Category: AI in news
FTC warns consumers of scammers offering to remove all negative information from credit reports
by nlqip
Are you worried about your credit report? Are you eager for your credit report to be “cleaned-up” so lenders and landlords will have a better opinion of your financial responsibility and creditworthiness? Tempted by internet ads that promise an easy fix to the pecuniary pickle that you find yourself in? If you think that describes…
Read MoreAug 06, 2024Ravie LakshmananEmail Security / Financial Fraud INTERPOL said it devised a “global stop-payment mechanism” that helped facilitate the largest-ever recovery of funds defrauded in a business email compromise (BEC) scam. The development comes after an unnamed commodity firm based in Singapore fell victim to a BEC scam in mid-July 2024. It refers to…
Read MoreIn episode ten of “The AI Fix” podcast, Graham attempts to say “quinoa”, Mark draws a line in the amper-sand, ChatGPT becomes an expert in solar panels and bomb disposal, and our hosts watch a terrifying tailer for a creepy new AI friend. Graham discovers that the world of AI cookery is a soggy, limey…
Read More“Cequence’s UAP platform offers advanced API discovery and mapping capabilities to ensure comprehensive security coverage,” Talwalkar added. “By automatically identifying all API gateways and infrastructure, including those on cloud platforms like AWS and Azure, the platform eliminates blind spots often associated with traditional security tools.” API discovery, according to Marks, is a significant challenge in…
Read MoreNorth Korean group infiltrated 100-plus companies with imposter IT pros: CrowdStrike report
by nlqip
CSO caught up with Adam Meyers, CrowdStrike’s SVP of counter adversary operations, whose team produced the report, for an exclusive interview on the report’s findings. (Questions regarding the “Channel File 291 incident” were directed to CrowdStrike’s Remediation and Guidance Hub, where the company is providing continuous information and updates, including an FAQ.) Famous Chollima’s shocking…
Read MoreSecuronix: AI-reinforced SIEM Securonix introduced two new capabilities within its Securonix EON suite — Cyber Data Fabric and Noise Canceling SIEM. These updates are designed to enhance the company’s Unified Defense SIEM solution, targeted at helping CyberOps teams tackle sophisticated cyberattacks more effectively. Cyber Data Fabric offers modular architecture for intelligent data classification, ensuring relevant…
Read MoreAs AI transforms industries, security remains critical. Discover the importance of a security-first approach in AI development, the risks of open-source tools, and how Tenable’s solutions can help protect your systems. Artificial Intelligence (AI) is transforming industries and starting to be massively adopted by software developers to build core business applications. However, as organizations embrace…
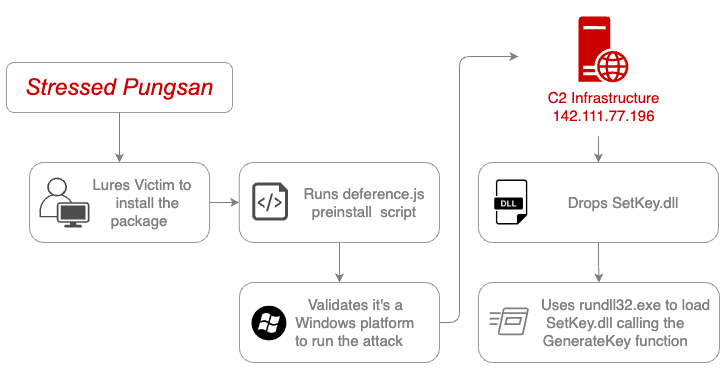
Read MoreAug 06, 2024Ravie LakshmananMalware / Windows Security The North Korea-linked threat actor known as Moonstone Sleet has continued to push malicious npm packages to the JavaScript package registry with the aim of infecting Windows systems, underscoring the persistent nature of their campaigns. The packages in question, harthat-api and harthat-hash, were published on July 7, 2024,…
Read MoreA massive cyberattack targeting Mobile Guardian, a UK-based mobile device management (MDM) firm, has caused widespread disruption to schools and businesses worldwide, including North America, Europe, and Singapore. The incident has resulted in the loss of data and remote wiping of iOS and ChromeOS devices for thousands of users. Mobile Guardian has acknowledged the global…
Read MoreA Better Investigatory Board for Cyber Incidents When an airplane crashes, impartial investigatory bodies leap into action, empowered by law to unearth what happened and why. But there is no such empowered and impartial body to investigate CrowdStrike’s faulty update that recently unfolded, ensnarling banks, airlines, and emergency services to the tune of billions of…
Read MoreRecent Posts
- LevelBlue Cybersecurity Awareness Month Recap
- Red Hat Updates Present ‘Huge’ Partner Opportunities in OpenShift, Edge
- US govt officials’ communications compromised in recent telecom hack
- Microsoft patches Windows zero-day exploited in attacks on Ukraine
- Leaked info of 122 million linked to B2B data aggregator breach