Category: Chatgpt
Access Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/enhancing-cyber-resilience-in-the-financial-services-industry” on this server. Reference #18.dbd7ce17.1728474593.34b6d32a https://errors.edgesuite.net/18.dbd7ce17.1728474593.34b6d32a Source link lol
Read MoreComplyAuto
by nlqip
MS-ISAC ADVISORY NUMBER: 2024-112 DATE(S) ISSUED: 10/08/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Adobe products, the most severe of which could allow for arbitrary code execution. Adobe is a software that is used for creating and publishing a wide variety of contents including graphics, photography, illustration, animation, multimedia, motion pictures and print. Successful…
Read MoreAva Smithing was eleven when she saw a swimsuit on Pinterest that she liked. That innocent click turned into an eating disorder. How? This episode explores the most dangerous thing children face today: Algorithms. On a mission to hold Big Tech accountable, Ava shares her journey as an activist with us, including her recent role…
Read MoreTenable Cloud Risk Report Sounds the Alarm on Toxic Cloud Exposures Threatening Global Organizations
by nlqip
Tenable®, the exposure management company, today released its 2024 Tenable Cloud Risk Report, which examines the critical risks at play in modern cloud environments. Most alarmingly, nearly four in 10 organizations globally are leaving themselves exposed at the highest levels due to the “toxic cloud triad” of publicly exposed, critically vulnerable and highly privileged cloud…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/reducing-alert-fatigue-by-streamlining-soc-processes” on this server. Reference #18.e4d7ce17.1728295785.a3bbc129 https://errors.edgesuite.net/18.e4d7ce17.1728295785.a3bbc129 Source link lol
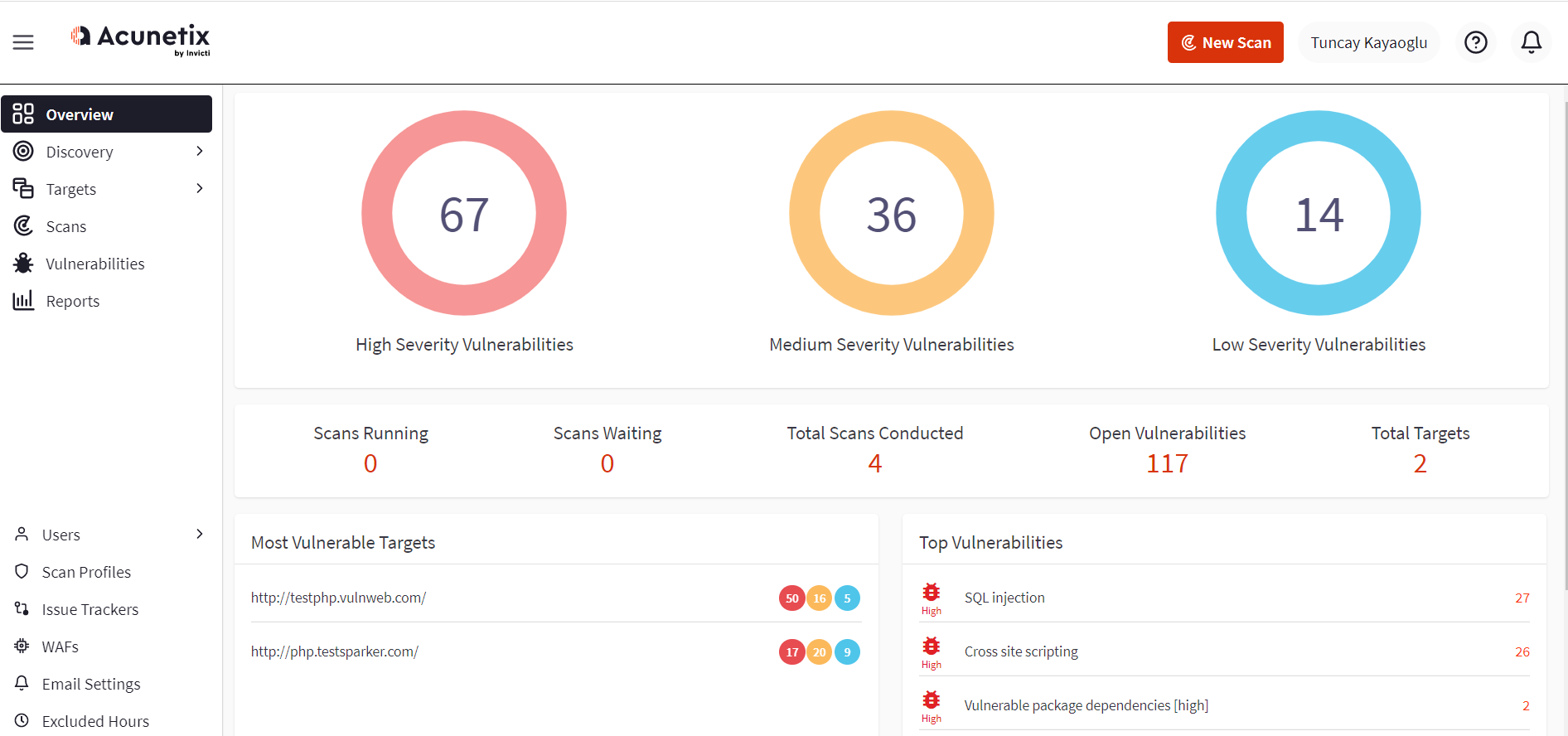
Read MoreDAST vulnerability scanners are not that different from virus scanners. In both cases, the goal of the software is to find something out of the ordinary in the target. A virus scanner scans a computer’s local resources and storage to find potentially malicious software. A vulnerability scanner scans some kind of target to find potentially…
Read More3 reasons why DAST is the best way to begin the web application security journey | Acunetix
by nlqip
To fully secure your web applications, you need several software solutions, specialist internal resources, and external contractors. However, this means significant costs, and not everyone can afford it all at once. How should small businesses start their web application security journey? Let’s have a look at your options and the reasons why DAST is a…
Read MoreAcunetix releases support for RHEL 9, updates CWE report, and improves PHP IAST AcuSensor | Acunetix
by nlqip
A new Acunetix Premium update has been released for Windows and Linux: 15.0.221007170. This Acunetix release introduces support for Red Hat Enterprise Linux (RHEL) 9, which has been released earlier this year. The PHP IAST AcuSensor can now be used with web applications that take advantage of the PHP Slim Framework, and has been updated…
Read MoreA new Acunetix Premium update has been released for Windows and Linux: 15.1 This Acunetix release updates its user interface and the notifications list. The user interface features a new navigation menu, which prioritizes features based on how frequently you may need them. The most frequently used features appear on the top while the rest…
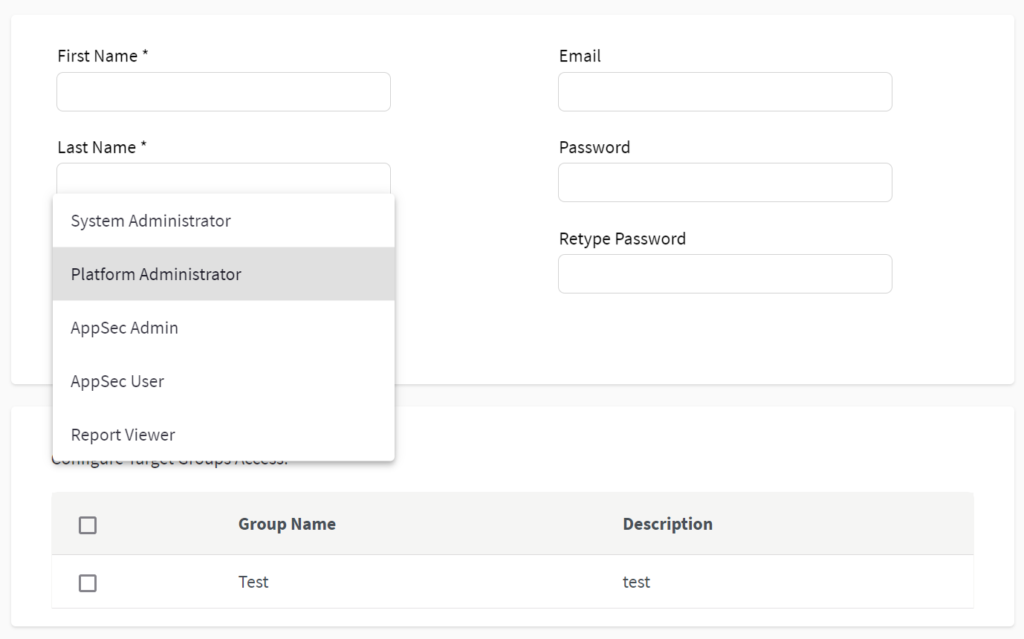
Read MoreA new Acunetix Premium update has been released for Windows and Linux: 15.4 This Acunetix release improves the default roles. Acunetix offers role-based access control (RBAC) to efficiently manage user access. Thanks to RBAC, you can limit or authorize user access to Acunetix based on the user’s specific role. This release brings improvements to user roles.…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA