Category: Viral
Dell Chief AI Officer Jeff Boudreau: ‘Right Now, There’s A Big Learning Curve, And That’s An Opportunity For Our Partner Community’
by nlqip
“It’s a community of practice. It’s just shared learnings. We’re all kind of going, ‘It’s early innings.’ We’re all bumping elbows and skinning knees. It’s like, ’Let’s learn together, share some of this pain, but share some of the learnings,” newly appointed Dell Chief AI Officer Jeff Boudreau tells CRN. Dell Technologies holds the No.…
Read MoreA threat actor ‘obtained certain personal information’ belonging to more than 60,000 customers and stored in the Snowflake platform, according to Neiman Marcus Group. Neiman Marcus Group confirmed Tuesday that it’s among the victims impacted by recent widespread cyberattacks targeting Snowflake customers, in an incident that saw data belonging to more than 60,000 customers potentially…
Read MoreHere’s a look at 10 data science and machine learning tools that solution and service providers should be aware of. Deep Thoughts Data science and machine learning technologies have long been important for data analytics tasks and predictive analytical software. But with the wave of artificial intelligence and generative AI development in 2023, the importance…
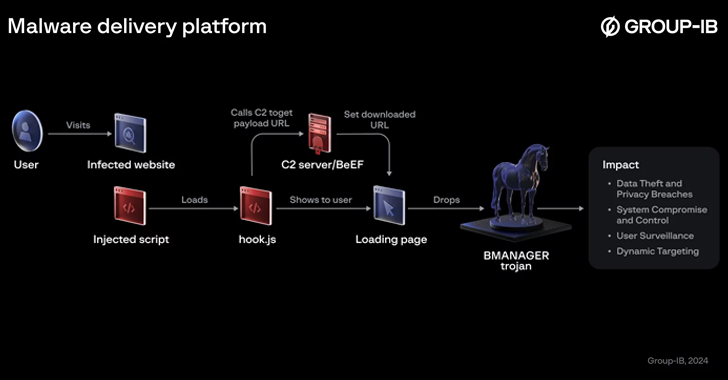
Read MoreJun 25, 2024NewsroomData Theft / Web Security A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. “The threat actor behind this campaign has been carrying out opportunistic SQL injection attacks against websites in various countries since at least 2022,” Group-IB researchers Rustam…
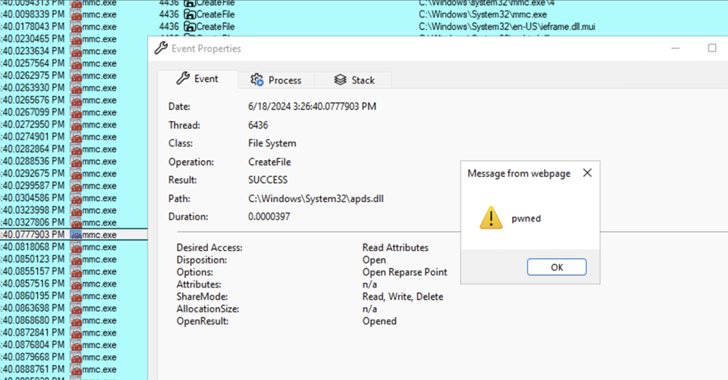
Read MoreJun 25, 2024NewsroomVulnerability / Threat Detection Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management Console (MMC) and evade security defenses. Elastic Security Labs has codenamed the approach GrimResource after identifying an artifact (“sccm-updater.msc“) that was…
Read MoreJun 25, 2024NewsroomWordPress / Web Security Multiple WordPress plugins have been backdoored to inject malicious code that makes it possible to create rogue administrator accounts with the aim of performing arbitrary actions. “The injected malware attempts to create a new administrative user account and then sends those details back to the attacker-controlled server,” Wordfence security…
Read More‘We’ve really focused on tools that MSPs need but also we’re looking at line of business horizontally,’ says Ryan Burton, vice president of marketplace vendor strategy for Pax8. ‘That is sales and marketing, finance, HR … things that go across customer segments.’ Five new vendors have hit Pax8’s marketplace just as the Denver-based distributor is…
Read MoreBy linking its AI monitoring tools – part of the New Relic Observability Platform – with Nvidia NIM, organizations can gain visibility into the “black box” operations of an AI application stack and improve AI operational performance and ROI. New Relic has integrated its observability software with Nvidia’s NIM inference microservices, making it possible to…
Read MoreThe maker of software used by thousands of car dealerships has reportedly been in negotiations with threat actors over a ransom payment worth tens of millions of dollars. CDK Global has begun to restore its systems and has been in negotiations with threat actors over a ransom payment, purportedly worth tens of millions of dollars,…
Read MoreJun 24, 2024NewsroomVulnerability / Artificial Intelligence Google has developed a new framework called Project Naptime that it says enables a large language model (LLM) to carry out vulnerability research with an aim to improve automated discovery approaches. “The Naptime architecture is centered around the interaction between an AI agent and a target codebase,” Google Project…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm