Category: AI in news
Ironically, the answer on updates is in large part because many enterprises have historically found CrowdStrike’s quality to be quite high. “We trusted them too far because they have been really good for too long,” Zalewski said, stressing that the decision was also made because enterprise IT was cutting back extensively. “We didn’t have the…
Read MoreAug 19, 2024Ravie LakshmananVulnerability / Zero-Day A newly patched security flaw in Microsoft Windows was exploited as a zero-day by Lazarus Group, a prolific state-sponsored actor affiliated with North Korea. The security vulnerability, tracked as CVE-2024-38193 (CVSS score: 7.8), has been described as a privilege escalation bug in the Windows Ancillary Function Driver (AFD.sys) for…
Read MoreAt one time, Microsoft created a custom version of Windows 10 in order to comply with and respond to the Chinese government’s concerns. There were rumors that Microsoft was slowly moving AI researchers out of China to Canada, but it’s unclear if that is what is truly going on. Almost every device has software at…
Read MoreAug 19, 2024Ravie LakshmananCybercrime / Network Security Cybersecurity researchers have discovered new infrastructure linked to a financially motivated threat actor known as FIN7. The two clusters of potential FIN7 activity “indicate communications inbound to FIN7 infrastructure from IP addresses assigned to Post Ltd (Russia) and SmartApe (Estonia), respectively,” Team Cymru said in a report published…
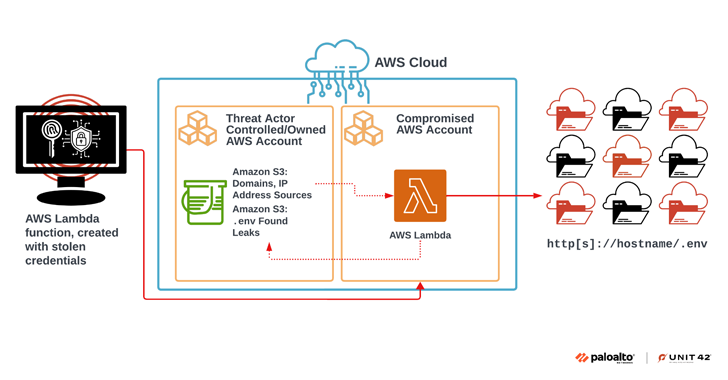
Read MoreLateral movement inside AWS environments In the hands of knowledgeable hackers, leaked secrets can be very powerful and dangerous. For example, the attackers behind this operation exhibited advanced knowledge of AWS APIs.After obtaining an AWS access key the attackers used it to run a GetCallerIdentity API call to verify the identity or role assigned to…
Read MoreThe imminent release of Cisco HyperShield this month marks a pivotal evolution in the cybersecurity landscape. As an “AI-native” security architecture, HyperShield promises to redefine traditional security protocols through its automated proactive cybersecurity measures and AI-driven security solutions. However, the effectiveness of this sophisticated technology heavily relies on the skilled deployment by IT and Information…
Read MoreFriday Squid Blog: The Market for Squid Oil Is Growing How did I not know before now that there was a market for squid oil? The squid oil market has experienced robust growth in recent years, expanding from $4.56 billion in 2023 to $4.94 billion in 2024 at a compound annual growth rate (CAGR) of…
Read MoreGetting an MSP ready to be acquired can take a year or more of prepping the team, cleaning up the accounting and understanding the factors that affect its value, according to a panel of experts. Whether looking to expand opportunities as part of a larger organization or looking to retire, the decision to sell an…
Read MoreAug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications. “Multiple security missteps were present in the course of this campaign, including the following: Exposing environment variables, using long-lived…
Read More‘You need to strengthen your client relationships, your team collaboration and your service consistency. That’s going to increase your efficiency, your operational maturity and, ultimately, your sales, your revenue and your profitability,’ says Ray Mann, channel development manager at ScalePad. Ray Mann, channel development manager at ScalePad, told an audience of MSPs at XChange August…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA