Category: AI in news
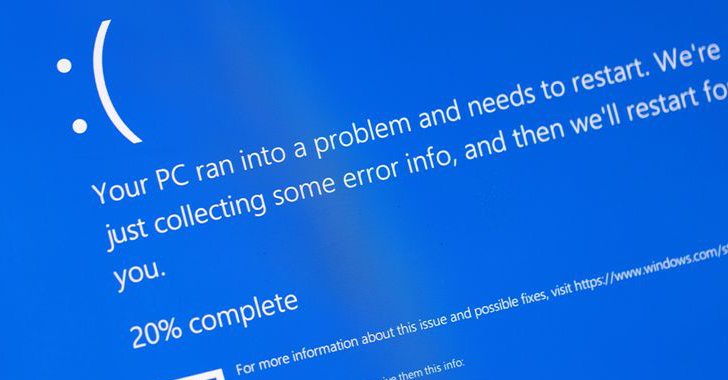
“Based on the testing performed before the initial deployment of the Template Type (on March 05, 2024), trust in the checks performed in the Content Validator, and previous successful IPC Template Instance deployments, these instances were deployed into production,” CrowdStrike explained in its review. “When received by the sensor and loaded into the Content Interpreter,…
Read MoreSecurity questionnaires aren’t just an inconvenience — they’re a recurring problem for security and sales teams. They bleed time from organizations, filling the schedules of professionals with monotonous, automatable work. But what if there were a way to reduce or even altogether eliminate security questionnaires? The root problem isn’t a lack of great questionnaire products…
Read MoreLeidos serves prominent clients including the US Department of Defense (DOD), the Department of Homeland Security (DHS), NASA, and various other US and foreign agencies, as well as commercial businesses. The leak has raised significant concerns given the sensitive nature of the information involved. The report reviewed some of the leaked files posted on a…
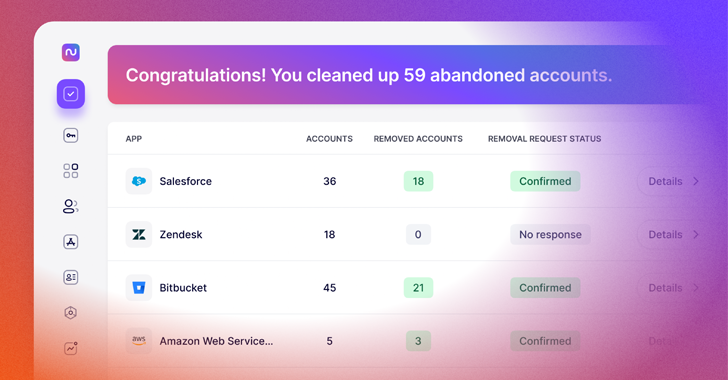
Read MoreJul 24, 2024The Hacker NewsSaaS Management / IT Governance There is one simple driver behind the modern explosion in SaaS adoption: productivity. We have reached an era where purpose-built tools exist for almost every aspect of modern business and it’s incredibly easy (and tempting) for your workforce to adopt these tools without going through the…
Read MoreMost companies, however, didn’t extend this to its natural next step. Why do we trust our administrative users and software implicitly? Endpoints — whether laptops held by users, servers in the cloud, or embedded devices powering airport displays — are often heavily laden with remote administrator tools in the unified endpoint management (UEM) space. Asset…
Read MoreJul 24, 2024NewsroomSoftware Update / IT Outage Cybersecurity firm CrowdStrike on Wednesday blamed an issue in its validation system for causing millions of Windows devices to crash as part of a widespread outage late last week. “On Friday, July 19, 2024 at 04:09 UTC, as part of regular operations, CrowdStrike released a content configuration update…
Read MoreThe DORA doesn’t directly name escrow as a viable proportional component of stressed exit plans, but that doesn’t mean escrow isn’t the solution. “Remember, DORA is technology agnostic and cannot name a solution, but there’s a clear reason why the likes of the PRA, OCC, RBI, and MAS all name escrow: It works,” Scott says.…
Read MoreJul 24, 2024NewsroomVulnerability / Software Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities are listed below – CVE-2012-4792 (CVSS score: 9.3) – Microsoft Internet Explorer Use-After-Free Vulnerability CVE-2024-39891 (CVSS score: 5.3) – Twilio Authy…
Read MoreThe core discovery by the researchers is that connection tracking features don’t always isolate processes from each other, especially with those VPNs that run on top of Linux and make use of Netfilter implementations, a typical internal connection tracking routine. Without this isolation, connections could be shared across other machine resources. “This approach can pose…
Read More‘I think we are in this phase where we have to deeply work and make sure on these use cases and these work flows we are driving deeper progress in unlocking value, which I’m bullish will happen. But these things take time,’ says Alphabet CEO Sundar Pichai. Google parent company Alphabet is uniquely well-positioned for…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption