Category: AI in news
Jul 22, 2024NewsroomCloud Security / Phishing Attack A Latin America (LATAM)-based financially motivated actor codenamed FLUXROOT has been observed leveraging Google Cloud serverless projects to orchestrate credential phishing activity, highlighting the abuse of the cloud computing model for malicious purposes. “Serverless architectures are attractive to developers and enterprises for their flexibility, cost effectiveness, and ease…
Read MoreMore sensitive information that could be used in frauds and identity thefts included Medicare card numbers (including individual identifier and expiry), Pensioner Concession card number and expiry, Commonwealth Seniors card number and expiry, Healthcare Concession card number and expiry, Department of Veterans’ Affairs (DVA) (Gold, White, Orange) card number and expiry. Sensitive individual health data…
Read MoreSnake Mimics a Spider This is a fantastic video. It’s an Iranian spider-tailed horned viper (Pseudocerastes urarachnoides). Its tail looks like a spider, which the snake uses to fool passing birds looking for a meal. Tags: natural security Posted on July 22, 2024 at 7:06 AM • 3 Comments Sidebar photo of Bruce Schneier by…
Read MoreOur new research paper gives you a roadmap for using Pimcore’s features while preserving security. Enterprises are using Pimcore, an open-source enterprise PHP solution, to streamline data management and experience management across devices. Our new research paper “Auditing Pimcore Enterprise Platform” examines the most common issues with Pimcore and details methods that can be used…
Read MoreThe opportunities to use AI in workflow automation are many and varied, but one of the simplest ways to use AI to save time and enhance your organization’s security posture is by building an automated SMS analysis service. Workflow automation platform Tines provides a good example of how to do it. The vendor recently released…
Read MoreEmployers should also clearly define the process for the intern and explain what is required of them. If possible, Smith recommends mentoring an intern, not simply ticking off a bureaucratic checklist of their tasks: “I do fervently believe you essentially need a sponsor, someone who’s going to take the intern under his or her wing…
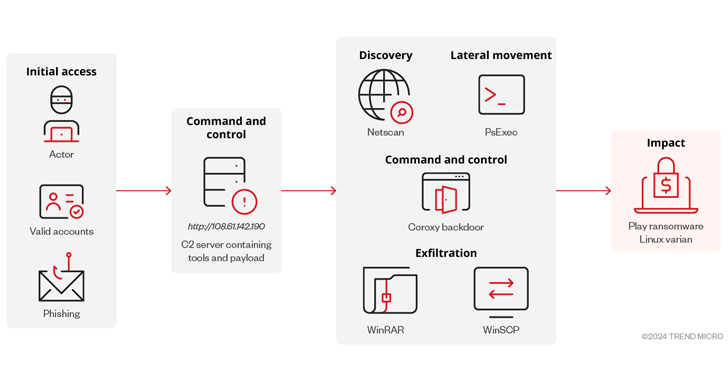
Read MoreCybersecurity researchers have discovered a new Linux variant of a ransomware strain known as Play (aka Balloonfly and PlayCrypt) that’s designed to target VMware ESXi environments. “This development suggests that the group could be broadening its attacks across the Linux platform, leading to an expanded victim pool and more successful ransom negotiations,” Trend Micro researchers…
Read MoreThe defect was in one it calls Channel 291, the company said in Saturday’s technical blog post. The file is stored in a directory named “C:WindowsSystem32driversCrowdStrike” and with a filename beginning “C-00000291-” and ending “.sys”. Despite the file’s location and name, the file is not a Windows kernel driver, CrowdStrike insisted. Channel File 291 is…
Read MoreJul 20, 2024NewsroomCybercrime / Data Breach Law enforcement officials in the U.K. have arrested a 17-year-old boy from Walsall who is suspected to be a member of the notorious Scattered Spider cybercrime syndicate. The arrest was made “in connection with a global cyber online crime group which has been targeting large organizations with ransomware and…
Read MoreDismissed charges Although the judge ordered that the securities fraud charge proceed to trial, he dismissed all of the other charges. Those charges included the SEC’s argument that security misrepresentations amount to accounting errors, and that statements made in news releases and blogs also fooled investors. Engelmayer also dismissed public statements by Brown, including those…
Read MoreRecent Posts
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption