Category: Chatgpt
This Acunetix release introduces a new security check for the Fortinet RCE flaw (CVE-2022-39952). The FortiNAC, a network security solution, was discovered to have a vulnerability with a high CVSS score of 9.8, known as CVE-2022-39952. Fortinet disclosed the security issue on February 16. The issue can be exploited by an unauthorized user to write…
Read MoreA new Acunetix Premium update has been released for Windows and Linux: 15.7 We are sunsetting the support for Windows 8, Server 2012, and Server 2012 R2. To provide you with the best DAST product experience, we regularly update Acunetix. As a result of these updates and changes, we are required to sunset our support…
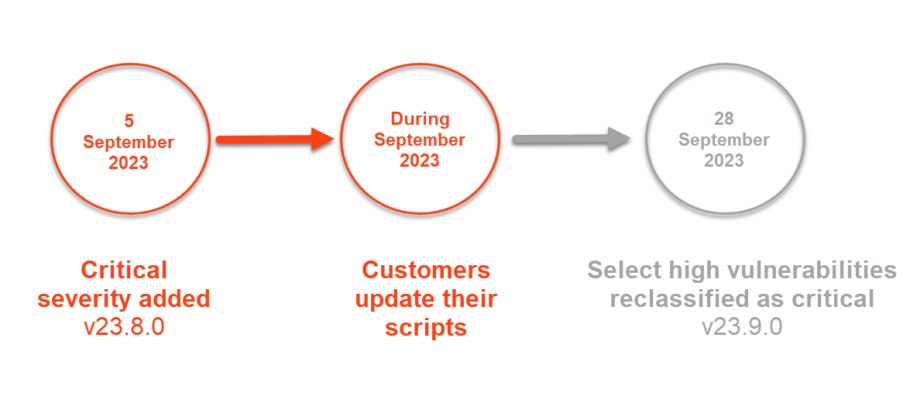
Read MoreWith the release of Acunetix Standard and Acunetix Premium versions 23.8 and 23.9 comes the addition of critical severity as a new vulnerability classification. Find out which vulnerabilities have changed to critical here. What’s changing? Our vulnerability classification system (High-Medium-Low) has expanded to include a fourth threat level — Critical Severity. On 5 September 2023,…
Read MoreAll announcements about Acunetix product updates and new releases are now exclusively available on our changelogs page. For each release, we publish notes to announce new features, new security checks, improvements, and bug fixes. Information about our latest product updates and previous release notes are available on the links below according to your Acunetix product:…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-107 DATE(S) ISSUED: 10/01/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution. Mozilla Firefox is a web browser used to access the Internet. Mozilla Firefox ESR is a version of the web browser intended to be deployed in large…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-109 DATE(S) ISSUED: 10/02/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/levelblue-driving-cyber-resilience-in-october-and-beyond” on this server. Reference #18.dad7ce17.1727964132.319391c3 https://errors.edgesuite.net/18.dad7ce17.1727964132.319391c3 Source link lol
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/demand-great-cybersecurity-troubleshooting-skills-going-back-to-the-basics” on this server. Reference #18.dfd7ce17.1727863258.9fcca058 https://errors.edgesuite.net/18.dfd7ce17.1727863258.9fcca058 Source link lol
Read MoreFrom cyberbullying to harmful algorithms, the risks are real. This week, Senators Marsha Blackburn and Richard Blumenthal join us to discuss their bipartisan bill—the Kids Online Safety Act (KOSA). Together, they’re taking on Big Tech to ensure the safety of children online. Tune in to hear how KOSA could change the digital world for the…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/people-know-their-data-rights-and-theyre-here-to-play-ball” on this server. Reference #18.ded7ce17.1727776852.80fe52ca https://errors.edgesuite.net/18.ded7ce17.1727776852.80fe52ca Source link lol
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA