Category: Viral
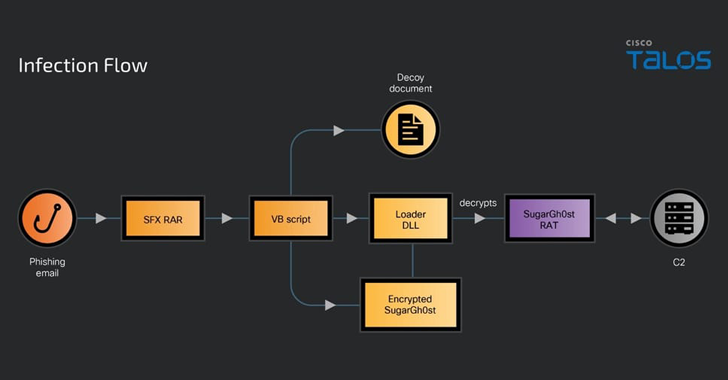
Jun 21, 2024NewsroomMalware / Threat Intelligence A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage campaign primarily targeting government entities across Asia and EMEA (Europe, Middle East, and Africa) with SugarGh0st malware since at least August 2023. “SneakyChef uses lures that are scanned documents of government agencies, most of which…
Read MoreGenAI has remained a top focus for cybersecurity vendors recently during the first half of the year, but plenty of other new products—including in SIEM, SASE and XDR—have debuted during the first half of the year. The list of cybersecurity tools utilizing generative AI continued to balloon during the first half of the year, including…
Read MoreJun 21, 2024NewsroomPhishing Attack / Email Security Cybersecurity researchers have shed light on a new phishing campaign that has been identified as targeting people in Pakistan using a custom backdoor. Dubbed PHANTOM#SPIKE by Securonix, the unknown threat actors behind the activity have leveraged military-related phishing documents to activate the infection sequence. “While there are many…
Read MoreSlalom’s Chris Thomas explains the growing artificial intelligence use cases for its AI-powered robotic dog named Spot. The use cases for Slalom’s AI-powered robotic dog, Spot, are growing at a rapid pace thanks to Google’s Gemini AI and edge computing innovation. At Google Cloud Next 2024, Spot could be seen walking around and in between…
Read MoreJun 21, 2024NewsroomMalware / Malvertising A malvertising campaign is leveraging trojanized installers for popular software such as Google Chrome and Microsoft Teams to drop a backdoor called Oyster (aka Broomstick and CleanUpLoader). That’s according to findings from Rapid7, which identified lookalike websites hosting the malicious payloads that users are redirected to after searching for them…
Read MoreDigital Security As health data continues to be a prized target for hackers, here’s how to minimize the fallout from a breach impacting your own health records 20 Jun 2024 • , 5 min. read Digital transformation is helping healthcare providers across the globe to become more cost-efficient, while improving standards of patient care. But…
Read MoreStarting midnight July 20, Kaspersky is barred “from entering into any new agreement with U.S. persons involving one or more” information and communications technology and services deals. The United States has taken steps to ban domestic sales and integration of products by Russia-based cybersecurity vendor Kaspersky, citing “undue and unacceptable risks to U.S. national security…
Read MoreThe provider of software used by thousands of car dealerships reportedly says it has shut down most of its systems after a pair of attacks. CDK Global, a provider of software used by thousands of car dealerships, has reportedly shut down most of its systems after a pair of cyberattacks in recent days. The first…
Read MoreTD Synnex CEO Rich Hume, who led Tech Data through the pandemic and the acquisition of rival Synnex, will retire Sept. 1. TD Synnex COO Patrick Zammit will take over. TD Synnex CEO Rich Hume, who led the company through six transformative years of massive growth through acquisition as well as running one of the…
Read MoreIn an interview with CRN, AMD executive Forrest Norrod talks about how the company is “dramatically” increasing investments in its Instinct data center GPUs to compete with Nvidia and when it plans to make a greater focus on enabling channel partners to sell Instinct-based systems for AI workloads. AMD’s top data center executive said the…
Read MoreRecent Posts
- CISA Releases Four Industrial Control Systems Advisories | CISA
- CISA and US and International Partners Publish Guidance on Priority Considerations in Product Selection for OT Owners and Operators | CISA
- Broadcom Names New Channel Chief, Sales Leader: 5 Big Things To Know
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.