Category: AI in news
Twenty-four prisoners were freed today in an international prisoner swap between Russia and Western countries. Among the eight Russians repatriated were five convicted cybercriminals. In return, Russia has reportedly released 16 prisoners, including Wall Street Journal reporter Evan Gershkovich and ex-U.S. Marine Paul Whelan. Among the more notable Russian hackers released in the prisoner swap…
Read MoreHumans still have something to say in the age of AI Beyond the failure of CrowdStrike and the systemic problems affecting the technology industry, the global computer blackout made it clear that, in the era of artificial intelligence (AI) everywhere, human beings are not expendable, and that the world is not ready to leave big…
Read More“The manufacturing, healthcare, and technology sectors were the top targets of ransomware attacks, while the energy sector experienced a 500% year-over-year spike as critical infrastructure and susceptibility to operational disruptions make it particularly attractive to cybercriminals,” the report said. “The energy sector experienced a 527.27% year-over-year increase in ransomware attacks, likely due to its critical…
Read MoreOn Friday posts were published on the internet containing what appeared to be the personal information of Israeli Olympic athletes. As the Times of Israel reports, information including athletes’ names, phone numbers, addresses, passwords, family relationships, photographs, military status and blood test results were published on Telegram. The hackers also created a website and Twitter…
Read MoreThe staggering sum of US $75 million has reportedly been paid to a ransomware gang in what is believed to be the largest known ransom payment made by a cyber attack victim since records began. Researchers at Zscaler claim in a new report that the record-breaking figure was paid by an undisclosed Fortune 50 company…
Read MoreAug 01, 2024Ravie LakshmananVulnerability / Threat Intelligence Over a million domains are susceptible to takeover by malicious actors by means of what has been called a Sitting Ducks attack. The powerful attack vector, which exploits weaknesses in the domain name system (DNS), is being exploited by over a dozen Russian-nexus cybercriminal actors to stealthily hijack…
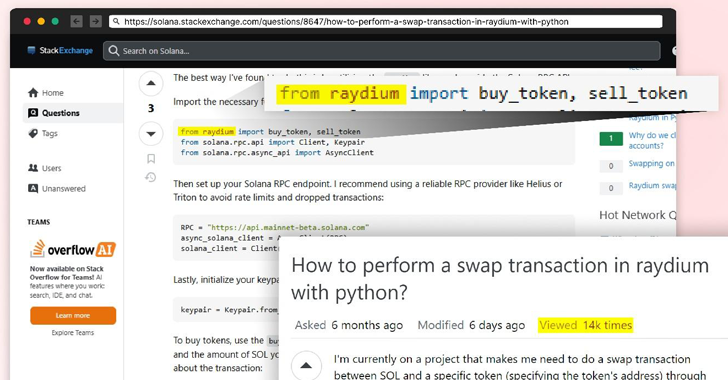
Read MoreIn yet another sign that threat actors are always looking out for new ways to trick users into downloading malware, it has come to light that the question-and-answer (Q&A) platform known as Stack Exchange has been abused to direct unsuspecting developers to bogus Python packages capable of draining their cryptocurrency wallets. “Upon installation, this code…
Read More‘Cautious customer behavior once again elongated sales cycles, then drove prioritization of needs over wants and cost savings over expansion. Capital investment in complex solutions, particularly those tied to data center and network modernization, continued to be downsized or put on hold. And there was growing refresh activity in client devices,’ says CDW Chair and…
Read More“Through thorough investigation and leveraging sensitive sources, CloudSEK has confirmed that the ransomware group responsible for this attack is RansomEXX,” CloudSEK said. “Our extensive engagement with the affected banking sector in India facilitated this determination.” The AI-powered, threat intelligence firm said the attack happened through a misconfigured Jenkins server, an open-source automation tool for developers…
Read MoreHow to detect and prevent attackers from using these various techniques Obfuscation is an important technique for protecting software that also carries risks, especially when used by malware authors. In this article, we examine obfuscation, its effects, and responses to it. What Is Obfuscation? Obfuscation is the technique of intentionally making information difficult to read,…
Read More