Category: AI in news
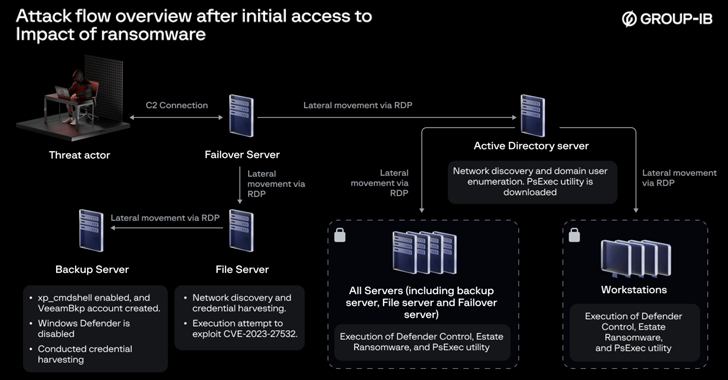
Jul 10, 2024NewsroomData Breach / Malware A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. Singapore-headquartered Group-IB, which discovered the threat actor in early April 2024, said the modus operandi involved the exploitation of CVE-2023-27532 (CVSS score: 7.5) to carry out the malicious…
Read MoreJul 10, 2024The Hacker NewsEndpoint Security / Identity Security It’s the age of identity security. The explosion of driven ransomware attacks has made CISOs and security teams realize that identity protection lags 20 years behind their endpoints and networks. This realization is mainly due to the transformation of lateral movement from fine art, found in…
Read MoreThe Problem The “2024 Attack Intelligence Report” from the staff at Rapid7 [1] is a well-researched, well-written report that is worthy of careful study. Some key takeaways are: 53% of the over 30 new vulnerabilities that were widely exploited in 2023 and at the start of 2024 were zero-days. More mass compromise events arose from…
Read MoreA covert Russian government-operated social media bot farm that used generative AI to spread disinformation to global users has been disrupted by a joint FBI-international cybersecurity forces operation. Affiliates of a Russian state-sponsored media organization Russia Today (RT), used Meliorator — an AI-enabled bot farm generation and management software–to set up over 1000 X (formerly…
Read MoreJul 10, 2024NewsroomOnline Scam / Blockchain Cryptocurrency analysts have shed light on an online marketplace called HuiOne Guarantee that’s widely used by cybercriminals in Southeast Asia, particularly those linked to pig butchering scams. “Merchants on the platform offer technology, data, and money laundering services, and have engaged in transactions totaling at least $11 billion,” Elliptic…
Read MoreDespite the SBOM’s conceptual attractiveness as a simple tool for spotting potentially problematic software components, its value is still too limited to be helpful. “What I’m seeing is that SBOM is too nascent for department and agency proactive use,” Rebecca McWhite, cyber supply chain risk management technical Lead at NIST, said during the CISA conference.…
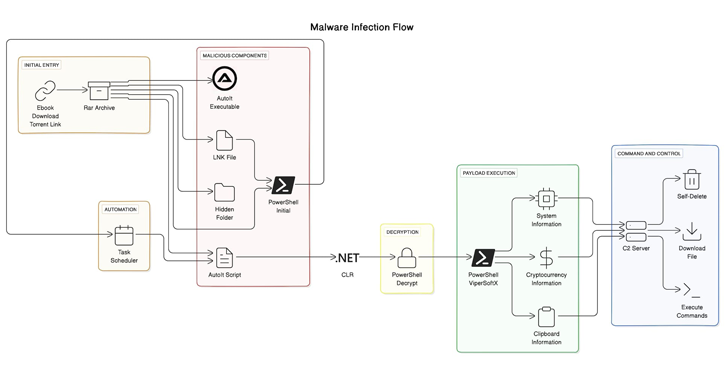
Read MoreJul 10, 2024NewsroomEndpoint Security / Threat Intelligence The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. “A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime (CLR) to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for…
Read MoreHe believes these dual-title roles can provide a more direct reporting line to the CEO or board, which is important for risk reporting. It gives the CISO greater autonomy to report to the board and helps them understand business risk because the CISO is looking across all the different parts of the organization. “It’s not…
Read MoreJul 10, 2024NewsroomVulnerability / Network Security Select versions of the OpenSSH secure networking suite are susceptible to a new vulnerability that can trigger remote code execution (RCE). The vulnerability, tracked as CVE-2024-6409 (CVSS score: 7.0), is distinct from CVE-2024-6387 (aka RegreSSHion) and relates to a case of code execution in the privsep child process due…
Read More“Prior to our work, there was no publicly-known attack exploiting MD5 to violate the integrity of the RADIUS/UDP traffic,” the researchers wrote in a blog post. “However, attacks continue to get faster, cheaper, become more widely available, and become more practical against real protocols. Protocols that we thought might be ‘secure enough,’ in spite of…
Read MoreRecent Posts
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist
- Here Are The Stellar Startup Edge Computing/IoT Vendors To Know In 2024
- Five Companies That Came To Win This Week
- Microsoft pulls Exchange security updates over mail delivery issues
- Palo Alto Networks warns of critical RCE zero-day exploited in attacks