Category: AI in news
Jul 04, 2024NewsroomData Breach / Mobile Security Cloud communications provider Twilio has revealed that unidentified threat actors took advantage of an unauthenticated endpoint in Authy to identify data associated with Authy accounts, including users’ cell phone numbers. The company said it took steps to secure the endpoint to no longer accept unauthenticated requests. The development…
Read MoreIn episode four of The AI Fix podcast, Graham and Mark learn there’s a 99.9% chance that AI will wipe out humans within 100 years, examine the even more chilling prospect of Barney the dinosaur reading Adolf Hitler’s Mein Kampf to six-year-olds, and resurrect a tried-and-trusted software evaluation method to decide if Claude 3.5 Sonnet…
Read MoreApps can let you spy on strangers in bars, a gang of cryptocurrency thieves turns to kidnap and assault, and have you joined the mile-high evil twin club? All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault, joined this…
Read MoreIf you can answer this question, you’re smarter than 99% of AIs: “Alice has 4 brothers, and she also has 1 sister. How many sisters do Alice’s brothers have?” Find out why AI is stupid, what Toys “R” Us has done that’s even more annoying than putting that “R” in its name, why Graham Cluley…
Read MoreMost accomplished cybercriminals go out of their way to separate their real names from their hacker handles. But among certain old-school Russian hackers it is not uncommon to find major players who have done little to prevent people from figuring out who they are in real life. A case study in this phenomenon is “x999xx,”…
Read MoreNew Open SSH Vulnerability It’s a serious one: The vulnerability, which is a signal handler race condition in OpenSSH’s server (sshd), allows unauthenticated remote code execution (RCE) as root on glibc-based Linux systems; that presents a significant security risk. This race condition affects sshd in its default configuration. […] This vulnerability, if exploited, could lead…
Read MoreFrom the editors of our sister publication Computerworld, this vendor comparison chart helps IT and security staff understand what the major unified endpoint management (UEM) platforms can do for their organizations to help choose the right solution. Source link lol
Read MoreJul 03, 2024The Hacker NewsOSINT / Artificial Intelligence Recently the Office of the Director of National Intelligence (ODNI) unveiled a new strategy for open-source intelligence (OSINT) and referred to OSINT as the “INT of first resort”. Public and private sector organizations are realizing the value that the discipline can provide but are also finding that…
Read More“We used the standard GitHub phishlet that can be found in various user repositories on GitHub itself,” Stewart said. “When the targeted user visits the lure URL, other than the hostname in the URL bar, what they will see looks just like the normal GitHub login page, because it is the actual GitHub login page,…
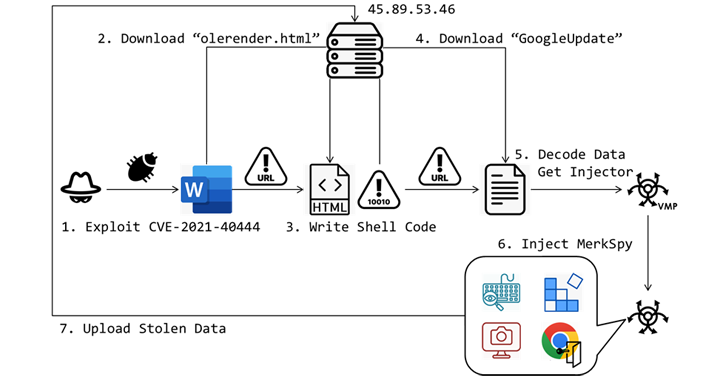
Read MoreJul 03, 2024NewsroomSpyware / Vulnerability Unknown threat actors have been observed exploiting a now-patched security flaw in Microsoft MSHTML to deliver a surveillance tool called MerkSpy as part of a campaign primarily targeting users in Canada, India, Poland, and the U.S. “MerkSpy is designed to clandestinely monitor user activities, capture sensitive information, and establish persistence…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist