Category: Viral
‘As enterprises go through their normal storage refresh, they should be able to uplevel it so instead of having to build specialized environments for AI, they’re able to have their workload data, their existing data that’s sitting in existing environments, accessible for analytics and AI,’ Pure Storage CEO Charles Giancarlo tells CRN. At its recently…
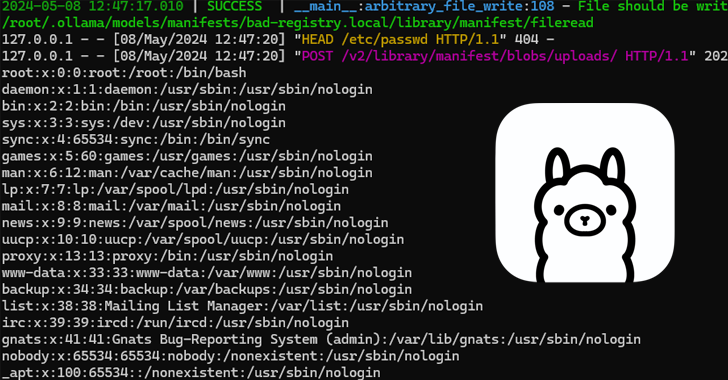
Read MoreJun 24, 2024NewsroomArtificial Intelligence / Cloud Security Cybersecurity researchers have detailed a now-patch security flaw affecting the Ollama open-source artificial intelligence (AI) infrastructure platform that could be exploited to achieve remote code execution. Tracked as CVE-2024-37032, the vulnerability has been codenamed Probllama by cloud security firm Wiz. Following responsible disclosure on May 5, 2024, the…
Read MoreFrom Amazon Q Business and AI Agents to new cloud storage and Amazon Bedrock tools, here are the 10 coolest new AWS products launched in 2024 so far. From its new Amazon Q Developer and Business products to new cloud storage and Amazon Bedrock offerings, Amazon Web Services’ product innovation engine has been on fire…
Read MoreJun 24, 2024The Hacker NewsThreat Intelligence / Cybersecurity Learn about critical threats that can impact your organization and the bad actors behind them from Cybersixgill’s threat experts. Each story shines a light on underground activities, the threat actors involved, and why you should care, along with what you can do to mitigate risk. Cybersecurity professionals…
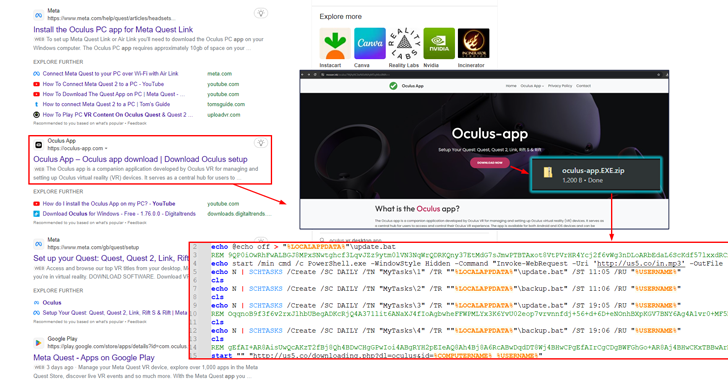
Read MoreJun 22, 2024NewsroomPhishing Attack / Adware A new campaign is tricking users searching for the Meta Quest (formerly Oculus) application for Windows into downloading a new adware family called AdsExhaust. “The adware is capable of exfiltrating screenshots from infected devices and interacting with browsers using simulated keystrokes,” cybersecurity firm eSentire said in an analysis, adding…
Read MoreVideo Understanding and preparing for the potential long-tail costs of data breaches is crucial for businesses that aim to mitigate the impact of security incidents 21 Jun 2024 A successful cyberattack can affect an organization in many ways, but the way the organization handles the incident extends far beyond the immediate aftermath. Indeed, the long-term…
Read MoreThe U.S. did not sanction CEO and founder Eugene Kaspersky. The United States has blocked members of Russia-based cybersecurity vendor Kaspersky’s leadership from making transactions in the country a day after banning the company from making sales in the U.S. Twelve individuals associated with Kaspersky have been designated to the Specially Designated Nationals (SDN) list…
Read MoreIn an interview with CRN, Insight Enterprises executive Megan Amdahl says there are multiple tailwinds for AI PC adoption, including potential productivity gains, an aging fleet of hastily obtained 2020-era PCs and Microsoft’s plan to stop supporting Windows 10 in 2025. What will motivate businesses to buy the growing wave of AI PCs hitting the…
Read MoreChange Healthcare: Patient Data Exposed In Breach Includes Medical Diagnoses, Test Results, Prescriptions
by nlqip
The medical data exposed in the cyberattack earlier this year may have included ‘diagnoses, medicines, test results, images, care and treatment,’ according to Change Healthcare. Change Healthcare disclosed that it now believes sensitive patient medical data was exposed in the widely felt cyberattack earlier this year, as the UnitedHealth-owned company said it is preparing to…
Read MoreA pair of cyberattacks against software maker CDK continues to impact thousands of car dealerships and has spurred threat actors to launch impersonation attacks. The CDK Global outage affecting thousands of car dealerships continued Friday, while the attempts to recover from cyberattacks earlier this week were compounded by reported impersonation scams targeting dealership staff. While…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm