Category: AI in news
Cloud security challenges are growing. Here’s why traditional SOC tools are failing to address them
by nlqip
The cloud will become a cornerstone of enterprise operations as IDC estimates that by 2025, there will be over 750 million cloud-native applications globally. Additionally, over 90% of organizations anticipate employing a multi-cloud approach over the next few years. Considering the cloud offers unparalleled flexibility, scalability, and agility, these numbers should be unsurprising. However, the…
Read MorePax8, GuidePoint Security, Zones, AWS, Oracle and Salesforce were among the tech companies making key executive hires and moves during May 2024. Pax8’s new CEO. A new CMO at GuidePoint Security. And Zones’ new chief commercial officer. Scott Chasin, formerly with ProtectWise; Rachel Haag, formerly of Workato; and Neal Campbell, formerly of CDW, were some…
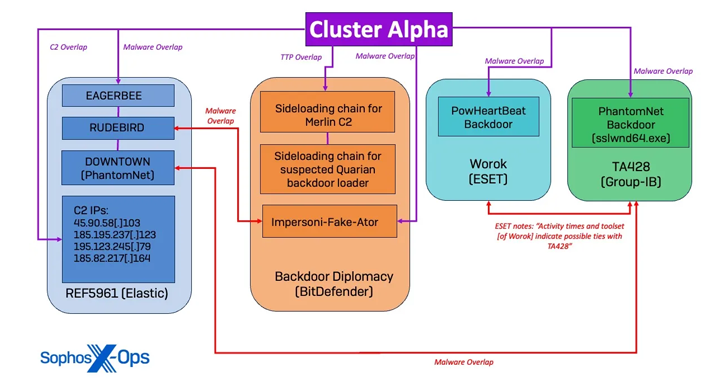
Read MoreJun 05, 2024NewsroomCyber Espionage / Threat Intelligence An unnamed high-profile government organization in Southeast Asia emerged as the target of a “complex, long-running” Chinese state-sponsored cyber espionage operation codenamed Crimson Palace. “The overall goal behind the campaign was to maintain access to the target network for cyberespionage in support of Chinese state interests,” Sophos researchers…
Read More“The NtQuerySystemInformation function allows the caller to obtain information about the current system’s physical details such as the number of logical processors available,” Arctic Wolf said. “This information can be useful when determining how many threads the multi-threaded encryption routine should allocate.” Once critical system information is obtained, encryption is attempted. “Using the system information…
Read MoreOnline Privacy and Overfishing Microsoft recently caught state-backed hackers using its generative AI tools to help with their attacks. In the security community, the immediate questions weren’t about how hackers were using the tools (that was utterly predictable), but about how Microsoft figured it out. The natural conclusion was that Microsoft was spying on its…
Read MoreJun 05, 2024NewsroomVulnerability / Data Security Zyxel has released security updates to address critical flaws impacting two of its network-attached storage (NAS) devices that have currently reached end-of-life (EoL) status. Successful exploitation of three of the five vulnerabilities could permit an unauthenticated attacker to execute operating system (OS) commands and arbitrary code on affected installations.…
Read MoreJun 05, 2024NewsroomCyber Attack / Online Security Popular video-sharing platform TikTok has acknowledged a security issue that has been exploited by threat actors to take control of high-profile accounts on the platform. The development was first reported by Semafor and Forbes, which detailed a zero-click account takeover campaign that allows malware propagated via direct messages…
Read MoreNearly 83% of all legal documents shared with AI tools go through non-corporate accounts, the report adds, while about half of all source code, R&D materials, and HR and employee records go into unauthorized AIs. The amount of data put into all AI tools saw nearly a five-fold increase between March 2023 and March 2024,…
Read MoreMaryland-based security firm Analygence has landed the job of helping the National Institute of Standards and Technology (NIST) reduce mounting backlog of entries in the US National Vulnerability Database (NVD), an agency representative said Tuesday. “I can confirm that Analygence, Inc. won a competitive task order for processing support for incoming CVEs for inclusion in…
Read MoreSpending on worldwide public cloud services is expected to reach $219 billion by 2027, according to new data from IDC, benefiting cloud leaders Amazon Web Services, Google Cloud and Microsoft. The market research firm said spending on public cloud services will continue to grow by billions of dollars annually over the next three years as…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’