Category: Viral
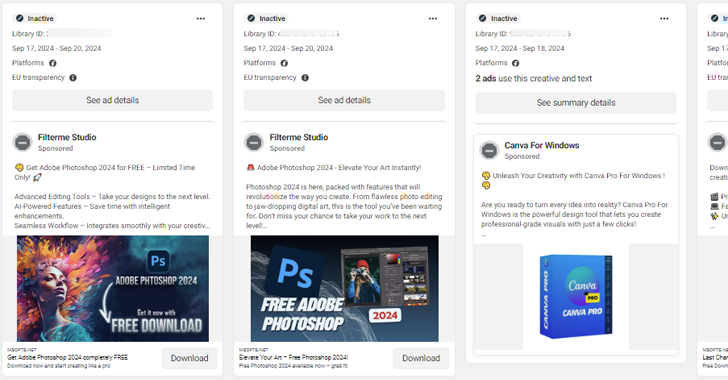
Cybersecurity researchers have uncovered an ongoing malvertising campaign that abuses Meta’s advertising platform and hijacked Facebook accounts to distribute information known as SYS01stealer. “The hackers behind the campaign use trusted brands to expand their reach,” Bitdefender Labs said in a report shared with The Hacker News. “The malvertising campaign leverages nearly a hundred malicious domains,…
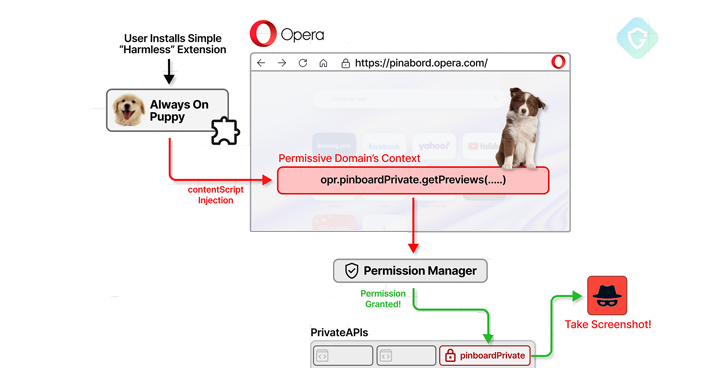
Read MoreOct 30, 2024Ravie Lakshmanan Browser Security / Vulnerability A now-patched security flaw in the Opera web browser could have enabled a malicious extension to gain unauthorized, full access to private APIs. The attack, codenamed CrossBarking, could have made it possible to conduct actions such as capturing screenshots, modifying browser settings, and account hijacking, Guardio Labs…
Read MoreChange Healthcare says it has notified approximately 100 million Americans that their personal, financial and healthcare records may have been stolen in a February 2024 ransomware attack that caused the largest ever known data breach of protected health information. Image: Tamer Tuncay, Shutterstock.com. A ransomware attack at Change Healthcare in the third week of February…
Read MoreThird-quarter revenue for Google Cloud climbed 35 percent from a year ago and ‘the overall opportunity is increasing as customers embrace GenAI,’ Google CEO Sundar Pichai said during the company’s quarterly call Tuesday. Google Cloud’s aggressive investments into enabling the adoption of AI infrastructure and GenAI capabilities are paying off as the tech giant is…
Read MoreOct 30, 2024The Hacker NewsVulnerability / Compliance Navigating the complexities of compliance frameworks like ISO 27001, SOC 2, or GDPR can be daunting. Luckily, Intruder simplifies the process by helping you address the key vulnerability management criteria these frameworks demand, making your compliance journey much smoother. Read on to understand how to meet the requirements…
Read MoreOct 30, 2024Ravie LakshmananCybercrim / Cryptocurrency Cybersecurity researchers have discovered a new malicious Python package that masquerades as a cryptocurrency trading tool but harbors functionality designed to steal sensitive data and drain assets from victims’ crypto wallets. The package, named “CryptoAITools,” is said to have been distributed via both Python Package Index (PyPI) and bogus…
Read More‘We are committed to equipping MSPs with the most advanced tools to protect their clients’ data,’ says SaaS Alerts CEO Jim Lippie. ‘Integrating SaaS Alerts into Kaseya 365 User means MSPs can now deliver advanced threat detection and response capabilities specifically tailored to the user and application level.’ Kaseya announced today that it bought cybersecurity…
Read MoreThe cybersecurity vendor says in a federal lawsuit over the July IT outage that it ‘certainly did not cause the harm that Delta claims.’ CrowdStrike has filed a lawsuit against Delta over the July IT outage that crippled the airline for days, formally accusing Delta of seeking to “shift blame” for its own failings to…
Read MoreIn an exclusive interview with CRN, Michael Green, general manager of Intel’s new North America partner scale group, says his top priorities are to grow the chipmaker’s business with partners and get his employees familiar with new roles as he pushes for greater efficiency within the semiconductor giant’s partner programs. After becoming Intel’s U.S. channel…
Read MoreCisco 360 represents a total revamp of the 30-year-old partner program and a significant departure in the way that Cisco partners earn today. Here’s what partners should know. Unveiled at Cisco Partner Summit 2024, the all-new Cisco 360 Partner Program is a total refresh of the tech giant’s nearly 30-year-old program. Unlike the programs of…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA