Category: AI in news
‘The pace of change is relentless,’ says Pax8 CEO Scott Chasin. ‘We’re on the cusp of AI reaching human-level intelligence and beyond.’ AI tools are evolving at a rapid pace, with new capabilities coming out every four to six months, and will completely change how IT businesses operate over the next 10 years. “The genie…
Read MoreAug 16, 2024Ravie LakshmananDark Web / Data Breach A 27-year-old Russian national has been sentenced to over three years in prison for peddling financial information, login credentials, and other personally identifying information (PII) on a now-defunct dark web marketplace called Slilpp. Georgy Kavzharadze, 27, of Moscow, Russia, pleaded guilty to one count of conspiracy to…
Read MoreAug 16, 2024Ravie LakshmananMalware / Data Theft Cybersecurity researchers have shed light on a sophisticated information stealer campaign that impersonates legitimate brands to distribute malware like DanaBot and StealC. The activity cluster, orchestrated by Russian-speaking cybercriminals and collectively codenamed Tusk, is said to encompass several sub-campaigns, leveraging the reputation of the platforms to trick users…
Read MoreJuan Perez Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and…
Read MoreCybersecurity Snapshot: First Quantum-resistant Algorithms Ready for Use, While New AI Risks’ Database Is Unveiled
by nlqip
NIST has released the first encryption algorithms that can protect data against quantum attacks. Plus, MIT launched a new database of AI risks. Meanwhile, the CSA published a paper outlining the unique risks involved in building systems that use LLMs. And get the latest on Q2’s most prevalent malware, the Radar/Dispossessor ransomware gang and CVE…
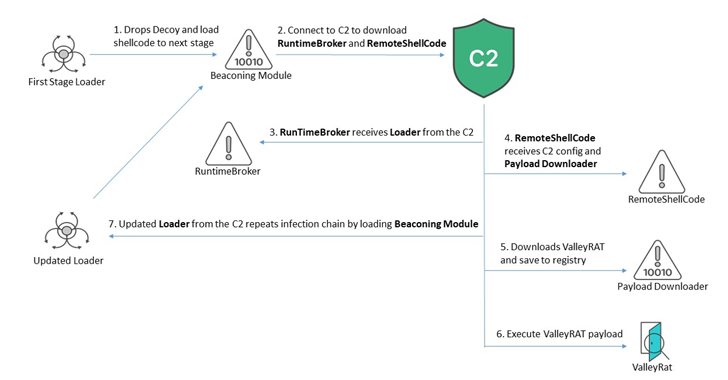
Read MoreAug 16, 2024Ravie LakshmananCyber Attack / Malware Chinese-speaking users are the target of an ongoing campaign that distributes malware known as ValleyRAT. “ValleyRAT is a multi-stage malware that utilizes diverse techniques to monitor and control its victims and deploy arbitrary plugins to cause further damage,” Fortinet FortiGuard Labs researchers Eduardo Altares and Joie Salvio said.…
Read MoreSaaS applications have become indispensable for organizations aiming to enhance productivity and streamline operations. However, the convenience and efficiency these applications offer come with inherent security risks, often leaving hidden gaps that can be exploited. Conducting thorough due diligence on SaaS apps is essential to identify and mitigate these risks, ensuring the protection of your…
Read MoreNew Windows IPv6 Zero-Click Vulnerability The press is reporting a critical Windows vulnerability affecting IPv6. As Microsoft explained in its Tuesday advisory, unauthenticated attackers can exploit the flaw remotely in low-complexity attacks by repeatedly sending IPv6 packets that include specially crafted packets. Microsoft also shared its exploitability assessment for this critical vulnerability, tagging it with…
Read MoreAug 16, 2024Ravie LakshmananMobile Security / Software Security A large percentage of Google’s own Pixel devices shipped globally since September 2017 included dormant software that could be used to stage nefarious attacks and deliver various kinds of malware. The issue manifests in the form of a pre-installed Android app called “Showcase.apk” that comes with excessive…
Read MoreAI start-up Anthropic launches bug reporting scheme Artificial intelligence startup Anthropic launched a vulnerability disclosure program (VDP), managed by HackerOne, in August with bounty rewards up to $15,000 for novel, universal jailbreak attacks that could expose vulnerabilities in critical, high-risk domains such as CBRN (chemical, biological, radiological, and nuclear) and cybersecurity. A jailbreak attack in…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA