Category: AI in news
Jun 11, 2024The Hacker NewsEndpoint Security / Incident Response Managed service providers (MSPs) are on the front lines of soaring demand for cybersecurity services as cyberattacks increase in volume and sophistication. Cynet has emerged as the security vendor of choice for MSPs to capitalize on existing relationships with SMB clients and profitably expand their client…
Read MoreIn a previous blog, we discussed how the “businessification” of cybercrime has coalesced around tried and true tools, techniques, and procedures, giving us a solid understanding of how these attacks happen. Security product vendors have made massive strides in developing capabilities to detect criminals carrying out their attacks; however, it’s not a perfect solution. If…
Read MoreAttackers are easily sidestepping endpoint detection and response (EDR) and extended detection and response (XDR) defenses, often catching enterprises unaware, according to a new study of cybersecurity threats. The study of global cyberthreats, by EDR/XDR vendor Trellix, highlighted the danger posed by the emergence of “EDR killer tools” and their use to deliver ransomware or…
Read MoreLLMs Acting Deceptively New research: “Deception abilities emerged in large language models“: Abstract: Large language models (LLMs) are currently at the forefront of intertwining AI systems with human communication and everyday life. Thus, aligning them with human values is of great importance. However, given the steady increase in reasoning abilities, future LLMs are under suspicion…
Read MoreJun 11, 2024NewsroomCloud Computing / Artificial Intelligence Apple has announced the launch of a “groundbreaking cloud intelligence system” called Private Cloud Compute (PCC) that’s designed for processing artificial intelligence (AI) tasks in a privacy-preserving manner in the cloud. The tech giant described PCC as the “most advanced security architecture ever deployed for cloud AI compute…
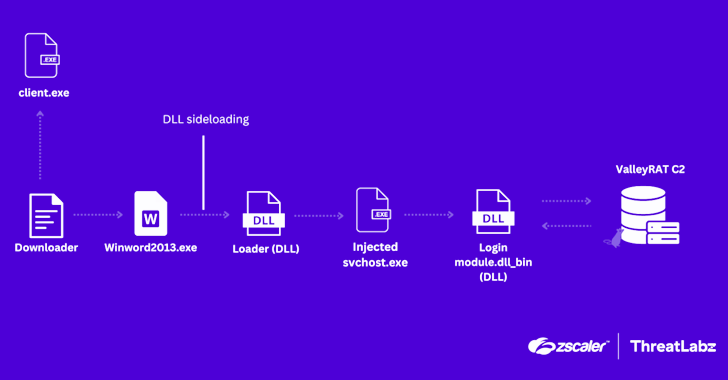
Read MoreJun 11, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that’s being distributed as part of a new campaign. “In the latest version, ValleyRAT introduced new commands, such as capturing screenshots, process filtering, forced shutdown, and clearing Windows event logs,” Zscaler ThreatLabz researchers Muhammed Irfan V A and…
Read MoreJun 11, 2024NewsroomData Theft / Cloud Security As many as 165 customers of Snowflake are said to have had their information potentially exposed as part of an ongoing campaign designed to facilitate data theft and extortion, indicating the operation has broader implications than previously thought. Google-owned Mandiant, which is assisting the cloud data warehousing platform…
Read MoreA failure to consider cybersecurity when it comes to engaging in an M&A deal, as Winzer put it, is like driving blind without any mirrors. “You can be very easily attacked and become prey to cyber attackers, and if that were to happen what’s at stake is business operations, being able to run the company…
Read MoreInformation security analyst/administrator Information assurance security officer Information security manager/specialist Information systems security engineer/manager Information security professionals/officers Information security/IT auditors Risk/threat/vulnerability analyst System administrators Network administrators and engineers This is, of course, over and above jobs that actually have “ethical hacker” or “penetration testing” or the like in their title, which are more glamorous but…
Read MoreUnsanitized RPC function calls The vulnerability is located in PyTorch’s distributed Remote Procedure Call (RPC) component, torch.distributed.rpc. The component facilitates inter-process communication between the various nodes involved in distributed training scenarios, in which a task is distributed between multiple deployments that function as workers and is controlled from a master node. When using RPC, workers…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’