Category: AI in news
The UPX-packed ELF, apart from DSOP.pdf, has the DISGOMOJI malware payload which, upon execution, reads and exfiltrates system information including IP address, username, hostname, operating system, and the current working directory. Apart from the main functions, DISGOMOJI also downloads a shell script uevent_seqnum.sh, to check for connected USB devices and copy the content of those…
Read MoreUsing LLMs to Exploit Vulnerabilities Interesting research: “Teams of LLM Agents can Exploit Zero-Day Vulnerabilities.” Abstract: LLM agents have become increasingly sophisticated, especially in the realm of cybersecurity. Researchers have shown that LLM agents can exploit real-world vulnerabilities when given a description of the vulnerability and toy capture-the-flag problems. However, these agents still perform poorly…
Read MoreOn the morning of August 30, 2023, a fire broke out at a data center operated by Belgian telecom giant Proximus. Soon, emergency numbers 112, 101, and 100, which are used to call the ambulance, the firefighters, and the police, became unreachable. The situation lasted for almost half an hour before these essential services were…
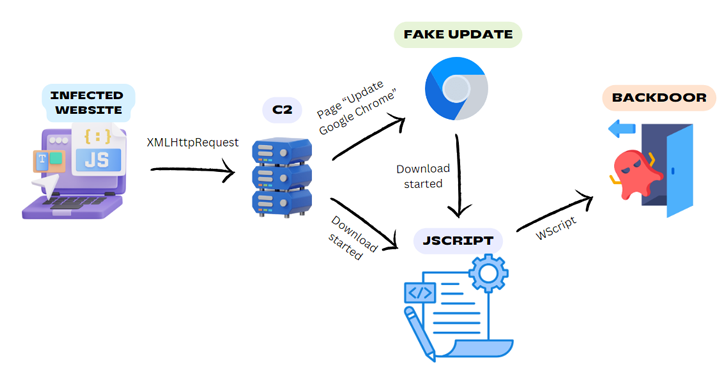
Read MoreJun 17, 2024NewsroomWeb Security / Malware Legitimate-but-compromised websites are being used as a conduit to deliver a Windows backdoor dubbed BadSpace under the guise of fake browser updates. “The threat actor employs a multi-stage attack chain involving an infected website, a command-and-control (C2) server, in some cases a fake browser update, and a JScript downloader…
Read MorePerhaps the best way to understand the approach is with an analogy about childhood learning. When we tell toddlers about numbers, they have no idea about how they drive complex human activities (statistical analysis, for instance). Instead, numbers are words learned perhaps by memorizing a song that uses them ( “One, Two, Buckle My Shoe”).…
Read MoreJun 17, 2024NewsroomBotnet / Cryptocurrency Threat actors have been observed deploying a malware called NiceRAT to co-opt infected devices into a botnet. The attacks, which target South Korean users, are designed to propagate the malware under the guise of cracked software, such as Microsoft Windows, or tools that purport to offer license verification for Microsoft…
Read MoreAs if CSOs didn’t have enough to worry about, how about upwards of four million more ways that cybercriminals could affect businesses — and society in general — through attacks on spacecraft and the infrastructure that develops, launches, and supports them? That’s what a new study from the Ethics + Emerging Sciences Group at California…
Read MoreJun 16, 2024NewsroomCybercrime / SIM Swapping Law enforcement authorities have allegedly arrested a key member of the notorious cybercrime group called Scattered Spider. The individual, a 22-year-old man from the United Kingdom, was arrested this week in the Spanish city of Palma de Mallorca as he attempted to board a flight to Italy. The move…
Read MoreJun 15, 2024Newsroom Pakistan has become the latest target of a threat actor called the Smishing Triad, marking the first expansion of its footprint beyond the E.U., Saudi Arabia, the U.A.E., and the U.S. “The group’s latest tactic involves sending malicious messages on behalf of Pakistan Post to customers of mobile carriers via iMessage and…
Read MoreJun 15, 2024NewsroomCyber Espionage / Malware A suspected Pakistan-based threat actor has been linked to a cyber espionage campaign targeting Indian government entities in 2024. Cybersecurity company Volexity is tracking the activity under the moniker UTA0137, noting the adversary’s exclusive use of a malware called DISGOMOJI that’s written in Golang and is designed to infect…
Read MoreRecent Posts
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021