Category: AI in news
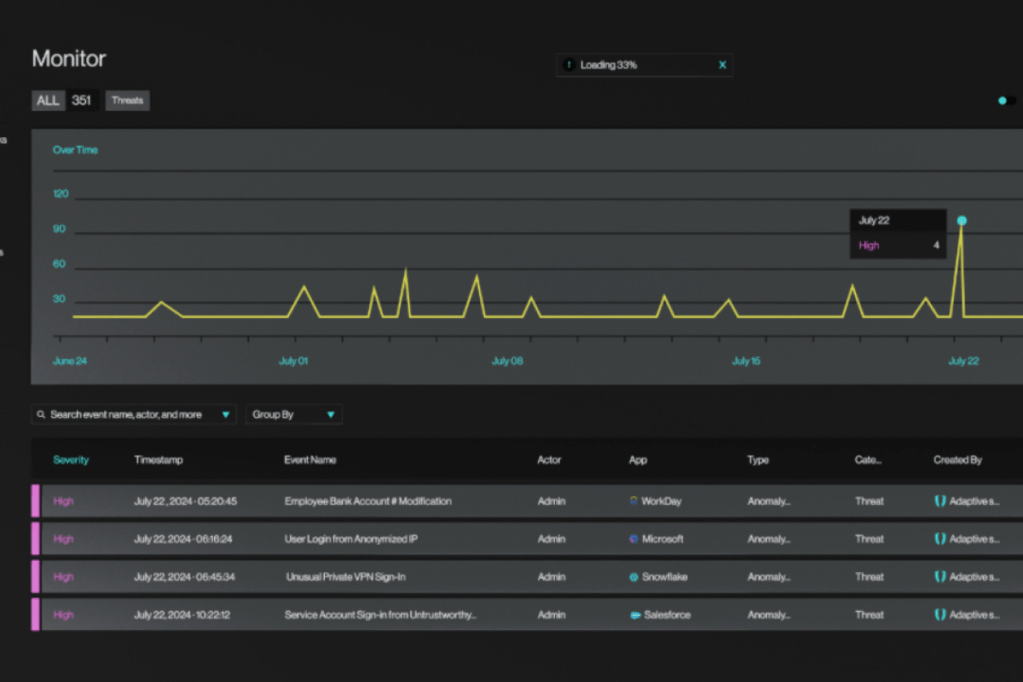
Adaptive Shield, a leader in SaaS Security, today announced its breakthrough Identity Threat Detection & Response (ITDR) platform for SaaS environments. Since entering this space a year ago, the company has already become a leader in the field, implementing the solution in hundreds of enterprise customer environments. Adaptive Shield will demonstrate its new ITDR platform…
Read MoreFor the second year in a row, Brazil took the crown as the country with the lowest cost per breach, at $1.36 million (though up by 11.5%, from $1.22 million in 2023). Damages vary by attack type and skills shortage The type of attack influenced the financial damage, the report noted. Destructive attacks, in which…
Read MoreAsked if there will differences in how online identity will be handled in China compared to other nations such as India, with its Aadhaar identifier, or France, whose France Connect allows residents to authenticate their identity to most government departments based on a verified identity already provided to another department, he said he expects that…
Read MoreMystified as to how this was possible, Guardio noticed that the phishing emails all originated on an SMTP virtual server routed via Office365 Online Exchange before entering a domain-specific relay server operated by Proofpoint. Importantly, that final Proofpoint server was where the DKIM and SPF authenticity would be passed as legitimate, essentially allowing it to…
Read MoreThis is at least the third major outage for Microsoft in July. Days after a faulty CrowdStrike update downed millions of Windows machines worldwide and a coincidental Microsoft Azure region outage in the United States, Microsoft has reported “access issues and degraded performance” for a variety of services and features under its Microsoft 365 umbrella.…
Read MoreIn episode nine of “The AI Fix” podcast, our hosts learn about the world’s most dangerous vending machine, a cartoonist who hypnotises himself with AI, and OpenAI’s plans to eat Google’s lunch. Graham tells Mark about a pig-farming professor, and Mark tests Graham’s tolerance with OpenAI’s terrifying roadmap to Artificial General Intelligence. All this and…
Read MoreTenable sponsored research from Cyentia and FIRST, which finds that while vulnerability exploitation is highly variable, EPSS is getting stronger in its ability to predict exploitation. The number of CVEs published annually keeps growing, which means it is increasingly crucial to predict which ones require the attention of vulnerability management teams. New research from Cyentia…
Read MoreJul 30, 2024Ravie LakshmananMobile Security / Spyware A new iteration of a sophisticated Android spyware called Mandrake has been discovered in five applications that were available for download from the Google Play Store and remained undetected for two years. The applications attracted a total of more than 32,000 installations before being pulled from the app…
Read MoreAnother research firm Assetnote added one more bug (CVE-2024-5178), with less severity, to the list, but said, that when chained together, hackers can exploit the vulnerabilities to access the ServiceNow database. “These vulnerabilities enable unauthenticated remote attackers to execute arbitrary code within the Now Platform, potentially leading to compromise, data theft, and disruption of business…
Read MoreJul 30, 2024Ravie LakshmananMalware / Cyber Threat Cybersecurity researchers have detailed widespread phishing campaigns targeting small and medium-sized businesses (SMBs) in Poland during May 2024 that led to the deployment of several malware families like Agent Tesla, Formbook, and Remcos RAT. Some of the other regions targeted by the campaigns include Italy and Romania, according…
Read MoreRecent Posts
- LevelBlue Cybersecurity Awareness Month Recap
- Red Hat Updates Present ‘Huge’ Partner Opportunities in OpenShift, Edge
- US govt officials’ communications compromised in recent telecom hack
- Microsoft patches Windows zero-day exploited in attacks on Ukraine
- Leaked info of 122 million linked to B2B data aggregator breach