Category: AI in news
Aug 08, 2024Ravie LakshmananWindows Security / Vulnerability Microsoft said it is developing security updates to address two loopholes that it said could be abused to stage downgrade attacks against the Windows update architecture and replace current versions of the Windows files with older versions. The vulnerabilities are listed below – CVE-2024-38202 (CVSS score: 7.3) –…
Read MoreUnlock the Future of Cybersecurity: Exclusive, Next Era AI Insights and Cutting-Edge Training at SANS Network Security 2024
by nlqip
Aug 08, 2024The Hacker NewsArtificial Intelligence / Network Security The Immersive Experience Happening This September in Las Vegas! In an era of relentless cybersecurity threats and rapid technological advancement, staying ahead of the curve is not just a necessity, but critical. SANS Institute, the premier global authority in cybersecurity training, is thrilled to announce Network…
Read MoreAug 08, 2024Ravie LakshmananVulnerability / Network Security A critical security flaw impacting Progress Software WhatsUp Gold is seeing active exploitation attempts, making it essential that users move quickly to apply the latest. The vulnerability in question is CVE-2024-4885 (CVSS score: 9.8), an unauthenticated remote code execution bug impacting versions of the network monitoring application released…
Read MoreAnton Konopliov, founder and CEO of Palma Violets Loans, however, warns that while the proposed rules are beneficial for reducing risk they could “cause chaos” for many firms both on the customer and vendor side around budgets and contractual obligations. “Financial firms will also no longer have the freedom to curate their own contractual terms…
Read MoreEven small farmers are not immune to cyberattacks. Vital Bircher, a farmer in Hagendorn, Switzerland, between Zurich and Lucerne, recently experienced an attack on his computer systems, which were also connected the dairy farmer’s milking robots, the Luzerner Zeitung first reported. Ultimately, one of Bircher’s cows died as a result of the attack. Bircher initially suspected…
Read MoreA partial selfie posted by Puchmade Dev to his Twitter account. Yes, that is a functioning handheld card skimming device, encrusted in diamonds. Underneath that are more medallions, including a diamond-studded bitcoin and payment card. In January, KrebsOnSecurity wrote about rapper Punchmade Dev, whose music videos sing the praises of a cybercrime lifestyle. That story…
Read MoreHere’s the global cloud market share results and six world leaders for Q2 2024, which include AWS, Alibaba, Google Cloud, Oracle, Microsoft and Salesforce, according to new market data. Global cloud market share for the three cloud giants—Microsoft, Google Cloud and AWS—shifted during the second quarter of 2024 as enterprise cloud spending reached a new…
Read MoreAug 07, 2024Ravie LakshmananLinux / Vulnerability Cybersecurity researchers have shed light on a novel Linux kernel exploitation technique dubbed SLUBStick that could be exploited to elevate a limited heap vulnerability to an arbitrary memory read-and-write primitive. “Initially, it exploits a timing side-channel of the allocator to perform a cross-cache attack reliably,” a group of academics…
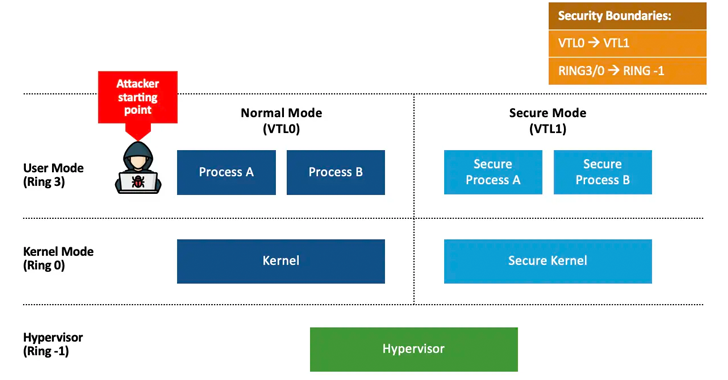
Read MoreKernel-mode drivers are critical yet risky components of the Windows operating system. Learn about their functionality, the dangers they pose, and how Tenable’s new plugins can help identify and mitigate vulnerabilities using community-driven resources like LOLDrivers. Windows is an operating system that, over its 40-plus years of history, has developed more than a few arcane…
Read MoreGoGra leverages the Microsoft Graph API in order to access the Outlook mail service using OAuth access tokens for a username called FNU LNU. The backdoor accesses the Outlook mailbox and reads instructions from email messages with the word “Input” in the subject line. However, the contents of the messages are encrypted with AES-256 and…
Read More