Category: AI in news
Aug 10, 2024Ravie LakshmananVulnerability / Enterprise Security Microsoft has disclosed an unpatched zero-day in Office that, if successfully exploited, could result in unauthorized disclosure of sensitive information to malicious actors. The vulnerability, tracked as CVE-2024-38200 (CVSS score: 7.5), has been described as a spoofing flaw that affects the following versions of Office – Microsoft Office…
Read MoreDeploying low-level malware implants Once an attacker manages to execute malicious code inside the SMM they could potentially inject a persistent malware implant inside the UEFI, but this depends on the platform’s configuration, as UEFI can have additional protections such as AMD’s ROM Armor, which controls access to the SPI flash memory where UEFI is…
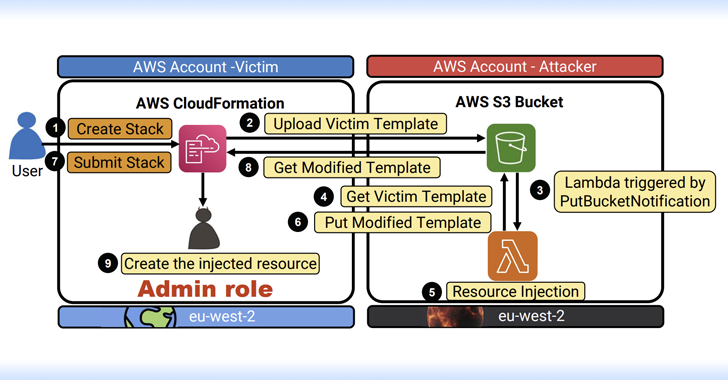
Read MoreAug 09, 2024Ravie LakshmananCloud Security / Data Protection Cybersecurity researchers have discovered multiple critical flaws in Amazon Web Services (AWS) offerings that, if successfully exploited, could result in serious consequences. “The impact of these vulnerabilities range between remote code execution (RCE), full-service user takeover (which might provide powerful administrative access), manipulation of AI modules, exposing…
Read MoreThe infosecurity world came together in Las Vegas this week for Black Hat USA 2024, offering presentations and product announcements that will give CISOs plenty to consider. Here are the top takeaways CISOs should keep in mind when adapting their cybersecurity strategies going forward. [For more Black Hat USA coverage, see “Black Hat: Latest news…
Read MoreFriday Squid Blogging: SQUID Is a New Computational Tool for Analyzing Genomic AI Yet another SQUID acronym: SQUID, short for Surrogate Quantitative Interpretability for Deepnets, is a computational tool created by Cold Spring Harbor Laboratory (CSHL) scientists. It’s designed to help interpret how AI models analyze the genome. Compared with other analysis tools, SQUID is…
Read More‘Together with Acqueon, we can intelligently combine the preferences of the customer with the increasing variety of outreach channels to help enterprises grow their revenue and delight customers, while aligning to compliance standards,’ says Five9 CEO Mike Burkland. Contact center specialist Five9 plans to acquire revenue generation platform provider Acqueon in a move to boost…
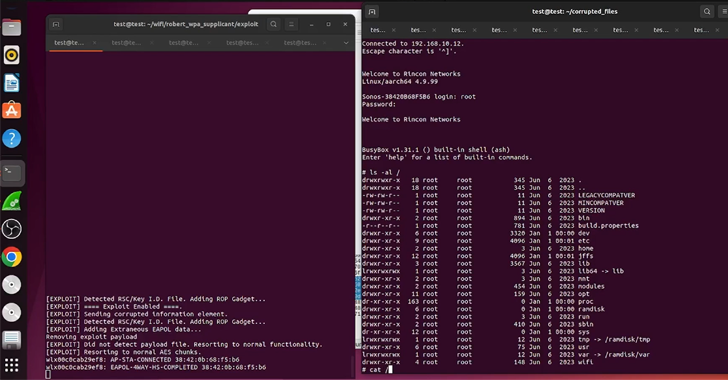
Read MoreAug 09, 2024Ravie LakshmananIoT Security / Wireless Security Cybersecurity researchers have uncovered weaknesses in Sonos smart speakers that could be exploited by malicious actors to clandestinely eavesdrop on users. The vulnerabilities “led to an entire break in the security of Sonos’s secure boot process across a wide range of devices and remotely being able to…
Read MorePeople-Search Site Removal Services Largely Ineffective Consumer Reports has a new study of people-search site removal services, concluding that they don’t really work: As a whole, people-search removal services are largely ineffective. Private information about each participant on the people-search sites decreased after using the people-search removal services. And, not surprisingly, the removal services did…
Read MoreCybersecurity Snapshot: New Report Ranks Top Cloud Threats, while Guide Helps Assess Whether SW Products Are Built Securely
by nlqip
The Cloud Security Alliance has released its list of top cloud threats for 2024. Plus, CISA and the FBI published a guide for determining if a software product was built “secure by design.” Meanwhile, find out how AI can transform offensive security. And the latest on the Royal ransomware gang, the CIS Benchmarks and TikTok’s…
Read MoreWhat it does: FAIR provides a model for understanding, analyzing, and quantifying cyber risk and operational risk in financial terms, according to the Fair Institute. It’s unlike risk assessment frameworks that focus their output on qualitative color charts or numerical weighted scales. Instead it builds a foundation for developing a robust approach to information risk…
Read MoreRecent Posts
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption
- Stellar Startup Data Center Tech Vendors To Know In 2024