Category: Viral
5Critical 132Important 1Moderate 0Low Microsoft addresses 138 CVEs in its July 2024 Patch Tuesday release, with five critical vulnerabilities and three zero-day vulnerabilities, two of which were exploited in the wild. Microsoft released 138 CVEs in July 2024 Patch Tuesday release, with five rated critical, 132 rated important and one rated moderate. Our counts omitted…
Read MoreAWS is investing cloud credits worth hundreds of millions of dollars for AI startups as Google, Amazon and Microsoft all battle to win over the hottest startups in the world as customers. Amazon Web Services is putting the full-court press on Microsoft and Google by giving hundreds of millions of dollars’ worth of cloud credits…
Read MoreThe fallout from the cyberattacks targeting Snowflake customers including Ticketmaster and Neiman Marcus Group is reportedly still growing. The fallout from the cyberattacks targeting high-profile Snowflake customers is reportedly still growing, with an expanded impact claimed in two of the major incidents. Separate reports have indicated that the theft of data from Ticketmaster and Neiman…
Read MoreJohn Tavares tells CRN he plans to double down on channel partners as part of a growth push at the cloud security unicorn. Cloud security unicorn Orca Security announced Tuesday it has named Dell Technologies veteran John Tavares as its new channel chief, with an aim toward doubling down on partners as part of a…
Read MoreBased on user posts to Microsoft-owned social network LinkedIn, the cuts have hit a variety of managers, engineers and other job titles in Microsoft. Microsoft’s new fiscal year has started with a round of layoffs and some changes in its partner program, especially around requirements for specializations. Layoffs aren’t unusual for Microsoft this time of…
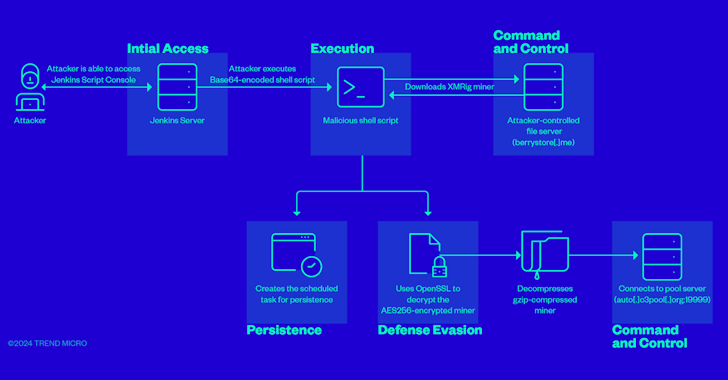
Read MoreJul 09, 2024NewsroomCI/CD Security / Server Security Cybersecurity researchers have found that it’s possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. “Misconfigurations such as improperly set up authentication mechanisms expose the ‘/script’ endpoint to attackers,” Trend Micro’s Shubham Singh and Sunil Bharti said in…
Read MoreClear Web vs. Deep Web vs. Dark Web Threat intelligence professionals divide the internet into three main components: Clear Web – Web assets that can be viewed through public search engines, including media, blogs, and other pages and sites. Deep Web – Websites and forums that are unindexed by search engines. For example, webmail, online…
Read MoreJul 09, 2024NewsroomSupply Chain Attack / Web Security Unknown threat actors have been found propagating trojanized versions of jQuery on npm, GitHub, and jsDelivr in what appears to be an instance of a “complex and persistent” supply chain attack. “This attack stands out due to the high variability across packages,” Phylum said in an analysis…
Read MorePeople’s Republic of China (PRC) Ministry of State Security APT40 Tradecraft in Action | CISA
by nlqip
This advisory, authored by the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), the United States Cybersecurity and Infrastructure Security Agency (CISA), the United States National Security Agency (NSA), the United States Federal Bureau of Investigation (FBI), the United Kingdom National Cyber Security Centre (NCSC-UK), the Canadian Centre for Cyber Security (CCCS), the New…
Read More‘Data centers have been built the way they have been built for the last 30 years. That isn’t going to get us to the next 30 years. That is going to have to change,’ Arthur Lewis, president of Dell’s Infrastructure Solutions Group, tells CRN. Arthur Lewis, president of Dell Technologies’ Infrastructure Solutions Group, said the…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm