Category: AI in news
American telecom service provider AT&T has confirmed that threat actors managed to access data belonging to “nearly all” of its wireless customers as well as customers of mobile virtual network operators (MVNOs) using AT&T’s wireless network. “Threat actors unlawfully accessed an AT&T workspace on a third-party cloud platform and, between April 14 and April 25,…
Read MoreCybersecurity Snapshot: CISA Tells Tech Vendors To Squash Command Injection Bugs, as OpenSSF Calls on Developers To Boost Security Skills
by nlqip
Check out CISA’s call for weeding out preventable OS command injection vulnerabilities. Plus, the Linux Foundation and OpenSSF spotlight the lack of cybersecurity expertise among SW developers. Meanwhile, GenAI deployments have tech leaders worried about data privacy and data security. And get the latest on FedRAMP, APT40 and AI-powered misinformation! Dive into six things that…
Read MoreSecurity intelligence firm Group-IB reports that attackers from a recently created ransomware group – EstateRansomware – exploited a year old vulnerability (CVE-2023-27532) in backup software from Veeam as part of a complex attack chain. Anatomy of an attack EstateRansomware exploited a dormant account in Fortinet FortiGate firewall SSL VPN appliances to gain initial access. After…
Read MoreThe phrase “may have been” signals that JAXA officials are still not certain what was and was not accessed. The agency also shared a cryptic comment that “In the course of taking the above measures and strengthening monitoring, we have detected and responded to multiple unauthorized accesses to JAXA’s network since January of this year—including…
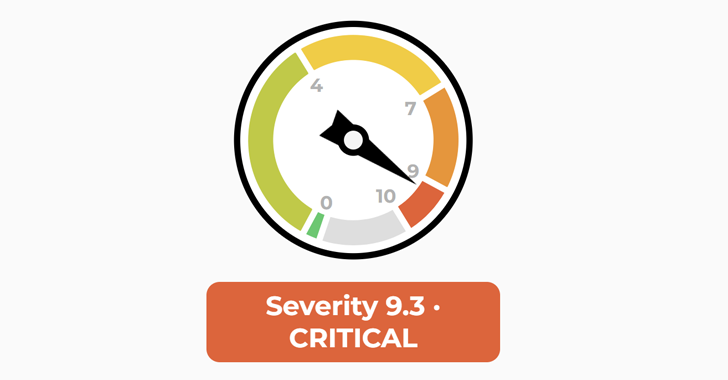
Read MoreJul 11, 2024NewsroomVulnerability / Enterprise Security Palo Alto Networks has released security updates to address five security flaws impacting its products, including a critical bug that could lead to an authentication bypass. Cataloged as CVE-2024-5910 (CVSS score: 9.3), the vulnerability has been described as a case of missing authentication in its Expedition migration tool that…
Read MoreApple Is Alerting iPhone Users of Spyware Attacks Not a lot of details: Apple has issued a new round of threat notifications to iPhone users across 98 countries, warning them of potential mercenary spyware attacks. It’s the second such alert campaign from the company this year, following a similar notification sent to users in 92…
Read MoreGoogle reportedly has walked away from a potentially massive deal to buy CRM provider HubSpot, a merger that would have helped Google Cloud. Google reportedly has abandoned its plans to acquire CRM specialist HubSpot, axing a potential deal that would have been worth billions and aided Google Cloud. HubSpot generated over $2 billion in revenue…
Read MoreExposed! The AI-enhanced social media bot farm that pumped out Kremlin propaganda on Twitter
by nlqip
The US Justice Department, working in coordination with Canadian and Dutch authorities, has seized two domain names which it claims were being used by Russian-backed hackers to spread disinformation on social media. The FBI has issued a joint cybersecurity advisory with its international partners, detailing the make-up of an AI-enhanced social media bot farm that…
Read MoreSmashing Security podcast #380: Teachers TikTok targeted, and fraud in the doctors’ waiting room
by nlqip
Execs at a health tech startup are sentenced to jail after a massive ad fraud, and a school is shaken after teachers are targeted via TikTok. All this and more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault. Plus don’t miss our featured interview…
Read MoreHow Risk-based Vulnerability Management Boosts Your Modern IT Environment’s Security Posture
by nlqip
Vulnerability assessments and vulnerability management sound similar – but they’re not. As a new Enterprise Strategy Group white paper explains, it’s key to understand their differences and to shift from ad-hoc vulnerability assessments to continuous, risk-based vulnerability management (RBVM). Read on to check out highlights from this Tenable-commissioned study and learn how RBVM helps organizations…
Read MoreRecent Posts
- Palo Alto Networks warns of critical RCE zero-day exploited in attacks
- Microsoft just killed the Windows 10 Beta Channel for good
- Cybersecurity Snapshot: Five Eyes Rank 2023’s Most Frequently Exploited CVEs, While CSA Publishes Framework for AI System Audits
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says