Category: AI in news
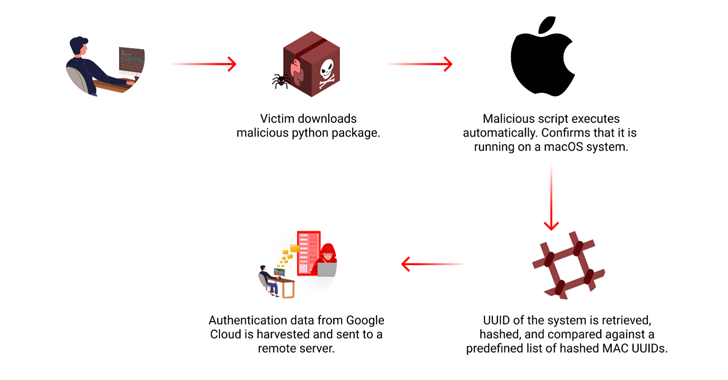
Jul 27, 2024NewsroomCybersecurity / Cloud Security Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository that targets Apple macOS systems with the goal of stealing users’ Google Cloud credentials from a narrow pool of victims. The package, named “lr-utils-lib,” attracted a total of 59 downloads before it was taken down.…
Read Morenjuy67 njuy67 njuy68 njuy68 njuy69 njuy69 njuy70 njuy70 njuy71 njuy71 njuy72 njuy72 njuy73 njuy73 njuy74 njuy74 njuy75 njuy75 njuy76 njuy76 njuy77 njuy77 njuy78 njuy78 njuy79 njuy79 njuy80 njuy80 njuy81 njuy81 njuy82 njuy82 njuy83 njuy83 njuy84 njuy84 njuy85 njuy85 njuy86 njuy86 njuy87 njuy87 njuy88 njuy88 njuy89 njuy89 njuy90 njuy90 njuy91 njuy91 njuy92 njuy92 njuy93 njuy93 njuy94…
Read MoreCrooks Bypassed Google’s Email Verification to Create Workspace Accounts, Access 3rd-Party Services – Krebs on Security
by nlqip
Google says it recently fixed an authentication weakness that allowed crooks to circumvent the email verification required to create a Google Workspace account, and leverage that to impersonate a domain holder to third-party services that allow logins through Google’s “Sign in with Google” feature. Last week, KrebsOnSecurity heard from a reader who said they received a…
Read MoreFriday Squid Blogging: Sunscreen from Squid Pigments They’re better for the environment. Blog moderation policy. Tags: squid Posted on July 26, 2024 at 5:02 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreOperational expenses and loss to business would differ greatly from organization to organization, and segment to segment. Parametrix, using its service monitoring sensors, estimated healthcare suffering the most at $1.94 billion in direct losses from the incident, with banking and transportation closely behind at $1.15 billion and $0.86 billion, respectively. It estimated the loss per…
Read MoreCompromising the Secure Boot Process This isn’t good: On Thursday, researchers from security firm Binarly revealed that Secure Boot is completely compromised on more than 200 device models sold by Acer, Dell, Gigabyte, Intel, and Supermicro. The cause: a cryptographic key underpinning Secure Boot on those models that was compromised in 2022. In a public…
Read MoreFrom the editors of our sister publication Computerworld, this enterprise buyer’s guide helps IT staff understand what the various unified endpoint management (UEM) platforms can do for their organizations and how to choose the right solution. Source link lol
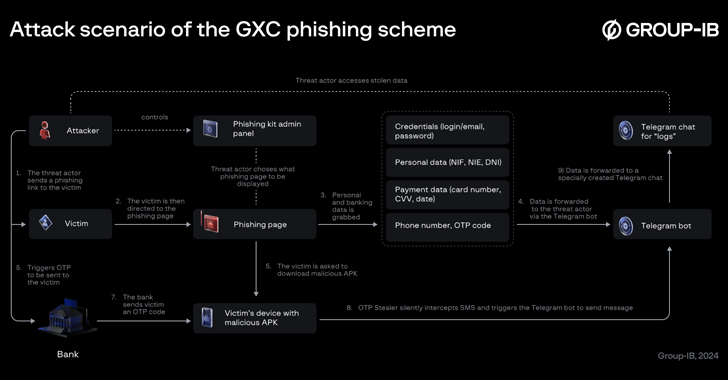
Read MoreA Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS) offerings to the next level. Singaporean cybersecurity company Group-IB, which has been tracking the e-crime actor since January 2023, described the crimeware solution as a “sophisticated AI-powered phishing-as-a-service platform” capable of targeting users of more…
Read MoreCybersecurity Snapshot: North Korea’s Cyber Spies Hunt for Nuclear Secrets, as Online Criminals Ramp Up AI Use in the EU
by nlqip
Check out a CISA-FBI advisory about North Korean cyber espionage on critical infrastructure orgs. Plus, what Europol found about the use of AI for cybercrime. Meanwhile, the risk concerns that healthcare leaders have about generative AI. And a poll on water plant cybersecurity. And much more! Dive into six things that are top of mind…
Read MoreJul 26, 2024The Hacker NewsDigital Warfare / Cybersecurity Training “Peace is the virtue of civilization. War is its crime. Yet it is often in the furnace of war that the sharpest tools of peace are forged.” – Victor Hugo. In 1971, an unsettling message started appearing on several computers that comprised ARPANET, the precursor to…
Read MoreRecent Posts
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption
- Stellar Startup Data Center Tech Vendors To Know In 2024