Category: AI in news
Another research firm Assetnote added one more bug (CVE-2024-5178), with less severity, to the list, but said, that when chained together, hackers can exploit the vulnerabilities to access the ServiceNow database. “These vulnerabilities enable unauthenticated remote attackers to execute arbitrary code within the Now Platform, potentially leading to compromise, data theft, and disruption of business…
Read MoreJul 30, 2024Ravie LakshmananMalware / Cyber Threat Cybersecurity researchers have detailed widespread phishing campaigns targeting small and medium-sized businesses (SMBs) in Poland during May 2024 that led to the deployment of several malware families like Agent Tesla, Formbook, and Remcos RAT. Some of the other regions targeted by the campaigns include Italy and Romania, according…
Read MoreProviding Security Updates to Automobile Software Auto manufacturers are just starting to realize the problems of supporting the software in older models: Today’s phones are able to receive updates six to eight years after their purchase date. Samsung and Google provide Android OS updates and security updates for seven years. Apple halts servicing products seven…
Read MoreJul 30, 2024Ravie LakshmananCyber Espionage / Malware The nation-state threat actor known as SideWinder has been attributed to a new cyber espionage campaign targeting ports and maritime facilities in the Indian Ocean and Mediterranean Sea. The BlackBerry Research and Intelligence Team, which discovered the activity, said targets of the spear-phishing campaign include countries like Pakistan,…
Read MoreMoreover, experts say this kind of software error will almost certainly occur again. “We should expect it to happen again, and you need to protect against it,” Ranjan Singh, chief product officer at Kaseya, tells CSO. “There are humans involved in the entire chain of development, so invariably, there’s always room for error. But it’s…
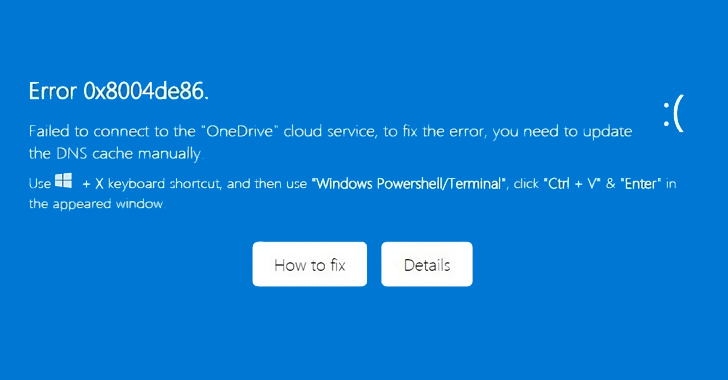
Read MoreJul 30, 2024Ravie LakshmananMalware / Email Security Cybersecurity researchers are warning about a new phishing campaign that targets Microsoft OneDrive users with the aim of executing a malicious PowerShell script. “This campaign heavily relies on social engineering tactics to deceive users into executing a PowerShell script, thereby compromising their systems,” Trellix security researcher Rafael Pena…
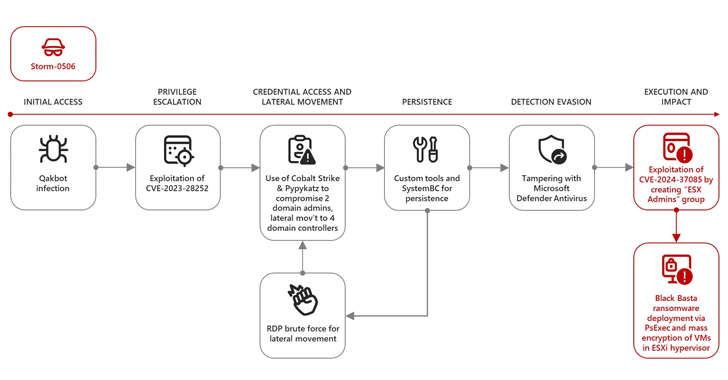
Read MoreA recently patched security flaw impacting VMware ESXi hypervisors has been actively exploited by “several” ransomware groups to gain elevated permissions and deploy file-encrypting malware. The attacks involve the exploitation of CVE-2024-37085 (CVSS score: 6.8), an Active Directory integration authentication bypass that allows an attacker to obtain administrative access to the host. “A malicious actor…
Read MoreSecurity researchers at Microsoft have discovered a vulnerability in VMware ESXi hypervisors that has been exploited by ransomware operators to gain full administrative access to a domain-joined hypervisor. The problem, identified as CVE-2024-37085, granted full admin privileges to members of a domain group, without proper validation. It has been used by several ransomware groups such…
Read More‘Red Hat is really doubling down on our commitment to the ecosystem,’ Red Hat VP Kevin Kennedy tells CRN. Amid a boost in business opportunities in artificial intelligence and migration from legacy virtualization vendors, Red Hat is transforming its partner program to standardization worldwide, streamlined incentives and a better digital experience. Kevin Kennedy, vice president…
Read MoreJul 29, 2024Ravie LakshmananEnterprise Security / Data Protection Cybersecurity company Acronis is warning that a now-patched critical security flaw impacting its Cyber Infrastructure (ACI) product has been exploited in the wild. The vulnerability, tracked as CVE-2023-45249 (CVSS score: 9.8), concerns a case of remote code execution that stems from the use of default passwords. The…
Read More