Category: Chatgpt
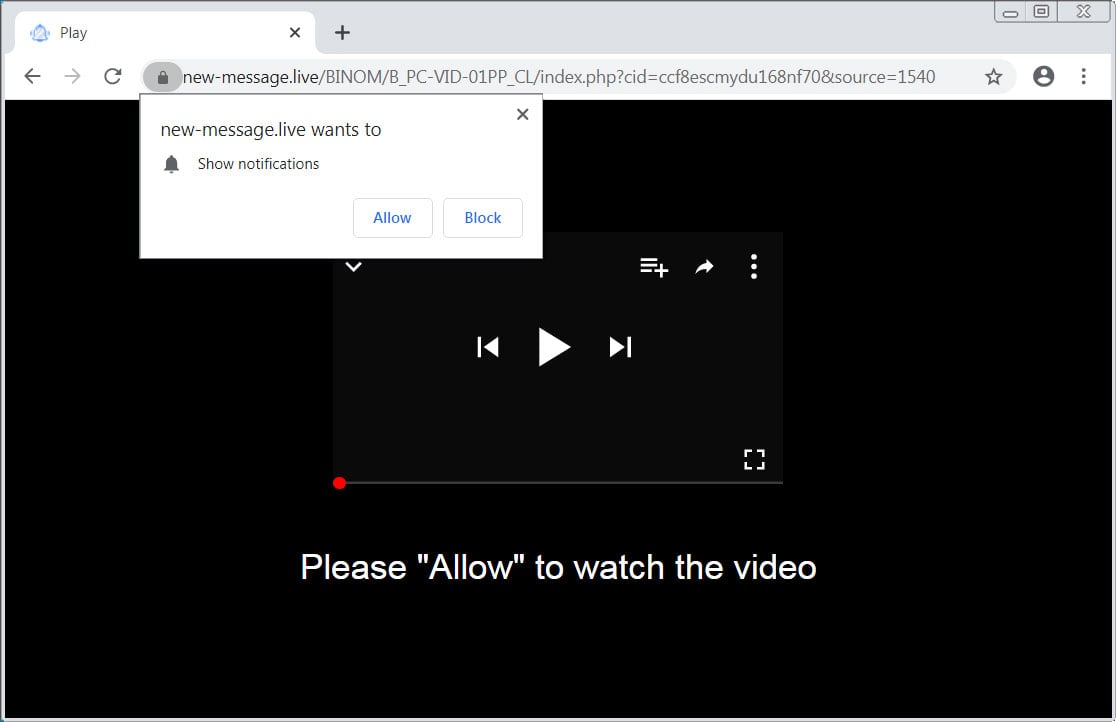
In order to remove Please Allow to watch the video Notification Page completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed…
Read MoreCyber security breaches have become rapidly one of the main concerns among all kinds of organizations. Even though companies are investing in complex new solutions against undesired guests, the task has never been easier. The various backdoors, loose ends and interconnected computer systems, mean that these intrusions are sometimes… inevitable. If unfortunately that happens, companies…
Read MoreTenable Ranks #1 for Fifth Consecutive Year in Market Share in Device Vulnerability Management
by nlqip
Tenable®, the Exposure Management company, today announced that it has been ranked first for 2022 worldwide market share for device vulnerability management in the IDC Worldwide Device Vulnerability Management Market Shares Exposures Present a Clear and Present Danger (doc #US50271923, December 2023) report. This is the fifth consecutive year Tenable has been ranked first, increasing its…
Read MoreIntroduction Much of the activity on the internet is automated, and quite a lot of it is specifically due to bots. Bots can be used for many purposes, but in this series of articles we’ll be looking at bots that create and use fake accounts. This first article looks at the motivations behind fake account…
Read MoreIn an interview with CRN, Intel’s Jason Kimrey says the Intel Partner Alliance Partner of the Year Awards recognize those are who not only driving revenue growth but who are also building innovative solutions and business models on top of embracing the chipmaker’s AI strategy. Intel has announced its top 27 partners in the Americas…
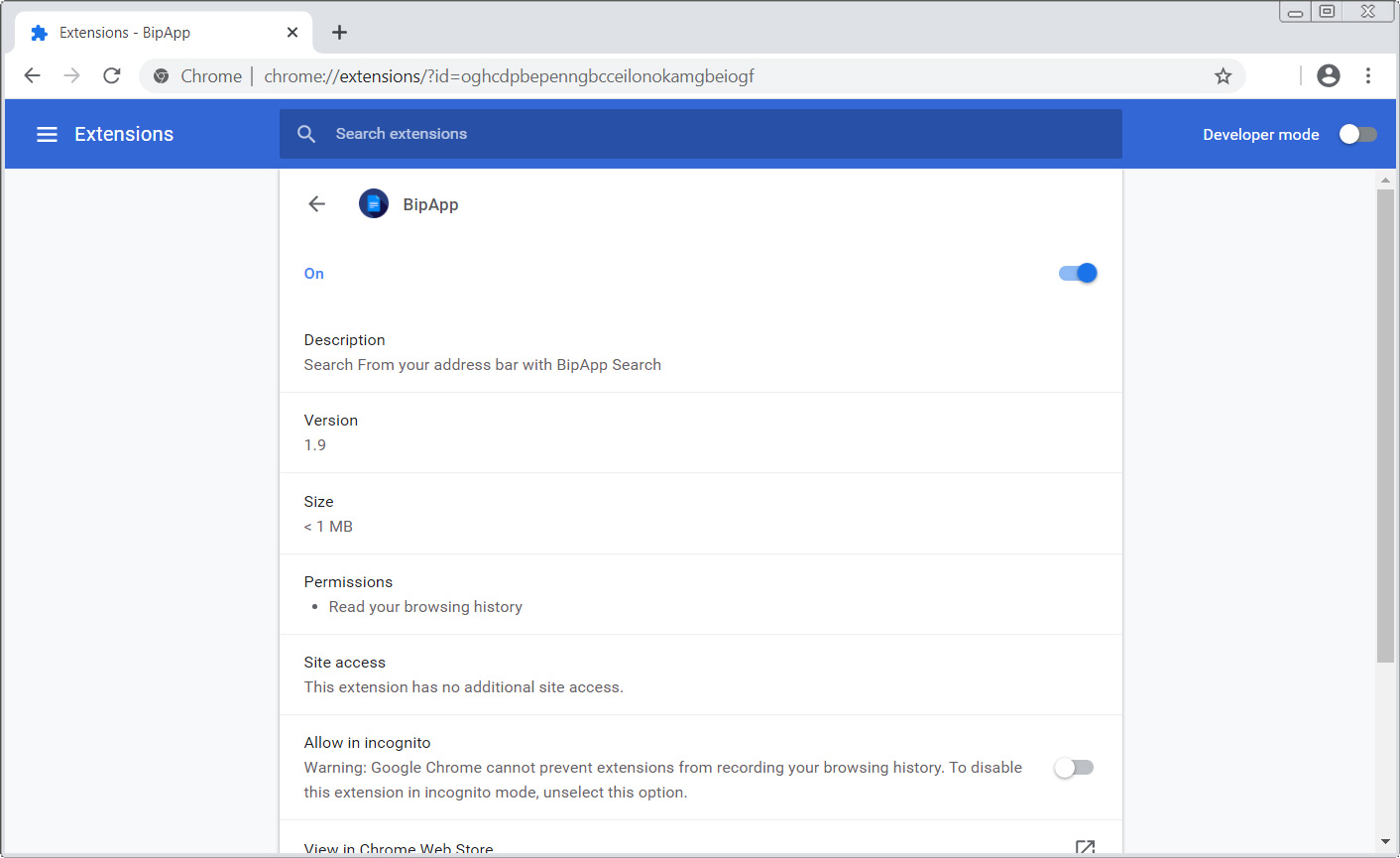
Read MoreIn order to remove BipApp Chrome Extension completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed extensions. All of your bookmarks,…
Read MoreBlockchain Security: The Theory and The Facts In whatever place we look at we always read the same story: how Blockchain is a new technology offering trust and security due to the way it is structured. But is that so? Is blockchain really so hacker proof as it praises itself to be? When we look…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. With the rise of remote and flexible work arrangements, Bring Your Own Device (BYOD) programs that allow employees to use their personal devices…
Read MoreTenable Introduces Groundbreaking Visibility Across IT, OT and IoT Domains to Fully Illuminate Attack Vectors and Risks
by nlqip
Tenable®, the Exposure Management company, today announced the release of Tenable One for OT/IoT. It is the first and only exposure management platform that provides holistic visibility into assets across IT and operational technology (OT) environments. The convergence of physical assets and IT – such as HVAC systems in data centers, badge readers in office buildings, cameras…
Read MoreIn part two of this multi-part series on fake account creation bots, we look at why automation is used to create fake accounts and how they impact businesses. What is a Fake Account Creation Bot? A fake account creation bot is an automated computer program designed to create large numbers of fake accounts inside online…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA