Category: AI in news
OpenAI, headquartered in San Francisco, confirmed the breach to employees as well as the board of directors in April 2023 in an all-hands call but opted not to make it public. The company reasoned that no customer or partner data was compromised, and they believed the hacker was an individual, not a state-sponsored actor, the…
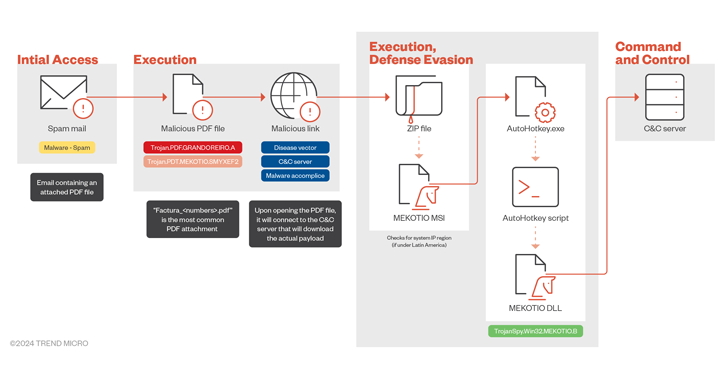
Read MoreJul 08, 2024NewsroomMalware / Cyber Threat Financial institutions in Latin America are being threatened by a banking trojan called Mekotio (aka Melcoz). That’s according to findings from Trend Micro, which said it recently observed a surge in cyber attacks distributing the Windows malware. Mekotio, known to be actively put to use since 2015, is known…
Read MoreTechnical debt can be described as an accumulation of fixes and outdated systems badly in need of updating. And infrastructure, because of the size and cost of building and maintaining public and private projects such as water systems, electrical grids, telecommunications systems, and transportation systems, is particularly prone to an accumulation of such debt. “Technical…
Read MoreFriday Squid Blogging: Newly Discovered Vampire Squid A new vampire squid species was discovered in the South China Sea. Blog moderation policy. Tags: squid Posted on July 5, 2024 at 5:39 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreThe researchers notified Intel of their research in February and the company has also notified other hardware and software vendors. The company already a mitigation for Spectre-like attacks in 2018 called the indirect branch predictor barrier (IBPB). While this in theory can be used to mitigate the new Indirector attack techniques, it would have to…
Read MoreWith growing concern over the recently disclosed regreSSHion vulnerability, we’re explaining here what it is, why it’s so significant, what it could mean for your cloud environment and how Tenable Cloud Security can help. The newly discovered CVE-2024-6387 vulnerability in OpenSSH, named “regreSSHion,” is a critical remote code execution (RCE) flaw resulting from a race…
Read MoreJul 05, 2024The Hacker NewsCybersecurity / Identity Protection Identity theft isn’t just about stolen credit cards anymore. Today, cybercriminals are using advanced tactics to infiltrate organizations and cause major damage with compromised credentials. The stakes are high: ransomware attacks, lateral movement, and devastating data breaches. Don’t be caught off guard. Join us for a groundbreaking…
Read MoreCybersecurity Snapshot: Malicious Versions of Cobalt Strike Taken Down, While Microsoft Notifies More Orgs About Midnight Blizzard Email Breach
by nlqip
Check out the results of a multinational operation against illegal instances of Cobalt Strike. Plus, more organizations are learning that Midnight Blizzard accessed their email exchanges with Microsoft. Meanwhile, Carnegie Mellon has a new report about how to fix and mitigate API vulnerabilities. And two new reports shed light on cyber insurance trends. And much…
Read MoreWhen matched, the company said it found 81 email addresses in the exported mailing list that were not part of the threat actor’s own list. Phished to a crypto drainer The phishing emails posed as an announcement claiming that the Ethereum Foundation had teamed up with the Lido decentralized autonomous organization (LidoDAO) to provide a…
Read MoreJul 05, 2024The Hacker NewsCloud Security / Attack Surface The attack surface isn’t what it once was and it’s becoming a nightmare to protect. A constantly expanding and evolving attack surface means risk to the business has skyrocketed and current security measures are struggling to keep it protected. If you’ve clicked on this article, there’s…
Read MoreRecent Posts
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist
- Here Are The Stellar Startup Edge Computing/IoT Vendors To Know In 2024