Category: AI in news
Education in Secure Software Development The Linux Foundation and OpenSSF released a report on the state of education in secure software development. …many developers lack the essential knowledge and skills to effectively implement secure software development. Survey findings outlined in the report show nearly one-third of all professionals directly involved in development and deployment …
Read MoreAug 01, 2024Ravie LakshmananData Encryption / Browser Security Google has announced that it’s adding a new layer of protection to its Chrome browser through what’s called app-bound encryption to prevent information-stealing malware from grabbing cookies on Windows systems. “On Windows, Chrome uses the Data Protection API (DPAPI) which protects the data at rest from other…
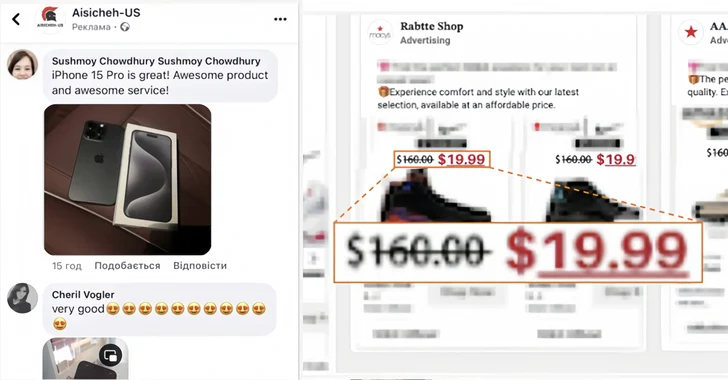
Read MoreAug 01, 2024Ravie LakshmananOnline Fraud / Malvertising Facebook users are the target of a scam e-commerce network that uses hundreds of fake websites to steal personal and financial data using brand impersonation and malvertising tricks. Recorded Future’s Payment Fraud Intelligence team, which detected the campaign on April 17, 2024, has given it the name ERIAKOS…
Read More4. Test your incident response plans thoroughly Organizations must have designated people and formal processes in place to determine the “material impact” of an incident and to communicate with relevant authorities by the stipulated deadlines. Testing and preparedness of incident response plans will be crucial. Sometimes when groups are brought together from a diverse set…
Read Morenjuy67 njuy67 njuy68 njuy68 njuy69 njuy69 njuy70 njuy70 njuy71 njuy71 njuy72 njuy72 njuy73 njuy73 njuy74 njuy74 njuy75 njuy75 njuy76 njuy76 njuy77 njuy77 njuy78 njuy78 njuy79 njuy79 njuy80 njuy80 njuy81 njuy81 njuy82 njuy82 njuy83 njuy83 njuy84 njuy84 njuy85 njuy85 njuy86 njuy86 njuy87 njuy87 njuy88 njuy88 njuy89 njuy89 njuy90 njuy90 njuy91 njuy91 njuy92 njuy92 njuy93 njuy93 njuy94…
Read MoreThe CABF requires that, in one format of the DNS CNAME entry, the random value be prefixed with an underscore, and DigiCert discovered that, in some cases, that character was not included, rendering the validation non-compliant. By CABF rules, those certificates must be revoked within 24 hours, with no exceptions. However, DigiCert said in an…
Read MoreIn November, the Lazarus group, North Korea’s primary cyberespionage and sabotage arm, compromised a Taiwanese multimedia software company called CyberLink and trojanized the installer for one of its commercial applications. In February, Japan’s CERT reported that Lazarus uploaded malicious Python packages to PyPI, the official Python package repository. One of the dangers of campaigns like…
Read MoreThe cybersecurity industry needs nearly four million professionals to fill vacant roles, and as adversaries advance their tactics, this figure is set to increase. Meanwhile, this skills shortage significantly impacts organizations worldwide, with 70% of IT leaders saying this widening gap creates additional risks for their business. While many organizations are taking creative approaches to…
Read MoreNearly 7% of Internet Traffic Is Malicious Cloudflare reports on the state of applications security. It claims that 6.8% of Internet traffic is malicious. And that CVEs are exploited as quickly as 22 minutes after proof-of-concepts are published. News articles. Tags: denial of service, malware, spam, vulnerabilities Posted on July 31, 2024 at 11:55 AM…
Read MoreJul 31, 2024Ravie LakshmananWeb Security / Compliance Certificate authority (CA) DigiCert has warned that it will be revoking a subset of SSL/TLS certificates within 24 hours due to an oversight with how it verified if a digital certificate is issued to the rightful owner of a domain. The company said it will be taking the…
Read More