Category: AI in news
Aug 15, 2024The Hacker NewsIdentity Security / Threat Detection The Emergence of Identity Threat Detection and Response Identity Threat Detection and Response (ITDR) has emerged as a critical component to effectively detect and respond to identity-based attacks. Threat actors have shown their ability to compromise the identity infrastructure and move laterally into IaaS, Saas, PaaS…
Read MoreAs Rodgers puts it, “What got you here won’t get you there. You know how to configure a firewall, but now you have to communicate to executives. You have to know the business and be able to talk about your technology, your security, the solution through the language of the business. Being able to have…
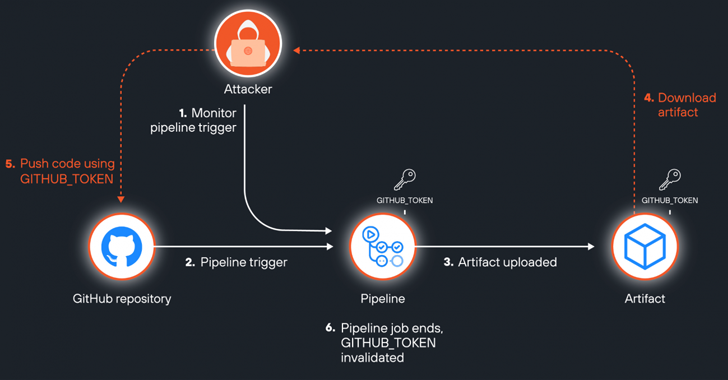
Read MoreAug 15, 2024Ravie LakshmananCloud Security / DevOps A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations’ cloud environments. “A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them…
Read MoreAug 15, 2024Ravie LakshmananNetwork Security / Cybercrime Cybersecurity researchers have discovered a new variant of the Gafgyt botnet that’s targeting machines with weak SSH passwords to ultimately mine cryptocurrency on compromised instances using their GPU computational power. This indicates that the “IoT botnet is targeting more robust servers running on cloud native environments,” Aqua Security…
Read MoreAs interest in AI soars, security leaders are prioritizing an architecture framework that supports innovation and delivers end-to-end protection of sensitive data and models—all while mitigating data exfiltration, poisoning, and other nefarious use case risks. Inadvertent leaks of AI models trained on PII data, users sharing sensitive information via genAI prompts, and use of AI…
Read MoreAug 14, 2024Ravie LakshmananMalware / Network Security An ongoing social engineering campaign with alleged links to the Black Basta ransomware group has been linked to “multiple intrusion attempts” with the goal of conducting credential theft and deploying a malware dropper called SystemBC. “The initial lure being utilized by the threat actors remains the same: an…
Read More“There are at least two more confirmed CVEs that have yet to be patched, (both of) which lead to full NTLM [Network Trust Level Manager] compromise, so the risk is still there,” Gorelik told CSO Online on Wednesday. The hole, which Microsoft has dubbed CVE-2024-38173, allows any email malware to be activated without the recipient…
Read MoreService Express, ECS, GuidePoint Security, Autodesk, HPE and SpaceX’s Starlink business are among the companies to list open positions for channel-related roles in August. This month, Service Express, ECS and GuidePoint Security are among the solution providers to list open positions while Autodesk, Hewlett Packard Enterprise and SpaceX are among the vendors to list open…
Read MoreTexas Sues GM for Collecting Driving Data without Consent Texas is suing General Motors for collecting driver data without consent and then selling it to insurance companies: From CNN: In car models from 2015 and later, the Detroit-based car manufacturer allegedly used technology to “collect, record, analyze, and transmit highly detailed driving data about each…
Read MoreAn investigation dating back almost ten years has seen the extradition this week to the United States of a man suspected to be the head of one the world’s most prolific Russian-speaking cybercriminal gangs. The UK’s National Crime Agency (NCA) says it has been investigating a cybercriminal using the online handle “J P Morgan” since…
Read More