Category: Good news
A Vulnerability in Atlassian Confluence Data Center and Server Could Allow for Remote Code Execution
by nlqip
Apply appropriate patches and workarounds provided by Atlassian to vulnerable systems, immediately after appropriate testing. (M1051: Update Software)o Safeguard 7.1: Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard.o Safeguard…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreIntroduction As stories of electronic fraud fill the daily news, we’re still answering the question “What is phishing?” In 2020, it continues to be one of the most prevalent attack types, so let’s look at what phishing is, why it is so successful, and what you can do to avoid becoming a victim. What…
Read MorePowerHouse Data Centers launched in 2022. It is owned by American Real Estate Partners. Its two newest projects in Reno and Viriginia are supported by $1 billion investment from Harrison Street JV. PowerHouse Data Centers has two massive projects underway to begin the new year, with a three-building site under development in Reno, Nevada, as…
Read MoreTABLACUSAPP.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have running on your computer. This consists of programs that are misleading, harmful, or undesirable. If the description states that it is a piece of malware, you should immediately run an antivirus and antispyware program. If…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-007 DATE(S) ISSUED: 01/18/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Oracle products, the most severe of which could allow for remote code execution. SYSTEMS AFFECTED: Fujitsu M10-1, M10-4, M10-4S, M12-1, M12-2, M12-2S Servers, versions prior to XCP2430, prior to XCP3130, prior to XCP4040 GoldenGate Big Data and Application Adapters, versions 19.1.0.0.0-19.1.0.0.16,…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreWhat Is the Principle of Least Privilege? Information security is a complex, multifaceted discipline built upon many foundational principles. The three most important—confidentiality, integrity, and availability (the CIA triad)—are considered the goals of any information security program. A supporting principle that helps organizations achieve these goals is the principle of least privilege. The principle of…
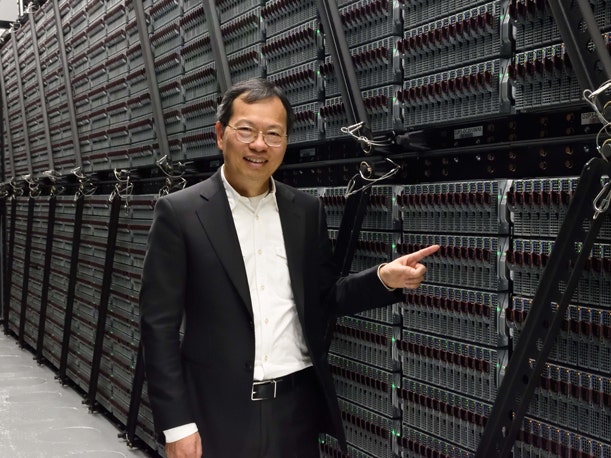
Read More‘Sometimes I like to compare the AI revolution with the Industrial Revolution of 200 years ago. I personally believe this AI revolution impact to our planet can be even bigger than the industrial revolution because AI impacts our lives in everything, both visible and invisible. So the impact will be everywhere,’ says Supermicro Founder, President,…
Read MoreSHADOWSOCKSS Information This is an undesirable program. This file has been identified as a program that is undesirable to have running on your computer. This consists of programs that are misleading, harmful, or undesirable. If the description states that it is a piece of malware, you should immediately run an antivirus and antispyware program. If…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA