Category: AI in news
In episode eight of “The AI Fix”, our hosts tackle the latest news from the world of AI and learn about two important medical breakthroughs, Mark coughs, Graham ruins “Killing me softly”, and neither shows their junk to an AI. Graham explains humour to Mark and shares a donkey story he learned from a Bulgarian,…
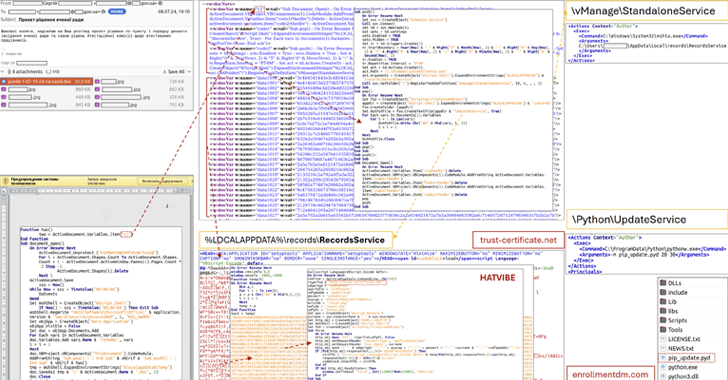
Read MoreJul 23, 2024NewsroomCyber Espionage / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has alerted of a spear-phishing campaign targeting a scientific research institution in the country with malware known as HATVIBE and CHERRYSPY. The agency attributed the attack to a threat actor it tracks under the name UAC-0063, which was previously observed targeting…
Read MoreOne of the pressing reasons for the delay is time. Google, reportedly, needs more time to test out the Privacy Sandbox settings. “The most consistent feedback we’ve received is the need for more time to evaluate and test the new Privacy Sandbox technologies before deprecating third-party cookies in Chrome,” Chavez said in a July 2022…
Read More2017 ODNI Memo on Kaspersky Labs It’s heavily redacted, but still interesting. Many more ODNI documents here. Tags: FOIA, Kaspersky Posted on July 23, 2024 at 7:08 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreJul 23, 2024The Hacker NewsCorporate Security / Data Protection The initial onboarding stage is a crucial step for both employees and employers. However, this process often involves the practice of sharing temporary first-day passwords, which can expose organizations to security risks. Traditionally, IT departments have been cornered into either sharing passwords in plain text via…
Read MoreThe NHI problem is “more challenging in cloud environments, with third-party interactions, IoT deployments, and at remote sites,” said Michael Tsia, the head of product at SaaS management platform Zluri. “The nature of these distributed environments makes it hard to keep centralized control and visibility over NHIs. Third-party NHIs might not be under your direct…
Read MoreUsing just-in-time controls to secure access to your SaaS applications will reduce your cloud attack surface by avoiding permanent access and enforcing least privilege. By granting permissions on a time-limited, as-needed basis only, just-in-time (JIT) controls are an important security mechanism for protecting access to cloud resources. JIT access is becoming a popular cloud security…
Read Morenjuy67 njuy67 njuy68 njuy68 njuy69 njuy69 njuy70 njuy70 njuy71 njuy71 njuy72 njuy72 njuy73 njuy73 njuy74 njuy74 njuy75 njuy75 njuy76 njuy76 njuy77 njuy77 njuy78 njuy78 njuy79 njuy79 njuy80 njuy80 njuy81 njuy81 njuy82 njuy82 njuy83 njuy83 njuy84 njuy84 njuy85 njuy85 njuy86 njuy86 njuy87 njuy87 njuy88 njuy88 njuy89 njuy89 njuy90 njuy90 njuy91 njuy91 njuy92 njuy92 njuy93 njuy93 njuy94…
Read MoreFrom Google’s potential blockbuster acquisition of security startup Wiz to the massive CrowdStrike and Microsoft chaos, here’s four big things to watch for during Google Cloud’s earnings results slated for Tuesday. Google Cloud’s parent company Alphabet is releasing the financial earnings results for its second quarter 2024 on Tuesday with potential huge discussions around the…
Read MoreFor many enterprises, IT infrastructures have broadened to the extent that they seemingly have no boundaries. Many employees are working remotely or via a hybrid model. Cloud-based services have become the norm. Edge computing and the internet of things are continuing to grow. This can all be great from the standpoint of keeping staffers happy,…
Read MoreRecent Posts
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption