Category: AI in news
The controversial spyware Pegasus and its operator, the Israeli NSO Group, is once again in the news. Last week, in documents filed in a judgment between NSO and WhatsApp, they admitted that any of their clients can target anyone with their spyware, including government or military officials because their jobs are inherently legitimate intelligence targets.…
Read MoreJun 19, 2024NewsroomCybercrime / Crypto Security Crypto exchange Kraken revealed that an unnamed security researcher exploited an “extremely critical” zero-day flaw in its platform to steal $3 million in digital assets and refused to return them. Details of the incident were shared by Kraken’s Chief Security Officer, Nick Percoco, on X (formerly Twitter), stating it…
Read MoreJun 19, 2024NewsroomZero-Day Exploits / Cyber Espionage The China-nexus cyber espionage actor linked to the zero-day exploitation of security flaws in Fortinet, Ivanti, and VMware devices has been observed utilizing multiple persistence mechanisms in order to maintain unfettered access to compromised environments. “Persistence mechanisms encompassed network devices, hypervisors, and virtual machines, ensuring alternative channels remain…
Read MoreWhile AMD confirmed that it is investigating the alleged breach, IntelBroker has posted previews of stolen data that include employee database, customer database, source codes, and firmware data. Sensitive data offered in exchange for crypto In the post on Breach Forums, IntelBroker outlined the extent of the data breach, claiming to have accessed various types…
Read MoreJun 19, 2024The Hacker NewsGDPR Compliance / Data Privacy Are your tags really safe with Google Tag Manager? If you’ve been thinking that using GTM means that your tracking tags and pixels are safely managed, then it might be time to think again. In this article we look at how a big-ticket seller that does…
Read MoreThe Hacking of Culture and the Creation of Socio-Technical Debt Culture is increasingly mediated through algorithms. These algorithms have splintered the organization of culture, a result of states and tech companies vying for influence over mass audiences. One byproduct of this splintering is a shift from imperfect but broad cultural narratives to a proliferation of…
Read MoreJun 19, 2024NewsroomMalware / Cyber Attack Chinese-speaking users are the target of a never-before-seen threat activity cluster codenamed Void Arachne that employs malicious Windows Installer (MSI) files for virtual private networks (VPNs) to deliver a command-and-control (C&C) framework called Winos 4.0. “The campaign also promotes compromised MSI files embedded with nudifiers and deepfake pornography-generating software,…
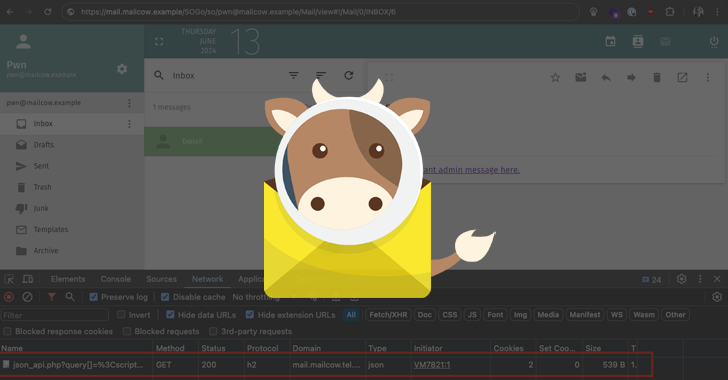
Read MoreJun 19, 2024NewsroomEmail Security / Vulnerability Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that could be exploited by malicious actors to achieve arbitrary code execution on susceptible instances. Both shortcomings impact all versions of the software prior to version 2024-04, which was released on April 4, 2024. The issues…
Read MoreCould separation of certain functions improve risk management? In other circumstances, it makes sense to have a head of cybersecurity to lead the technical, operations and architecture teams, and a CISO to lead governance, risk, and compliance functions, according to Chirag Joshi, CISO and founder of 7 Rules Cyber consultancy. “The governance and risk role…
Read MoreData breach at Total Fitness exposed almost half a million people’s photos – no password required
by nlqip
UK-based gym chain Total Fitness has been accused of sloppy security, following the discovery of an unsecured database containing the images of 470,000 members and staff – all accessible to anyone on the internet, no password required. A 47.7GB database belonging to the health club was discovered by cybersecurity researcher Jeremiah Fowler, who told The…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist