Category: Viral
‘You talk about a person that goes in and just adds energy and life to all the conferences and is always helping the channel, that was Bob. … He was willing to go beyond to make sure that people were engaged. I think everybody needs that kind spokesperson to lead their communities,’ said Paul Benson,…
Read More‘The foundation of our program was hardware and transaction. That’s who we were as a company at the time and that served us well … but what it rewarded was a partner who transacts, and the way that we do business today is quite different. It’s the first material shift in how we evaluate partners…
Read MoreThe cybersecurity vendor is reportedly once again exploring its options for being acquired. Cybersecurity vendor Rapid7 is reportedly exploring its options for being acquired by private equity investors for the second time in two years. According to a Reuters report Monday, publicly traded Rapid7 is in “early” discussions about a potential acquisition deal with several…
Read MoreDelta is seeking unspecified damages in connection with the CrowdStrike-caused IT outage in July, which cost the airline more than $500 million in out-of-pocket losses, according to the complaint. Delta is seeking significant damages from CrowdStrike in connection with the July IT outage caused by the cybersecurity vendor, which cost the airline more than $500…
Read MoreGenerative AI, copilots, agents, cybersecurity and PCs are among the many topics expected to come up. An update on Microsoft’s suite of artificial intelligence offerings, including copilots and agents. Growth in Teams and the productivity application suite. And early signs of an AI PC revolution. These are some of the subjects expected to come up…
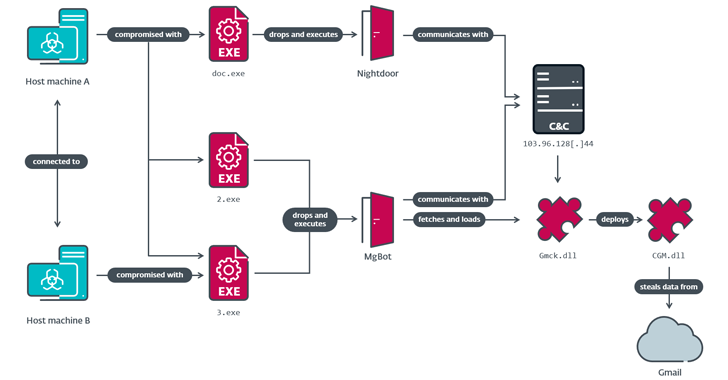
Read MoreOct 28, 2024Ravie LakshmananCloud Security / Cyber Attack A government entity and a religious organization in Taiwan were the target of a China-linked threat actor known as Evasive Panda that infected them with a previously undocumented post-compromise toolset codenamed CloudScout. “The CloudScout toolset is capable of retrieving data from various cloud services by leveraging stolen…
Read MoreOct 28, 2024Ravie LakshmananMalware / Threat Intelligence Three malicious packages published to the npm registry in September 2024 have been found to contain a known malware called BeaverTail, a JavaScript downloader and information stealer linked to an ongoing North Korean campaign tracked as Contagious Interview. The Datadog Security Research team is monitoring the activity under…
Read MoreOct 28, 2024Ravie LakshmananCyber Espionage / Android A suspected Russian hybrid espionage and influence operation has been observed delivering a mix of Windows and Android malware to target the Ukrainian military under the Telegram persona Civil Defense. Google’s Threat Analysis Group (TAG) and Mandiant are tracking the activity under the name UNC5812. The threat group,…
Read MoreIn an interview with CRN, HP Inc. Global Channel Chief Kobi Elbaz says the investments the PC and print giant has made into its three-year-old Amplify partner program will allow the company to ‘double down’ on hybrid AI solutions with partners, which include new AI PCs. HP Inc. Global Channel Chief Kobi Elbaz said selling…
Read MoreIn an interview with CRN, Rubrik CEO Bipul Sinha discusses data security in the GenAI era and why ‘nobody else from our space is even daring’ to go public. The well-known data security challenges posed by the arrival of generative AI have accelerated the already strong growth opportunities at Rubrik, which is positioned at the…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA