Category: AI in news
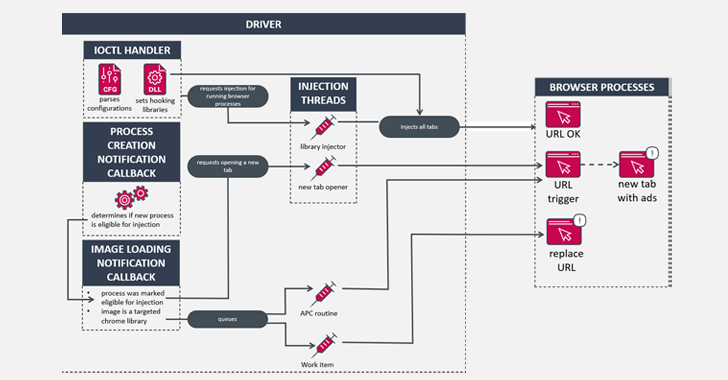
Jul 18, 2024NewsroomMalware / Windows Security Cybersecurity researchers have shed light on an adware module that purports to block ads and malicious websites, while stealthily offloading a kernel driver component that grants attackers the ability to run arbitrary code with elevated permissions on Windows hosts. The malware, dubbed HotPage, gets its name from the eponymous…
Read MoreTenable Announces Former Senior Administration Officials to Inaugural Public Sector Advisory Board
by nlqip
Rob Joyce and Mark Weatherford will help Tenable shape federal cyber and AI policy. The landscape of cybersecurity policies, regulations and recommendations at both the federal and state levels continues to rapidly evolve. Tenable has long advocated for policies that enhance cybersecurity and digital resilience and participated in numerous public private partnerships to provide cybersecurity…
Read More“The potential reach of the scam is very troubling since one of the hijacked channels that began promoting the scams has 1.26 million subscribers,” the researchers said in the blog. “Other instances show a subscriber count of over 700,000 and in the lower ranges of 100,000.” Moreover, fake claims about Musk’s political affiliation may have…
Read MoreJul 18, 2024The Hacker NewsApp Security / Security Awareness Let’s face it: AppSec and developers often feel like they’re on opposing teams. You’re battling endless vulnerabilities while they just want to ship code. Sound familiar? It’s a common challenge, but there is a solution. Ever wish they proactively cared about security? The answer lies in…
Read MoreJul 18, 2024The Hacker NewsCybersecurity / Bot Attacks As the travel industry rebounds post-pandemic, it is increasingly targeted by automated threats, with the sector experiencing nearly 21% of all bot attack requests last year. That’s according to research from Imperva, a Thales company. In their 2024 Bad Bot Report, Imperva finds that bad bots accounted…
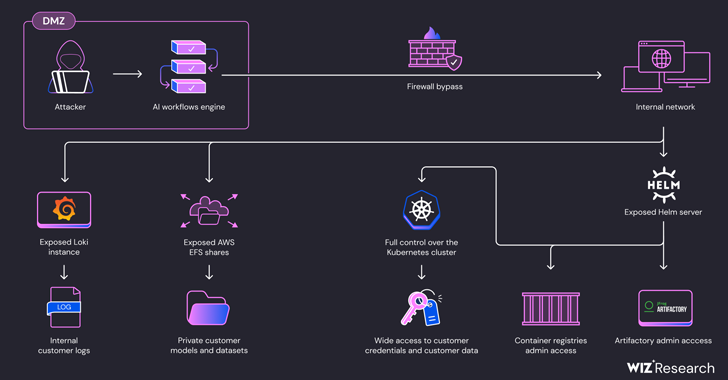
Read MoreJul 18, 2024NewsroomCloud Security / Enterprise Security Cybersecurity researchers have uncovered security shortcomings in SAP AI Core cloud-based platform for creating and deploying predictive artificial intelligence (AI) workflows that could be exploited to get hold of access tokens and customer data. The five vulnerabilities have been collectively dubbed SAPwned by cloud security firm Wiz. “The…
Read MoreWhen users then click on the rewritten link, the server runs a check to see if the link points to a known phishing or malware website and based on the result, either blocks access to it or redirects the request to the final destination. The benefit is that if a website is flagged as malicious…
Read MoreJul 18, 2024NewsroomArtificial Intelligence / Data Protection Meta has suspended the use of generative artificial intelligence (GenAI) in Brazil after the country’s data protection authority issued a preliminary ban objecting to its new privacy policy. The development was first reported by news agency Reuters. The company said it has decided to suspend the tools while…
Read MoreJul 18, 2024Newsroom Cisco has released patches to address a maximum-severity security flaw impacting Smart Software Manager On-Prem (Cisco SSM On-Prem) that could enable a remote, unauthenticated attacker to change the password of any users, including those belonging to administrative users. The vulnerability, tracked as CVE-2024-20419, carries a CVSS score of 10.0. “This vulnerability is…
Read MoreLimit access and federation between on-prem and cloud One should limit access and federation between on-premises and cloud assets where one can. Yes, we’ve built up reliance on this ability to share data and authentication between cloud assets and on-premises, but too often it’s also introducing weaknesses. A recent ProPublica article claims that a whistleblower…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks