common identity platform, maybe SailPoint. If SailPoint is passing a data stream to AWS and Microsoft and maybe others, it could permit access to all that client’s information in one of those hyperscaler environments. It might allow limited data access in the…
Read MoreOther than scanning huge amounts of data for potential threats, the technology comes in handy at sniffing out anomalies. By analyzing patterns and behaviors, GenAI can pinpoint suspicious activities, an ability well realized by Darktrace, a cybersecurity company that uses GenAI to understand normal network behavior and identify deviations. “GenAI can efficiently handle many tasks…
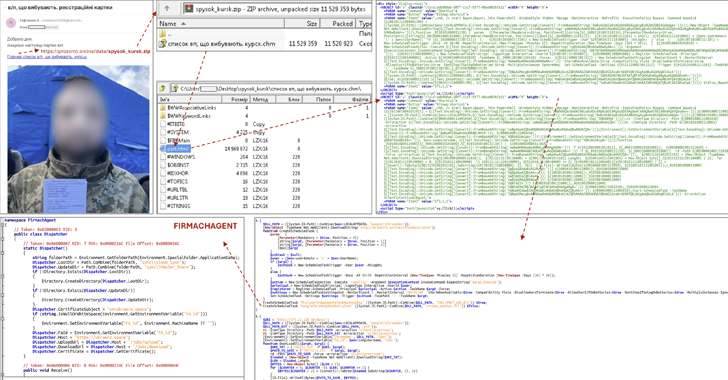
Read MoreAug 21, 2024Ravie LakshmananCyber Warfare / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of new phishing attacks that aim to infect devices with malware. The activity has been attributed to a threat cluster it tracks as UAC-0020, which is also known as Vermin. The exact scale and scope of the…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA